EDIT October, 4th 2014
If the only process detected is your Antivirus, please ignore the detection.
We are working on this issue, which is not really a bug, but a problem of signature scanner definition VS Antivirus definition.
Some Antivirus scanners load their signature database in clear in memory, and when RogueKiller has the same signature as the AV for a particular malware (this is the case for Zeus), it will find it in the Antivirus memory. The workaround will be to safely whitelist all antiviruses process, and never scan them for signatures, which will be in next release.
In clear: If ONLY your antivirus is detected, ignore it. If more processes are infected (like explorer.exe, etc…) then you’re probably infected.
Analysis
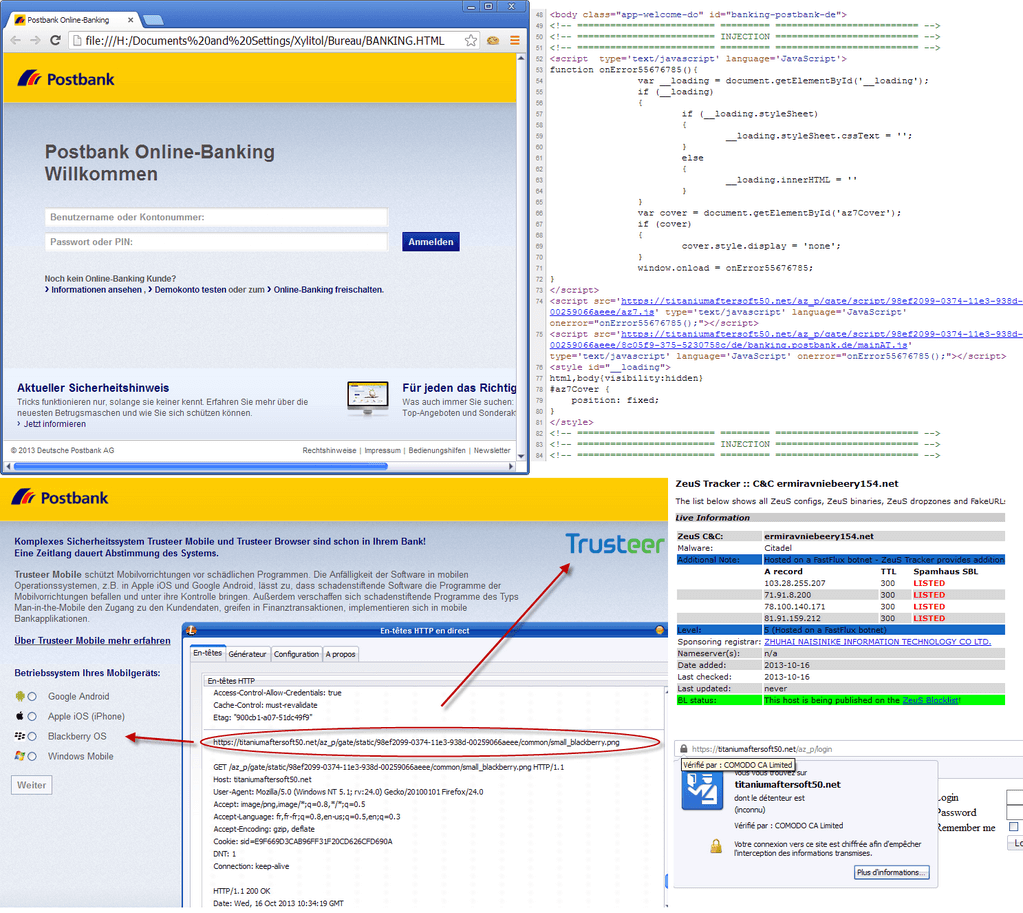
Zeus is a malware with banking/stealer features. The payload (malware file) is injected into several legit processes, even maybe in your antivirus, and loaded at boot time by a RUN key calling the injector. The Malware is injected into some legit processes (including explorer.exe) within an executable section, outside of any module. It can be found by looking at the sections with E/X rights, but with no physical DLL.
