What is a Potentially Unwanted Modification (PUM)?
A PUM (for Potentially Unwanted Modification) is a sensitive modification made by a program which can be malware or legit, or even made by the user. Such detection is triggered depending on what is modified.
Several examples
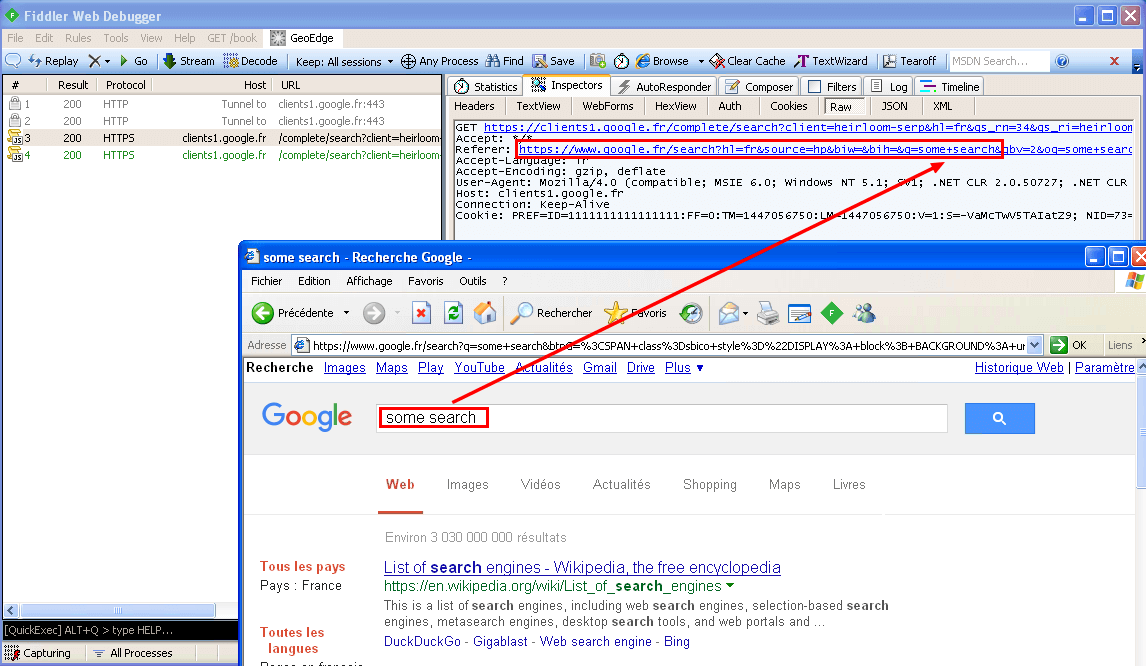
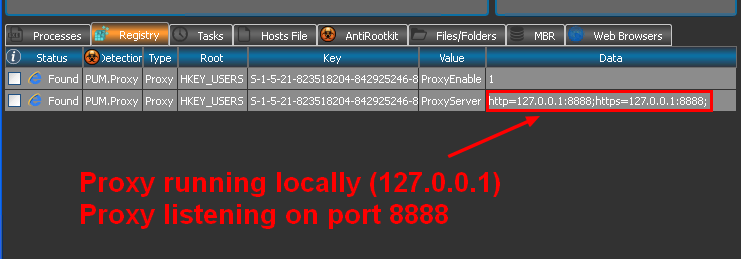
PUM.Proxy: A proxy is a program running either locally (on your machine) or on a remote machine (server) that acts as a web filter. It’s able to read, decode and filter all your internet traffic and bounce some requests based on rules. In an enterprise context, proxies are used to protect endpoints or deny some websites at work (Facebook, …). At home, most of the time these proxies are malicious.
Malware use proxies to deny access to help forums, or download websites (they don’t want you to be able to disinfect your machine). They are also used to retrieve information regarding your internet habits, and inject ads or redirect to malicious websites. What you need to know basically is that a proxy can read and modify all internet traffic that passes through it.
The following example is made with a LEGIT program, fiddler. It demonstrates what a proxy can do (running locally).
RogueKiller detects the PUM like this:
PUM.DNS: A DNS is a server that translates host names (ex: google.com) into an IP address (ex: 216:58.192.14). Usually, a good DNS configuration points to your ISP’s DNS server, or to third party DNS servers like OpenDNS or Google DNS. However, some malware can change that configuration (it’s a registry key) to point to a malicious DNS server, that will return wrong IP addresses and force you to go on malicious websites (ex: you type google.com and malicious DNS returns you the address of a server that looks like Google but serves malicious things).
Should I remove?
By default, PUMs are considered in-between malware and safe. RogueKiller cannot decide by itself if it’s malicious or not, just point that it exists. It’s done this way because sometimes the modification is wanted and has been setup by user itself or by machine’s administrator (in enterprise).
To answer the question, it’s up to you. If you’re at home, you probably want to remove them.
However, you need to know it’s SAFE TO REMOVE and won’t break your computer, PUMs are not critical.
Removal
Scan your computer with RogueKiller and remove detected PUM values.