Analysis
Zekos is a malware that patches a system DLL to keep persistence at reboot.
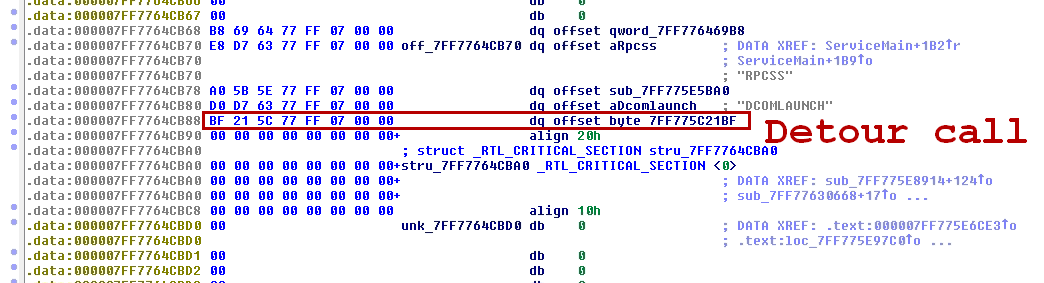
It plays audio advertisement in the background of your machine, without being able to know where it comes from. It keeps persistence by patching rpcss.dll, so that each time it’s loaded it will execute some code in the calling process’ context.
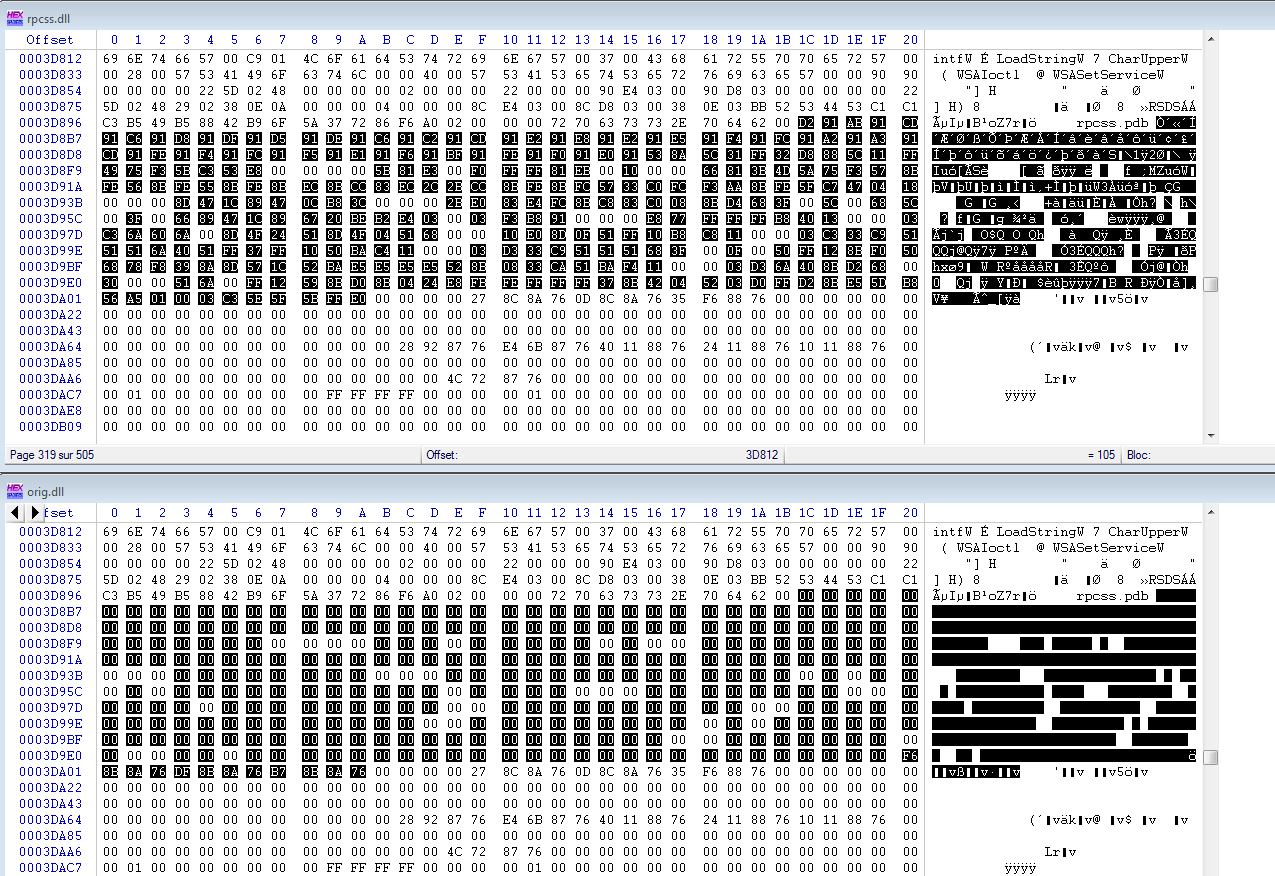
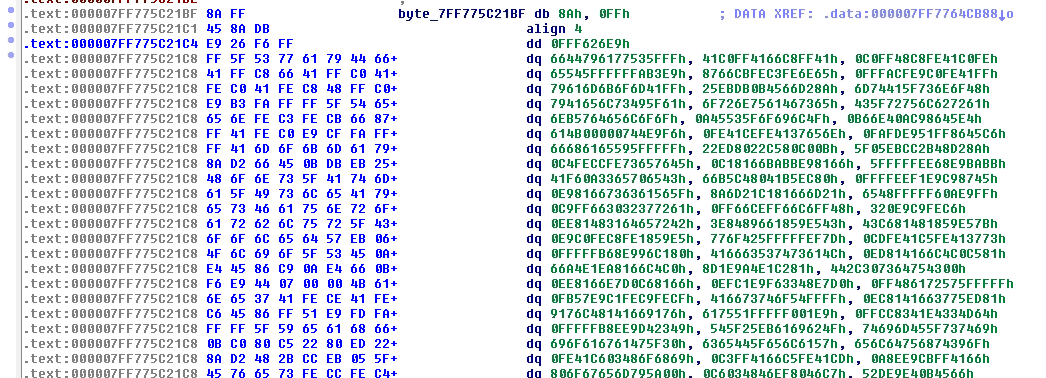
The useful code is contained in a randomly named file, droppped in system32. The name of this file is contained in the patched dll’s payload, with simple XOR encryption.