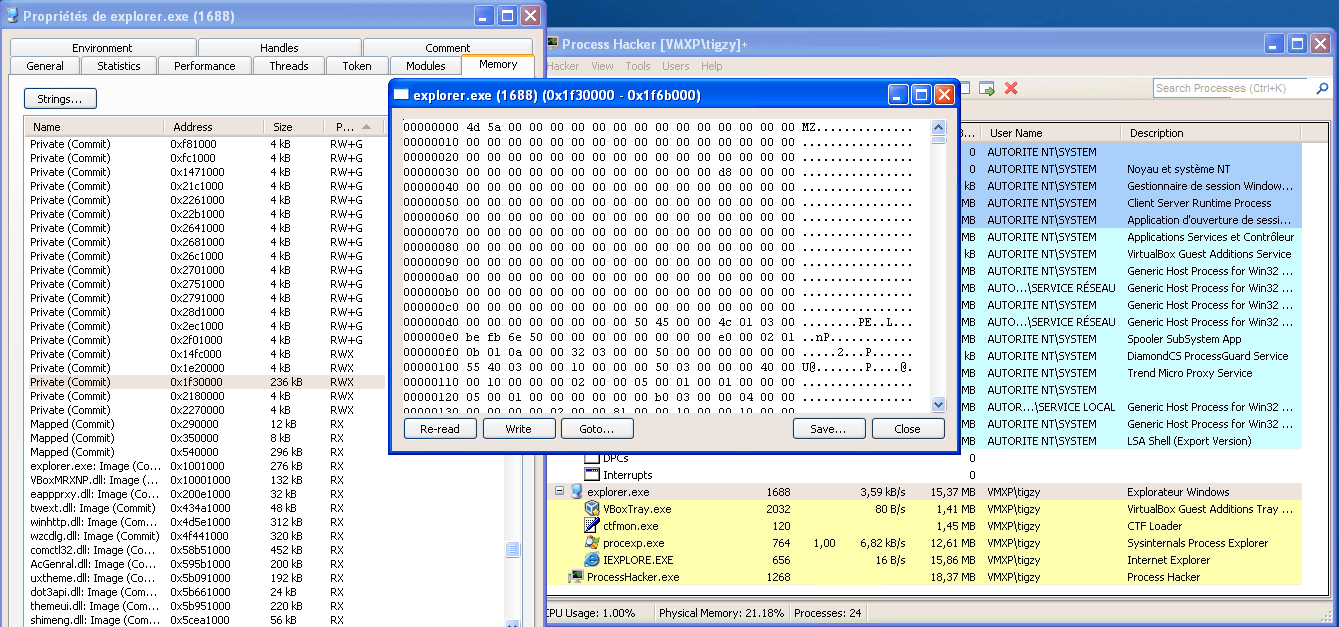
Once payload loaded in into a process, it behaves differently according to the name of the process. For a lambda process, it will hook several APIs, to monitor process creation and module loading. When a new process is loaded it attempts to inject it too, so that it becomes really hard to clean the memory.
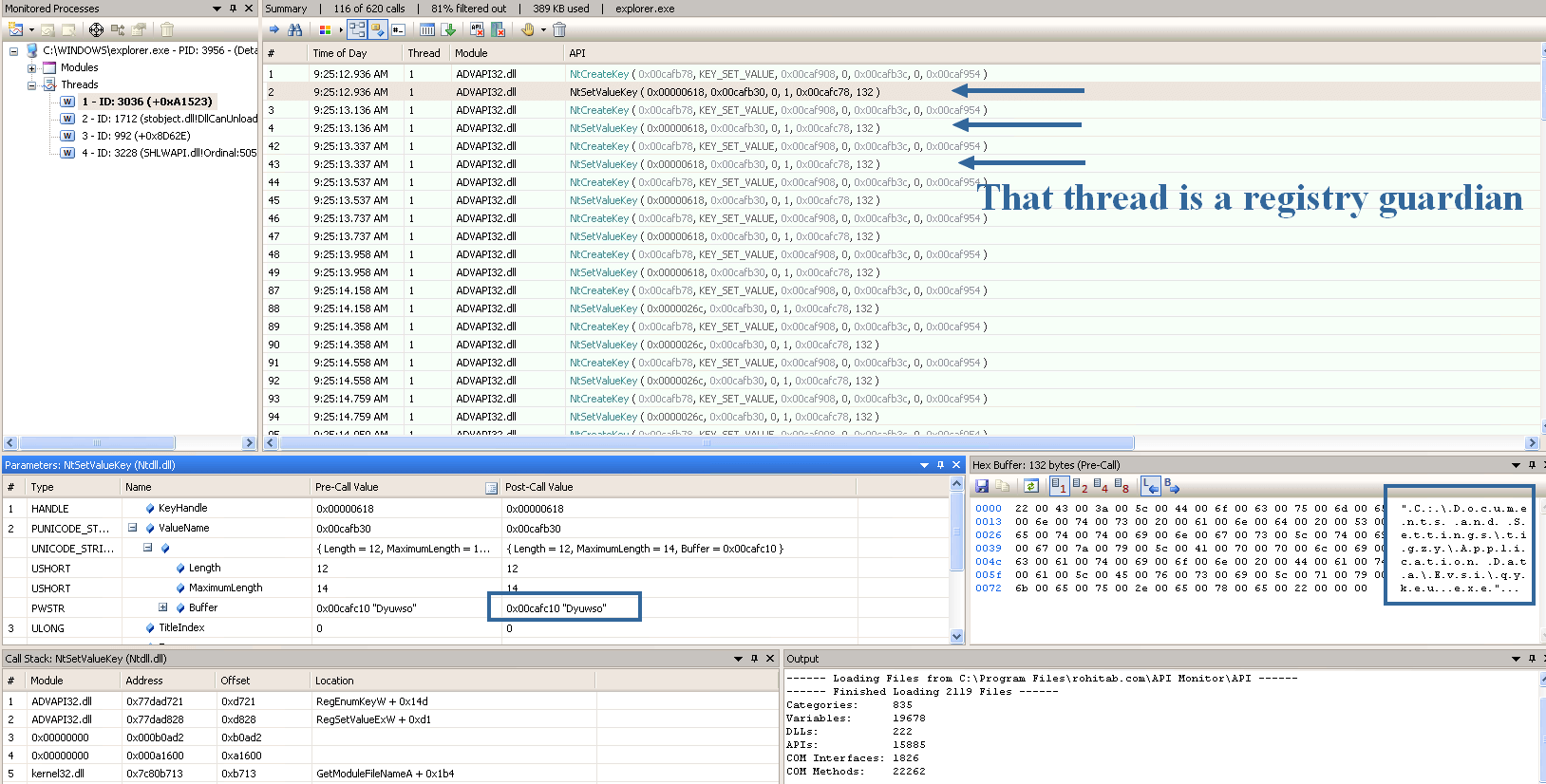
It also starts a watchdog thread that will rewrite the RUN value every 200ms. It becomes now really hard to remove it from the startup.
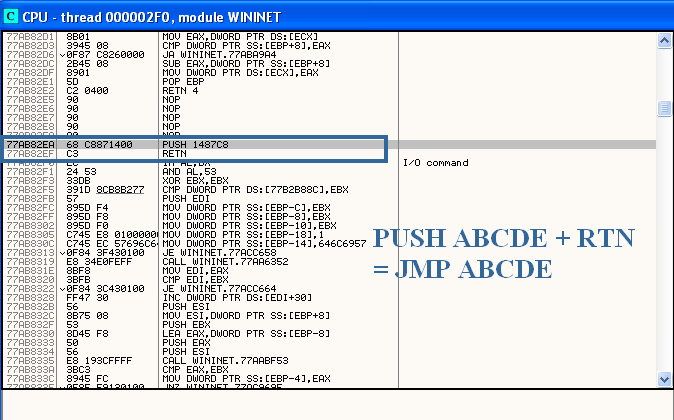
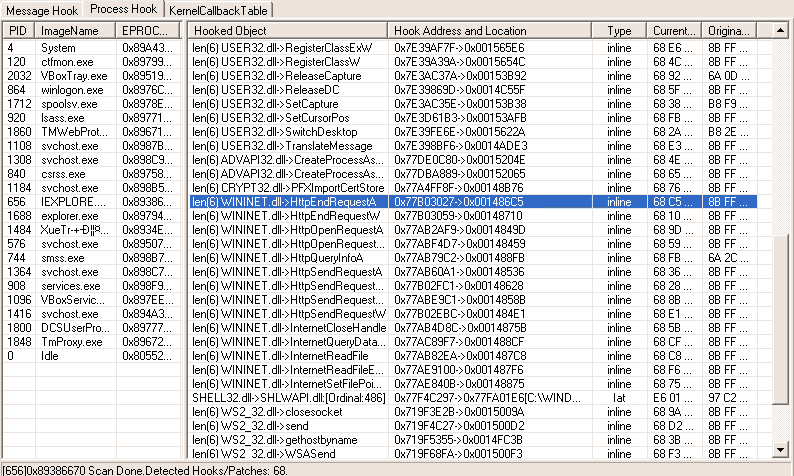
For a web browser process, it will also hook several Wininet APIs (for Internet Explorer), or some other APIs for Chrome/Firefox.
