A few weeks ago you may have seen a new scanner option available in RogueKiller, called WMI Scanner. This new scanner has been added after a few malware started to put themselves into what is called the Windows Management Instrumentation (WMI) database, which is a Microsoft version of the WBEM standard.
Windows Management Instrumentation (WMI)
WMI is explained here by Microsoft. This is a database model following the WBEM standard, aiming to standardize the way objects are stored in an enterprise (but not only) environment. You can see it as a big database where software can communicate, store information and call each other. Object model is composed of namespaces, classes and class instances.
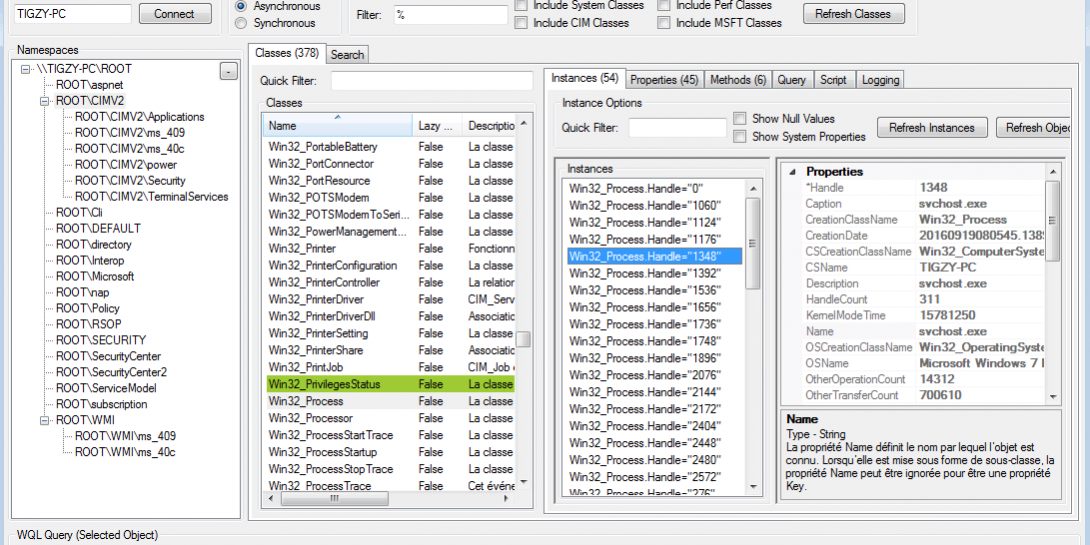
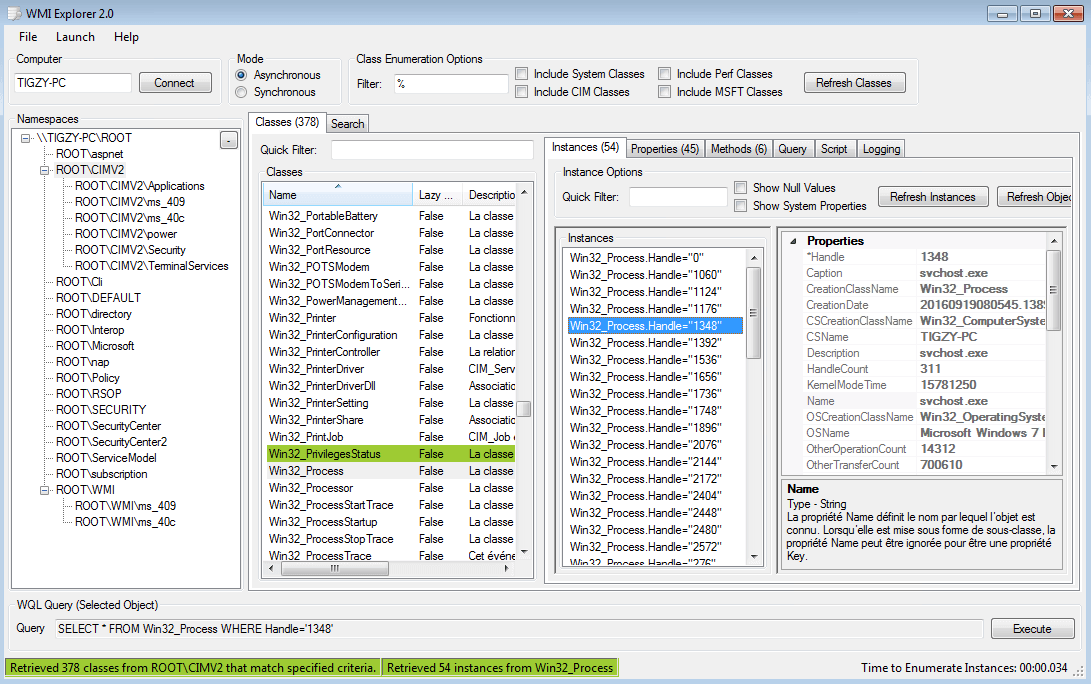
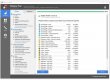
There are a bunch of tools to play with the WMI database, one of the best is called WMI Explorer, that you can download here. For example, this is how we can get the processes list with WMI Explorer:
WMI Malware
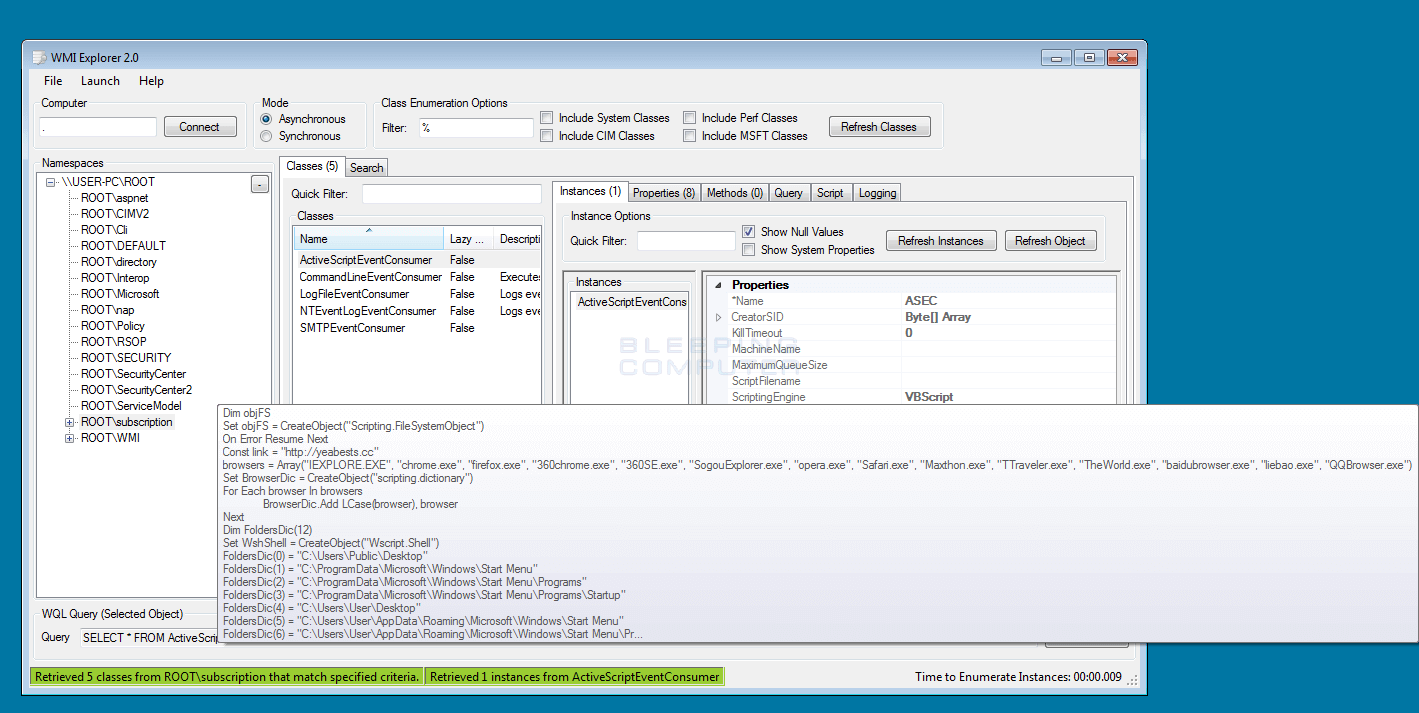
Some adware has been seen using the WMI database to store its payload (or malicious code) as well as its persistence item, to make it harder to detect and remove. The adware Yeabests uses ActiveScriptEventConsumer class to reinfect all desktop shortcuts in order to trigger the infection on web browser launch.
ActiveScriptEventConsumer is a special WMI class that can run code on a periodic time (like a scheduled task). Since it’s not well known and hidden in the WMI database, no anti-malware was detecting it before that.
RogueKiller, Inside WMI Scanner
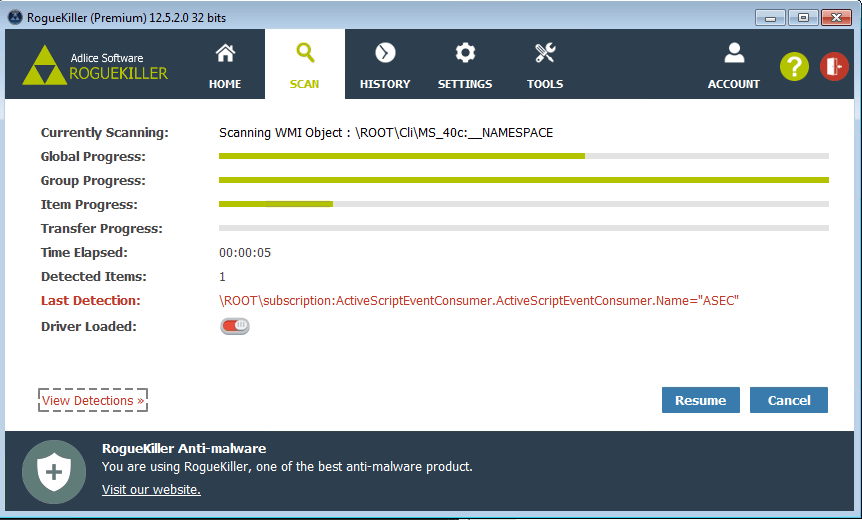
RogueKiller now implements a WMI Scanner, that iterates and scan each namespace, class and instance for malicious activity. As soon as it’s in the database, the malware will then be removed from the WMI database.