The DLL service’s entry point is hooked to point to payload.
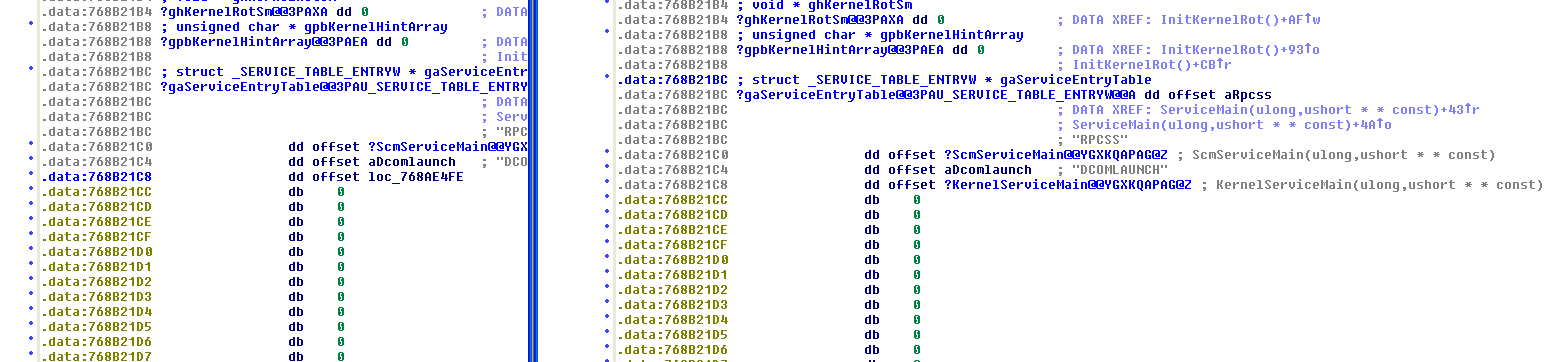
Once called, the DLL will decrypt that name, and execute some code inside.
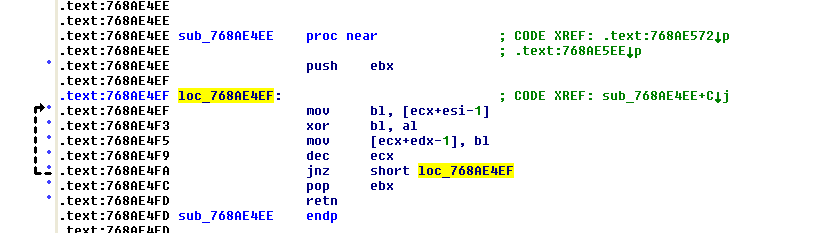
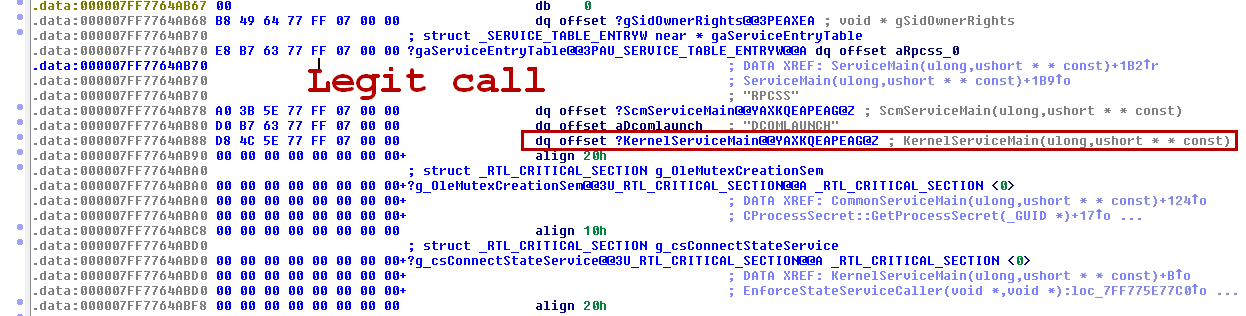
The X64 version is the same. The ServiceEntry table is hooked to point to the payload.
Removal
To remove this malware, simply scan your computer with RogueKiller and remove items. Please look at the demo video.
Your reports should look like this (with your own language text):
¤¤¤ Fichiers / Dossiers particuliers: ¤¤¤
[Root.Zekos][Fichier] rpcss.dll : C:\WINDOWS\system32\rpcss.dll [-] --> REMPLACÉ AU REBOOT -> (C:\WINDOWS\system32\DllCache\rpcss.dll)





