Description
Bootkits are rootkits infecting the Master Boot Record (MBR) or sometimes the Volume Boot Record (VBR) of a partition. Those rootkits take advantage of super early loading in the system to bypass antiviruses and hide themselves with a kernel driver. Most known bootkits are called TDSS/TDL4, Stoned, PiHar, MaxSST, Rovnix/Cidox, etc…
Analysis
Here’s the boot sequence of a classic machine (ESET courtesy).
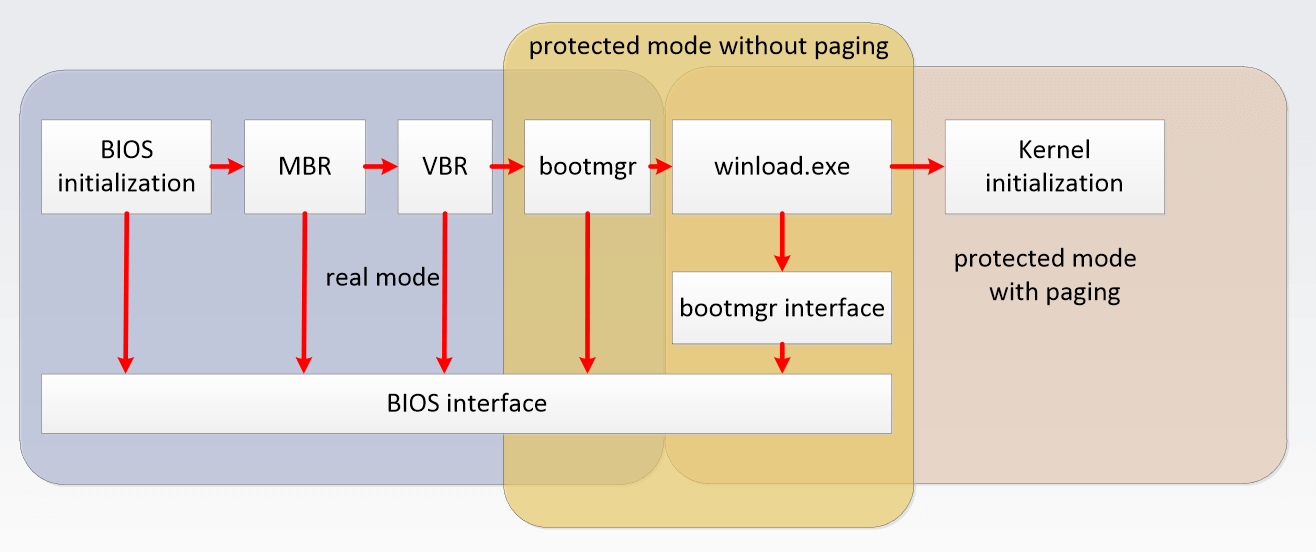
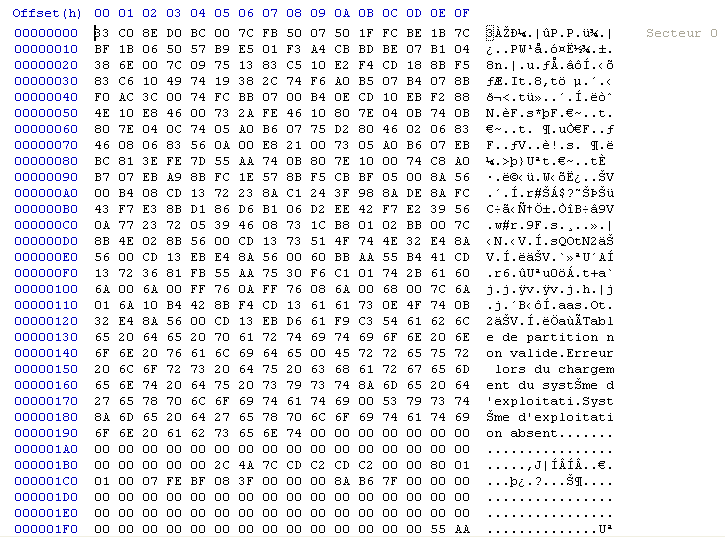
As seen in the picture above, the first component to be called is the Master Boot Record (MBR), which is the sector 0 of a physical hard drive. Below is a picture of what it looks like. MBR describes how many partitions are defined on the hard drive, if they are bootable, their size plus location, and the filesystem used on them. MBR also contains an assembly (16 bits) bootstrap, executed when the system starts.