Now the malware is able to filter internet communications, and overall inject HTML/Javascript code into the browser (man-in-the-middle attack), depending on what website you are on (Bank, Paypal, …), to send your credit card informations or credentials to the attacker.
Some variants are also able to detect and inject FTP/Email processes (like FileZilla, Outlook) to steal credentials and propagate on webservers (with FTP) or by email.
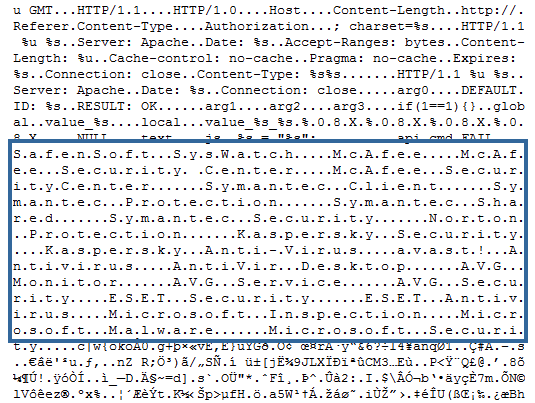
The payload contains also several interesting strings, including a blacklist of antiviruses names, and a very famous string about Brian Krebs (a security researcher).

Removal
Starting with release 10.0.4, RogueKiller is able to automatically remove that trojan. Simply scan your computer and remove infected keys.
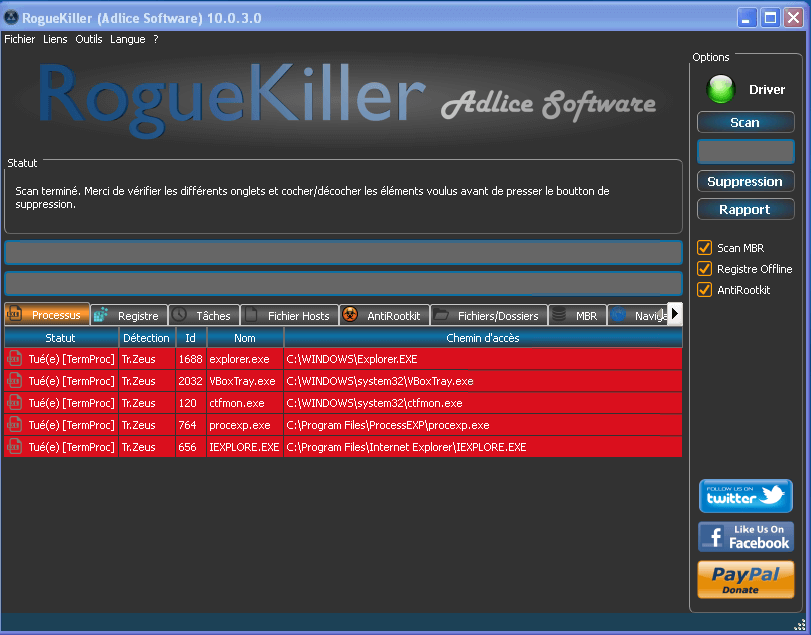
Your reports should look like this (with your own language text):
¤¤¤ Processus : 5 ¤¤¤
[Tr.Zeus] explorer.exe -- C:\WINDOWS\Explorer.EXE[7] -> Tué(e) [TermProc]
[Tr.Zeus] VBoxTray.exe -- C:\WINDOWS\system32\VBoxTray.exe[7] -> Tué(e) [TermProc]
[Tr.Zeus] ctfmon.exe -- C:\WINDOWS\system32\ctfmon.exe[7] -> Tué(e) [TermProc]
[Tr.Zeus] procexp.exe -- C:\Program Files\ProcessEXP\procexp.exe[7] -> Tué(e) [TermProc]
[Tr.Zeus] IEXPLORE.EXE -- C:\Program Files\Internet Explorer\IEXPLORE.EXE[7] -> Tué(e) [TermProc]
¤¤¤ Registre : 1 ¤¤¤
[Suspicious.Path] HKEY_USERS\S-1-5-21-823518204-842925246-839522115-1003\Software\Microsoft\Windows\CurrentVersion\Run | Dyuwso : "C:\Documents and Settings\tigzy\Application Data\Evsi\qykeu.exe" [-] -> Supprimé(e)
A demo of the removal is available here:






