Since a few weeks, new waves of infection related to the use of hacktools like Windows Loader or KMSPico caught our attention (KMS Activators). Since they are more used than before some malware authors now use them to disseminate infections.
KMS ACTIVATORS: BYPASSING ACTIVATION
With the release of Windows 10, illegal MAK and SLP activations became really difficult to perform and thus, available hacktools now use KMS.
Key Management Service (KMS) is used to activate Microsoft products on clients using generic keys against a Volume Activation Service, hosted on a remote server. Legally owned volume licenses are installed on the server and activation is required typically every 180 days to keep the products activated on client machines.
For more information, please refer to the Understanding KMS article by Microsoft.
Hacktools using KMS activation emulate a fake KMS server on the local computer and trick Microsoft products to activate against it. Products activated this way have temporary valid license and when installing such hacktools, a task is often created to automatically renew it every 60 days.
WHY NOT USING THEM?
Aside for the ethical point of view and TOS breaking, using hacktools may put your computer at risk. Even if some of them are perfectly functional and malware-free, that’s not a generality.
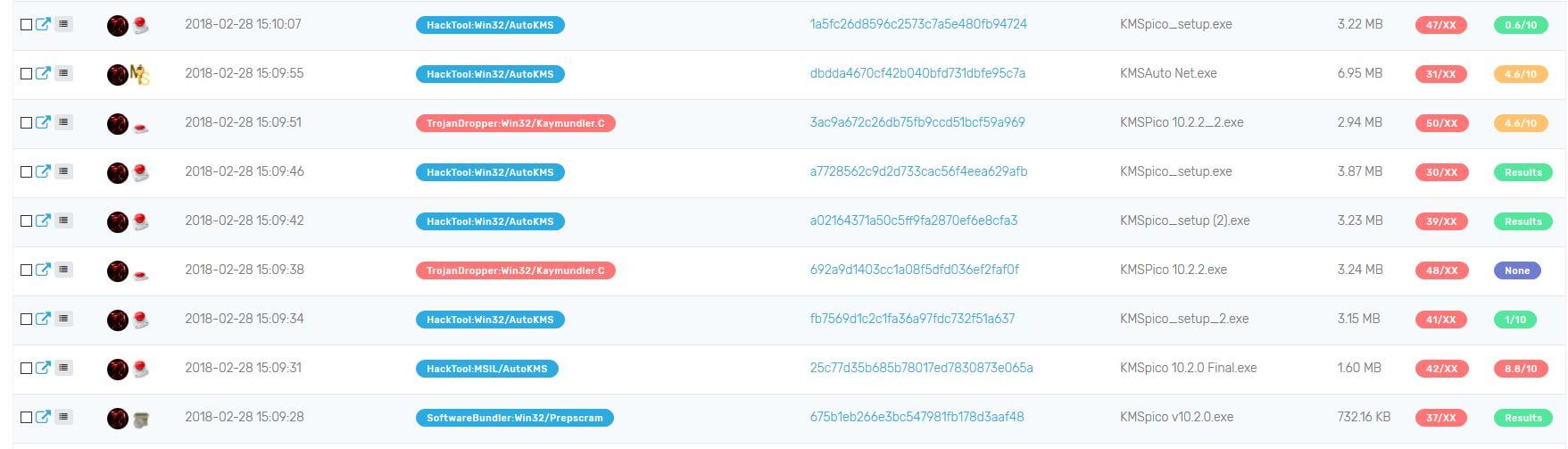
We have tested the first KMS activators returned by Google search engine and analyzed them. Here are the results :
Most of them are highly detected on VirusTotal, and a lot of them have suspicious activity in sandbox analysis.
Sample #1 : DBDDA4670CF42B040BFD731DBFE95C7A
| Interesting characteristics | Suspicious/Malicious activities |
| Check for debugger and virtual environment Signed using an unrecognized root certificate | None (program crashed) |
Sample #2 – 692A9D1403CC1A08F5DFD036EF2FAF0F
| Interesting characteristics | Suspicious/Malicious activities |
| Check for debugger | Install a backdoor allowing remote access Browser redirections and adclickers Monero cryptomining |
Sample #3 – 3AC9A672C26DB75FB9CCD51BCF59A969
| Interesting characteristics | Suspicious/Malicious activities |
| Check for debugger | Browser redirections and adclickers Monero cryptomining |
Sample #4 – 675B1EB266E3BC547981FB178D3AAF48
| Interesting characteristics | Suspicious/Malicious activities |
| Check for debugger and virtual environment | Open a backdoor allowing remote access |
Sample #5 – A02164371A50C5FF9FA2870EF6E8CFA3
| Interesting characteristics | Suspicious/Malicious activities |
| Signed using an unrecognized root certificate | None |
Sample #6 – A7728562C9D2D733CAC56F4EEA629AFB
| Interesting characteristics | Suspicious/Malicious activities |
| Signed using an unrecognized root certificate | Change security-related services and parameters |
Sample #7 – FB7569D1C2C1FA36A97FDC732F51A637
| Interesting characteristics | Suspicious/Malicious activities |
| Check for debugger and virtual environment Signed using an invalid certificate | Contact remote machine |
Sample #8 – 1A5FC26D8596C2573C7A5E480FB94724
| Interesting characteristics | Suspicious/Malicious activities |
| Check for virtual environment Signed using an unrecognized root certificate | Contact remote machine |
Sample #9 – 25C77D35B685B78017ED7830873E065A
| Interesting characteristics | Suspicious/Malicious activities |
| Check for virtual environment | None |
DETECTION & REMOVAL
In case you have installed one of these malware variants of KMSpico, and want to make sure they are not doing harmful actions to your machine, can you try to run a scan with RogueKiller Anti-Malware and remove all detections.
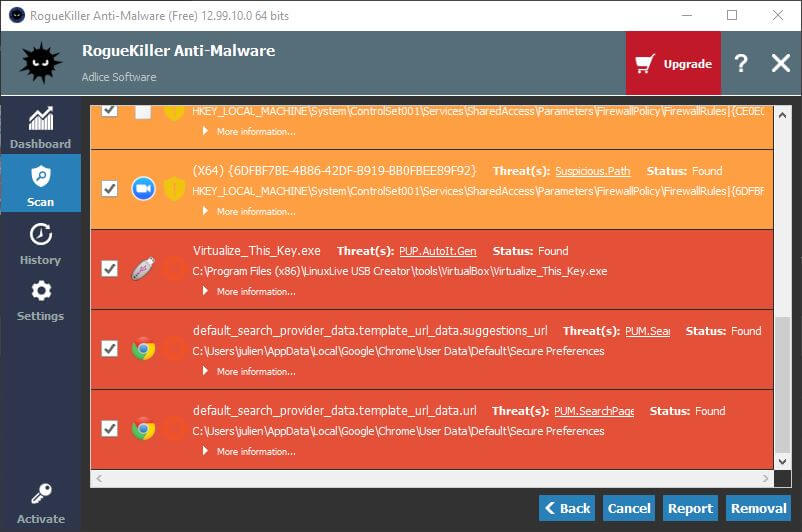
CONCLUSION
Some worked as advertised, some crashed on startup or failed to successfully activate Windows. But some included malicious code that would have allowed attackers to access your computer system and data if you happened to run them.
So, even if it is tempting to use such tools to save money, the financial loss resulting of identity or data theft could be much more expensive than the amount to be paid to buy a legal Microsoft license.