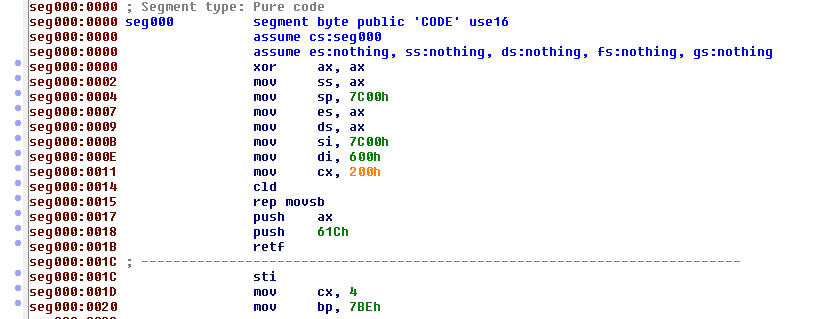
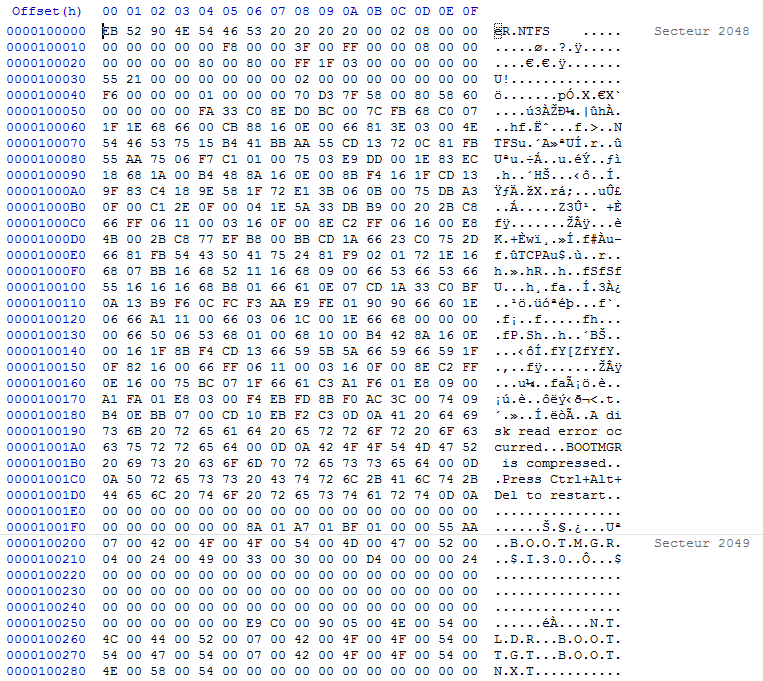
The bootstrap will perform several checks, and in the end will jump to the VBR bootstrap of the bootable partition, located at the sector 0 of the partition. VBR also defines several things about the partition, and contains assembly code executed when called. VBR contains 2 distinct assembly parts, called bootstrap and bootloader. The bootloader will in the end start to load the first component of the Windows operating system.
A bootkit will typically replace any assembly part (MBR/VBR) by a specially crafted one, to copy in memory and execute the code of a malicious driver. They also sometimes hook INT 13/15 interruption handlers to filter memory and disk access, and protect the infected MBR/VBR as well as the kernel driver.
Once done, the malicious driver will inject userland processes with a payload to perform malicious actions (the final goal of the malware), like sniffing passwords, perform web injects, redirect web queries to malicious websites, or open ads.
RogueKiller can detect injected processes, as shown in the capture below:
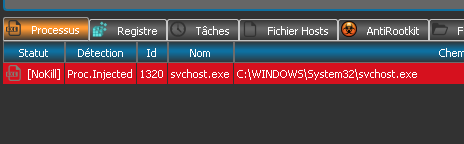
Removal
RogueKiller is able to automatically remove that infection. Simply scan your computer and remove infected items.
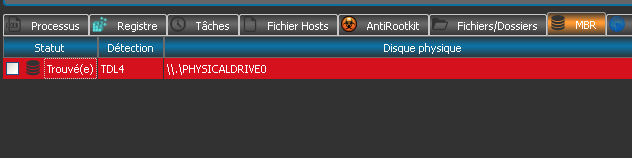
Your reports should look like this (with your own language text):
MBR infection:
¤¤¤ Vérification MBR : ¤¤¤
\\.\PHYSICALDRIVE0 TDL4 -> Trouvé(e)
+++++ PhysicalDrive0: VBOX HARDDISK +++++
--- User ---
[MBR] c708b764ca9daa4f8f33e4e8b3b517da
[BSP] f4eb87199eee8a432bb482bb55118447 : Windows XP MBR Code
Partition table:
0 - [ACTIVE] NTFS (0x7) [VISIBLE] Offset (sectors): 63 | Size: 4086 MB [Windows XP Bootstrap | Windows XP Bootloader]
User = LL1 ... OK
User != LL2 ... KO!
--- LL2 ---
[MBR] 8f672004e1c170714fc27562bd4f6693
[BSP] e0a06c8bf46b8d9ebc34f76f5defa5bf : TDL4 MBR Code [Malware!]
Partition table:
0 - [ACTIVE] NTFS (0x7) [VISIBLE] Offset (sectors): 63 | Size: 4086 MB [Windows XP Bootstrap | Windows XP Bootloader]VBR infection:
¤¤¤ MBR Check : ¤¤¤
\\.\PHYSICALDRIVE0 Rovnix -> Deleted
+++++ PhysicalDrive0: VBOX HARDDISK +++++
--- User ---
[MBR] c708b764ca9daa4f8f33e4e8b3b517da
[BSP] f4eb87199eee8a432bb482bb55118447 : Windows XP MBR Code
Partition table:
0 - [ACTIVE] NTFS (0x7) [VISIBLE] Offset (sectors): 63 | Size: 4086 MB [Windows XP Bootstrap | Rovnix Bootloader (Malware!)]
User = LL1 ... OK
User = LL2 ... OKRemoval demo of TDL4:
Removal demo of Rovnix:








