Analysis
Necurs is a rootkit, having a kernel driver and a protected service. The kernel driver has a self-protection feature against service key removal. It also filters which kernel driver can load to avoid antirootkits enter kernelmode and try to defeat it.
It keeps persistence with a randomly named service key, started at boot time. For deep analysis, please refer to that excellent post.
Removal
It’s necessary to act offline. You need to boot on a live CD/USB to remove the malware while it’s not loaded, with the help of RogueKiller’s Honey module. It’s integrated, no worry.
Download RogueKiller and place it where you will easily find it (C:\\). Simply start on the live CD and start RogueKiller, then do the usual Scan/Removal. If you don’t do that offline, you will see an error at service key removal, because the rootkit protects that service key..
Please check out the demo video to remove that nasty piece of malware. OTLPE can be found here.
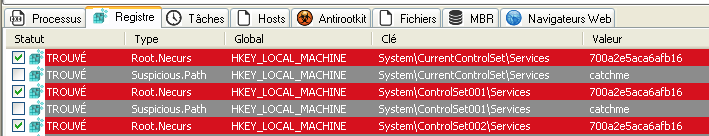
Your reports should look like this (with your own language text) :
[Root.Necurs] HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\700a2e5aca6afb16 -> REMOVED