EDIT 11/21/2014:
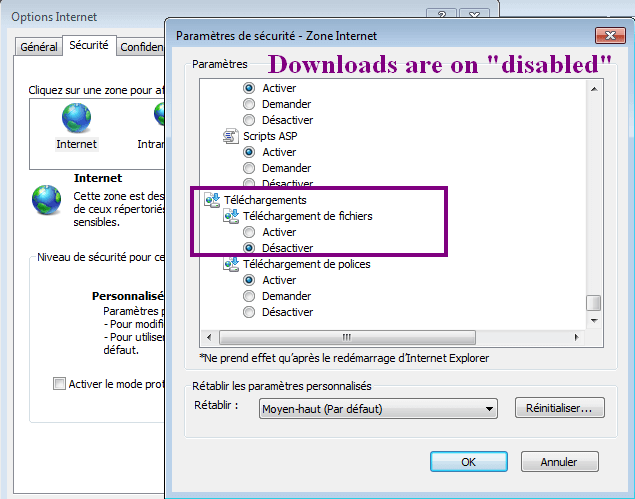
This new variant disallows file downloads on Internet Explorer. To re-enable them (and download RogueKiller), you need to go in “Tools”, “Internet Settings”, then in the “Security” tab. Click on “Reset all areas to the default level” et validate. Downloads are back.
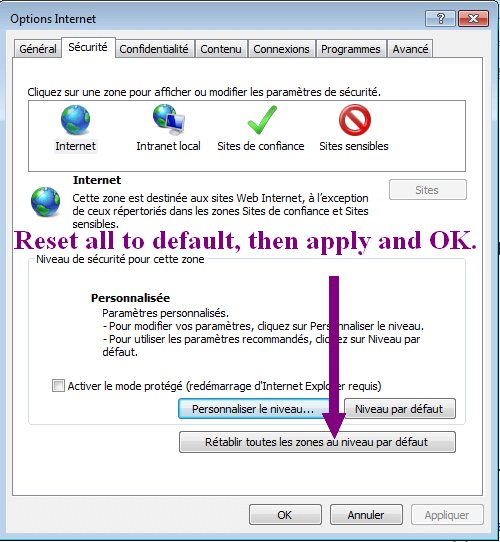
EDIT 10/10/2014:
If you have difficulties to remove that threat, try this:
- 1- Do a scan with RogueKiller. Do not close the window.
- 2- Kill all dllhost.exe processes (for example with Process Explorer, kill tree)
- 2.1- If you can’t kill them all, some reported it’s easier to do after a reboot in Safe Mode
- 3- Do the removal with RogueKiller
- 4- Reboot immediately
There’s also a forum thread speaking about that.
Poweliks has a new variant: Now there’s no more RUN key, only a CLSID hijack in HKEY_LOCAL_MACHINE\Software\classes\clsid\{73E709EA-5D93-4B2E-BBB0-99B7938DA9E4}\LocalServer32:
Your reports should look like this (with your own language text):
¤¤¤ Processus malicieux : 1 ¤¤¤
[Tr.Poweliks] dllhost.exe -- C:\WINDOWS\system32\dllhost.exe[7] -> TUÉ [TermProc]
¤¤¤ Entrées de registre : 5 ¤¤¤
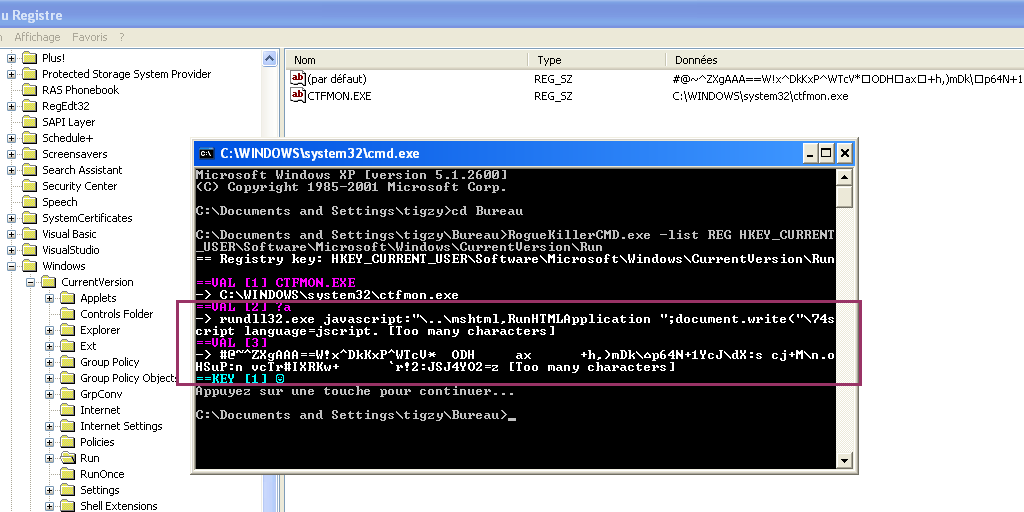
[Tr.Poweliks] HKEY_CLASSES_ROOT\CLSID\{73E709EA-5D93-4B2E-BBB0-99B7938DA9E4}\LocalServer32 | (default) : rundll32.exe javascript:"\..\mshtml,RunHTMLApplication [7][x] -> REMPLACÉ (%systemroot%\system32\wbem\wmiprvse.exe)
[Tr.Poweliks] HKEY_LOCAL_MACHINE\Software\classes\clsid\{73E709EA-5D93-4B2E-BBB0-99B7938DA9E4}\LocalServer32 | a : -> SUPPRIMÉ
[Tr.Poweliks] HKEY_LOCAL_MACHINE\Software\classes\clsid\{73E709EA-5D93-4B2E-BBB0-99B7938DA9E4}\LocalServer32\? -> SUPPRIMÉ
Analysis
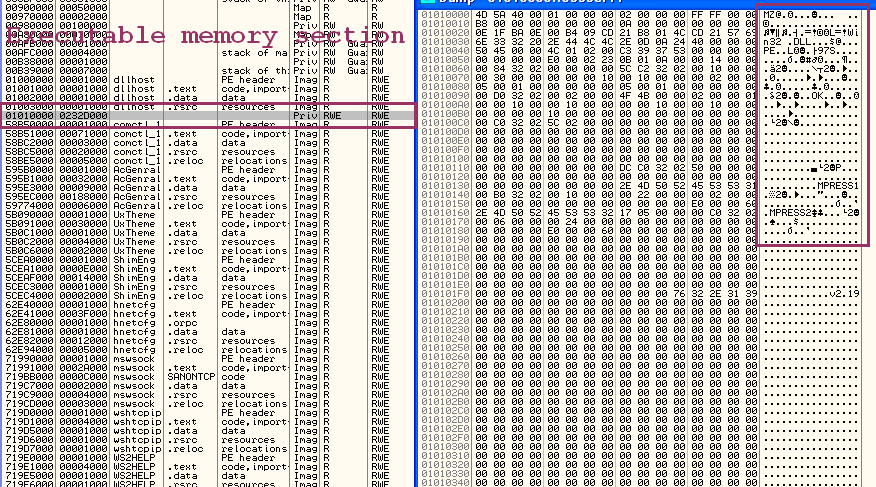
Poweliks is a malware with rootkit-like features, with no file (directly passing from registry to memory at boot time). The payload (malware file) is stored in an encrypted registry value, and loaded at boot time by a RUN key calling rundll32 process on an encrypted javascript payload.
Once payload loaded in rundll32, it tries to execute an embedded powershell script in interactive mode (no UI). That powershell scripts contains a base64-encoded payload (another one) which will be injected into a dllhost process (the persistent item), which will be zombified and act as a trojan downloader for other infections.
The dllhost injected thread is also responsible for protecting the registry value (persistence item) by recreating it when removed. This is why it’s necessary to shutdown the process first.
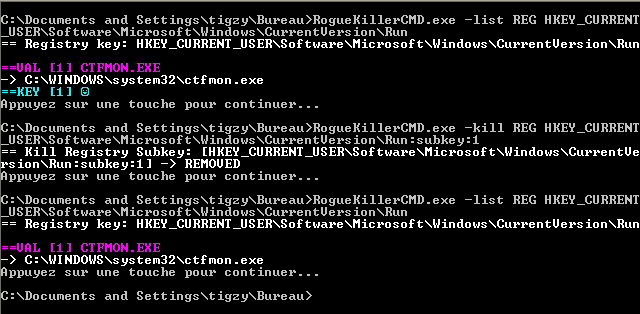
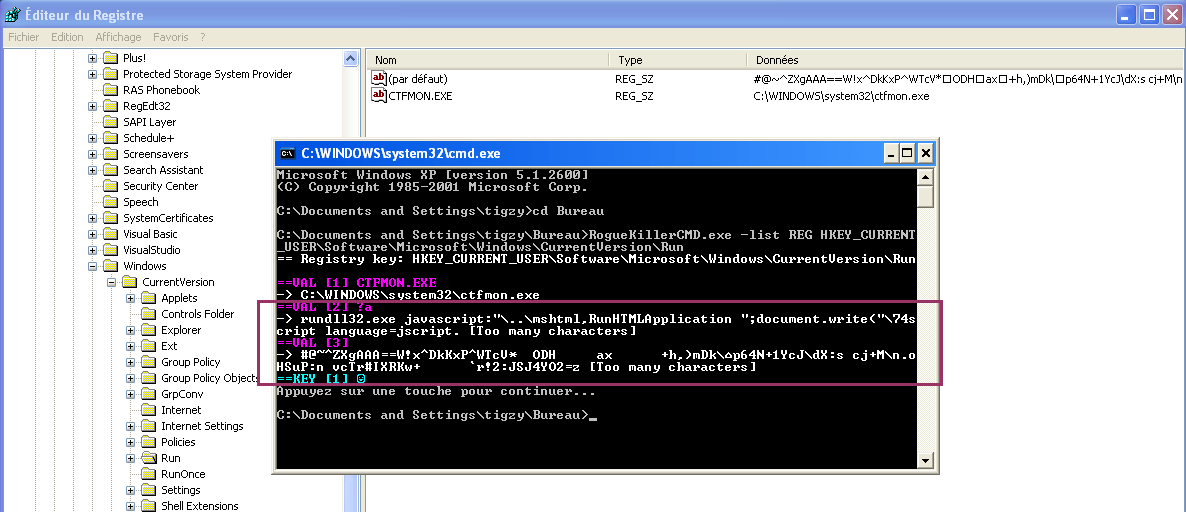
The registry value/subkey is located in HKEY_CURRENT_USER/../Run, and uses Win32API-fool trick, previously seen in ZeroAccess trojan. Value name and Subkey name are injected with unicode characters, so that the high level API cannot read them, and remove them.
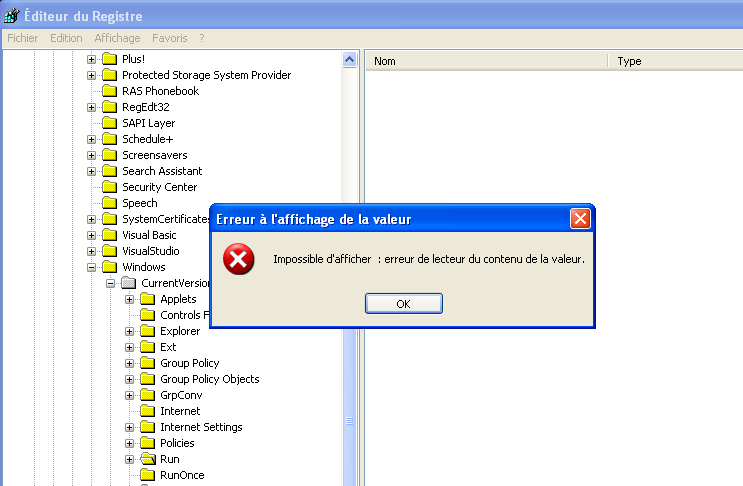
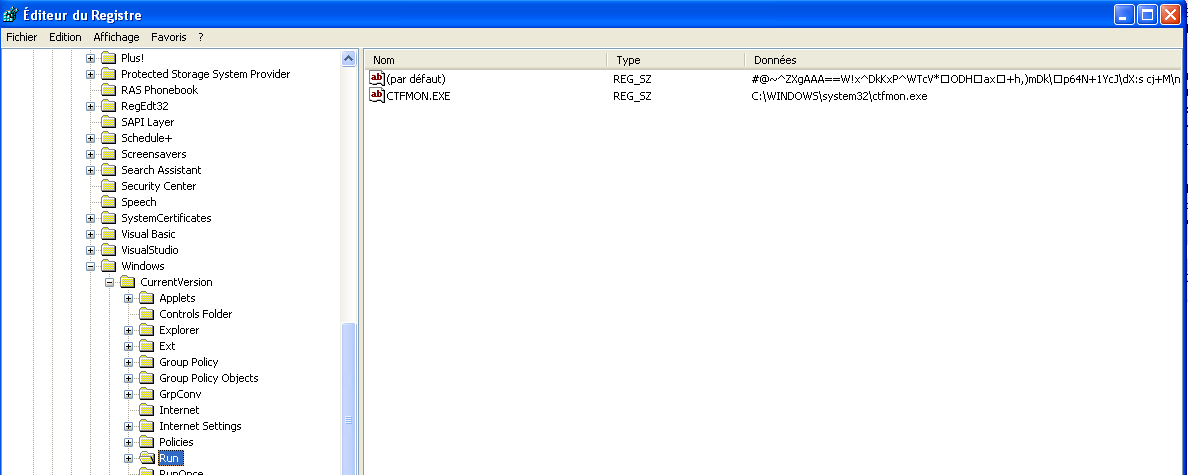
However, both RogueKiller and RogueKillerCMD are able to see them and neutralize them.
For deep analysis, please refer to that excellent post.
Removal
Starting with release 9.2.5, RogueKiller is able to automatically remove that trojan, and RogueKillerCMD is able to remove it manually. Simply scan your computer and remove infected keys.
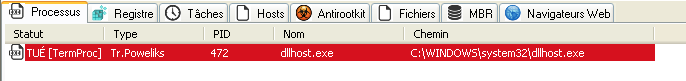
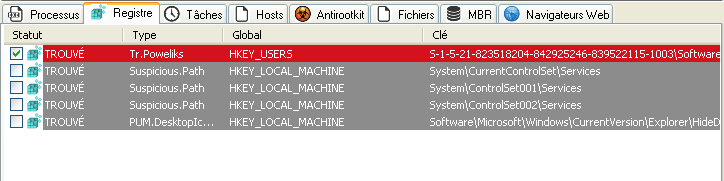
Your reports should look like this (with your own language text):
¤¤¤ Processus malicieux : 1 ¤¤¤
[Tr.Poweliks] dllhost.exe -- C:\WINDOWS\system32\dllhost.exe[7] -> TUÉ [TermProc]
¤¤¤ Entrées de registre : 5 ¤¤¤
[Tr.Poweliks] HKEY_USERS\S-1-5-21-823518204-842925246-839522115-1003\Software\Microsoft\Windows\CurrentVersion\Run | ?a : rundll32.exe javascript:"\..\mshtml,RunHTMLApplication -> SUPPRIMÉ
To complete the cleanup, you can also remove (optional) the payload key value, and the subkey with RogueKillerCMD.