Adlice PEViewer (formerly RogueKillerPE) is a PE parsing tool, helping researchers during a sample analysis to determine if a sample is malicious and if yes, also gives hints on how to make a signature for it.
Overview
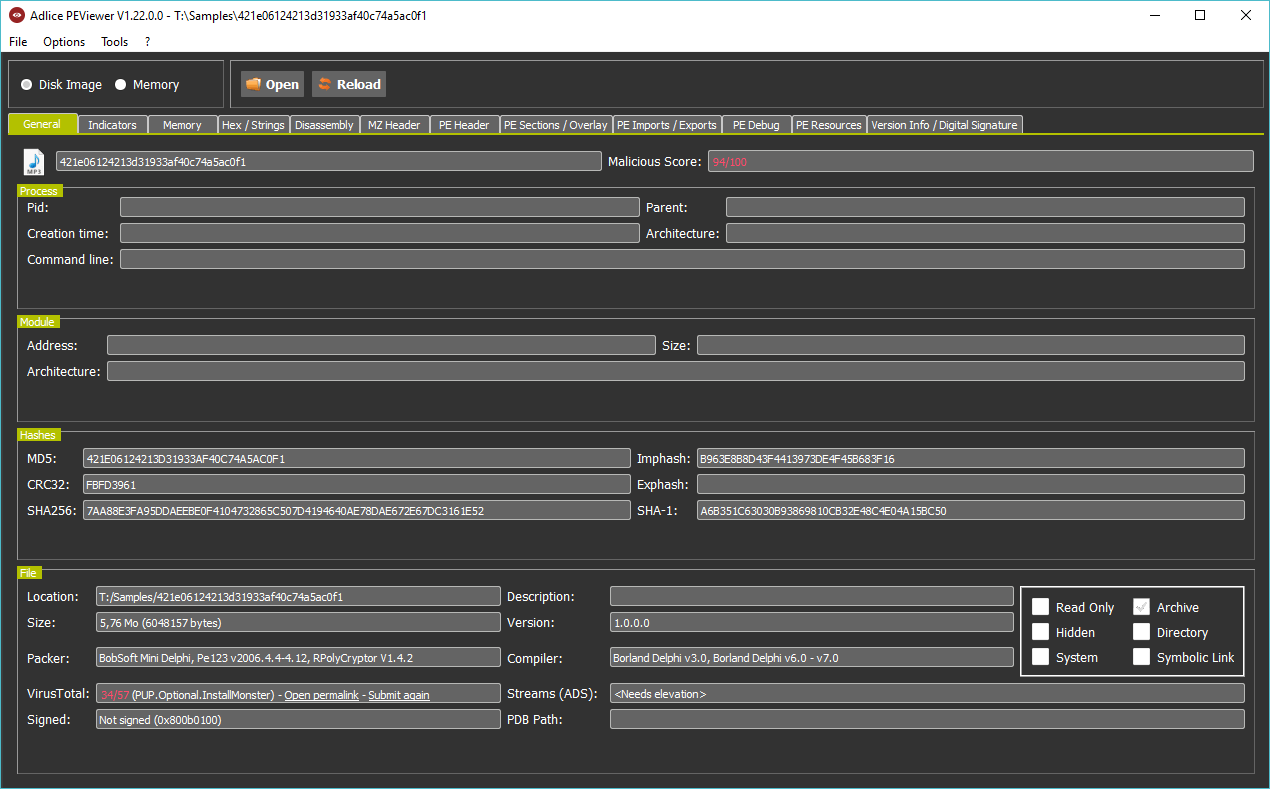
The general tab (overview) is like the sample’s face. It’s intuitive, and most of the time sufficient to know if a sample is malicious. You can see the icon, the PEViewer score as well as VirusTotal’s score, packer and compiler used, and digital signature.
In the example below, we can see it’s hidding behind a MP3 icon and use a PE Packer.
We can also see there’s an error in the digital signature (0x800b010c – A certificate was explicitly revoked by its issuer), due to a stolen (revoked) certificate. And overall, it’s 94% malicious and 34/57 on VirusTotal. No doubt, it’s malicious.
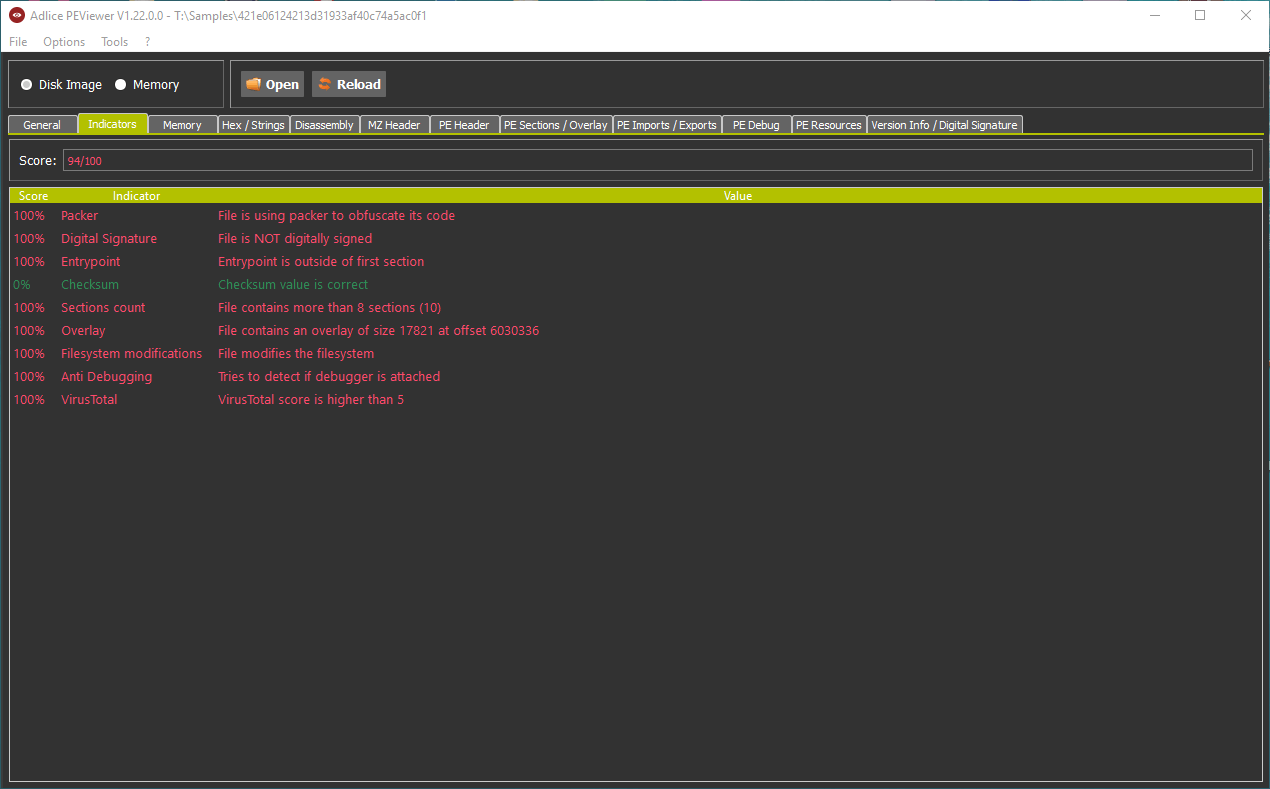
Indicators
Indicators are displayed in the special tab, with a red color for negative impact, and green for positive impact. They all have score and weight, and the addition of all of them gives a global maliciousness score. Here’s an example of some of them:
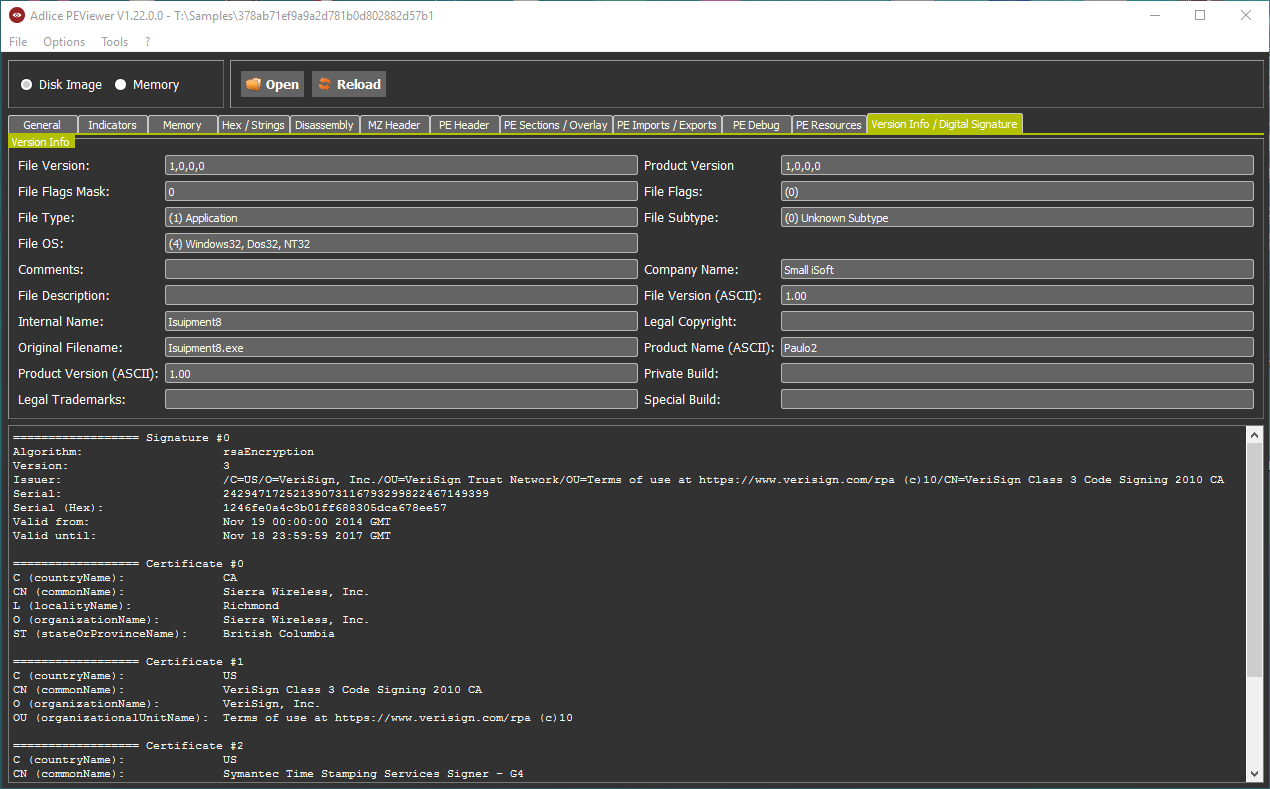
Digital Signature
Digital signature can be of some help to get an idea of the maliciousness of a sample. It is summarized in the General tab, like seen before, but is fully detailed in the Digital Signature tab. In the case of the following sample, the certificate has been stolen and since revoked by Sierry Wireless, Inc. (again the error 0x800b010c).
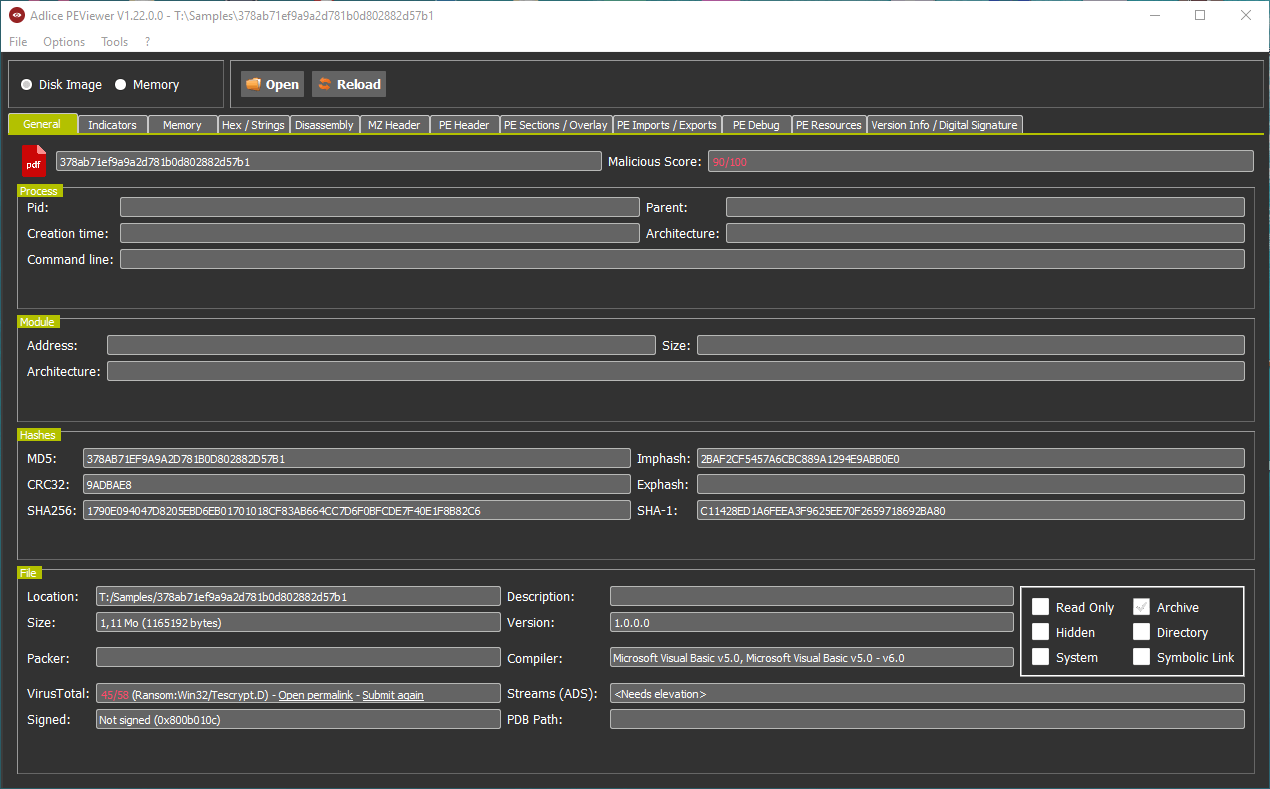
Legit sample
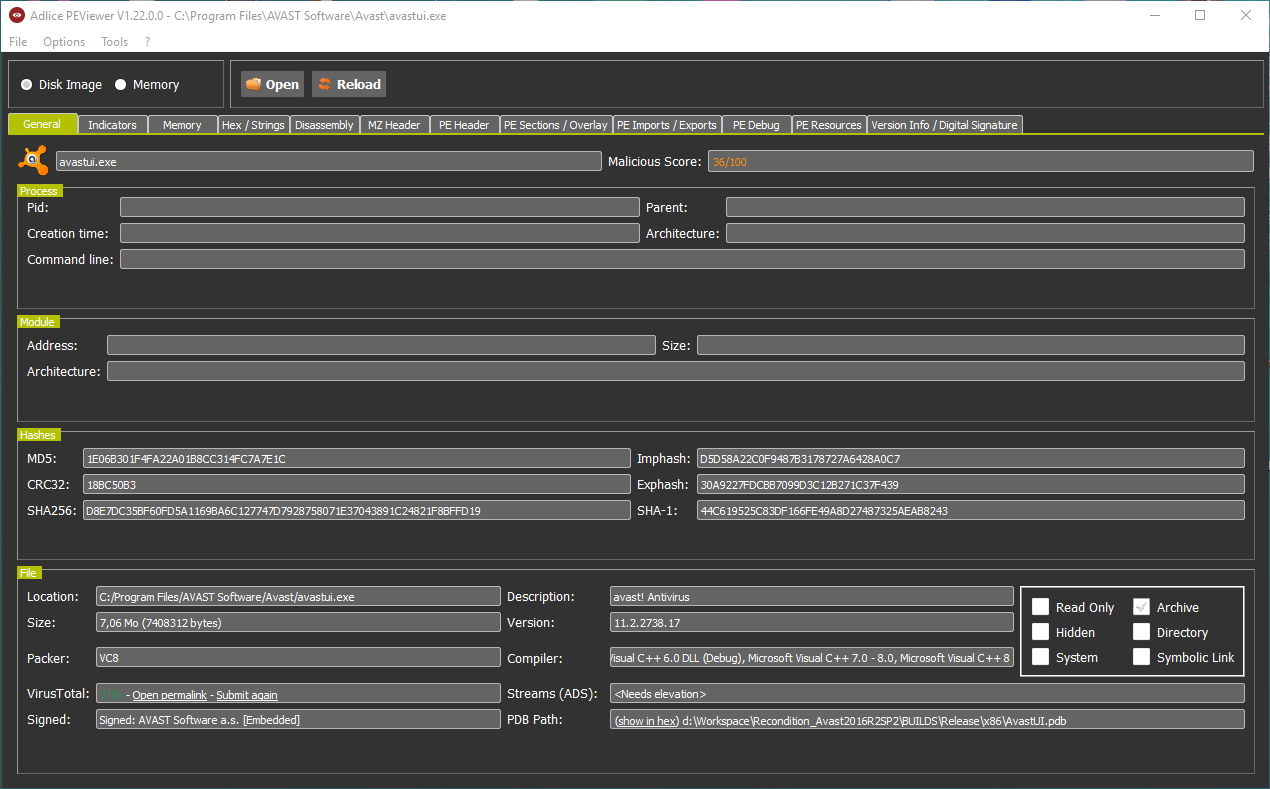
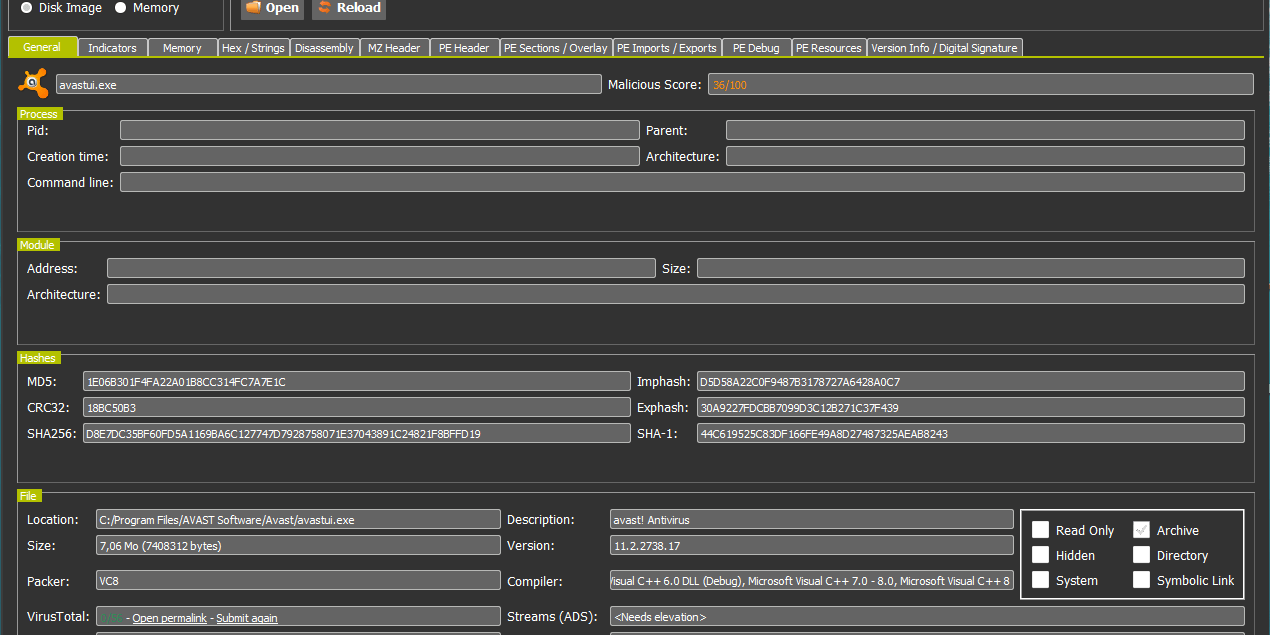
To see the actual difference (of score) with a legit sample, let’s take a look at Avast UI file. We can see something extremely useful in case of a malware, the PDB path. Also, since here the digital signature is valid we can see the issuer in the General tab. The sample reaches an overall maliciousness score of 36%, which is quite low (could have been better, but the file contains an overlay and calls suspicious kernel APIs).