Introduction
What is a PUP? PUP means “Potentially Unwanted Program”. They are designated that way (or sometimes “Not-A-Malware”) because they are in theory not harmful for you, just annoying.
A few examples: Zeus is a real malware, because it steals your bank account number, your passwords etc… Lot of PUPs are more involved into Ads display, bitcoin mining, etc. This is border line because most of the time people don’t know they have them, but it doesn’t harm them directly. They are usually installed with bundled software, when people don’t uncheck optional options.
But sometimes, PUPs are using badware technics to gain access to the web browser, and to remain undetected. This is what we will study here with the BreakingNews “firefox extension”.
Case study: BreakingNews PUP
Update 05/18/2015
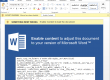
It looks like the technology used is from Injekt (hxxp://www.injekt.com/). They are providing software to inject HTML code in any web browser. This can be seen in the screenshot below with string “Injekt, Injekted, …”. Thanks to @mesa_matt for the info.
First, the dropper is detected 18/57 on virus total. We can see many Adware labels, or PUP.
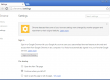
That program is intended to display Breaking News on top of Web browser, I didn’t test the feature in details as it’s not really the subject here.
I’m using Firefox, so I was surprised not to see any extension installed in Firefox and having that program just working (that Breaking News banner with blue border)! That makes it very hard to detect and remove from the web browser. Besides, there is no uninstall entry to remove it from the programs manager.
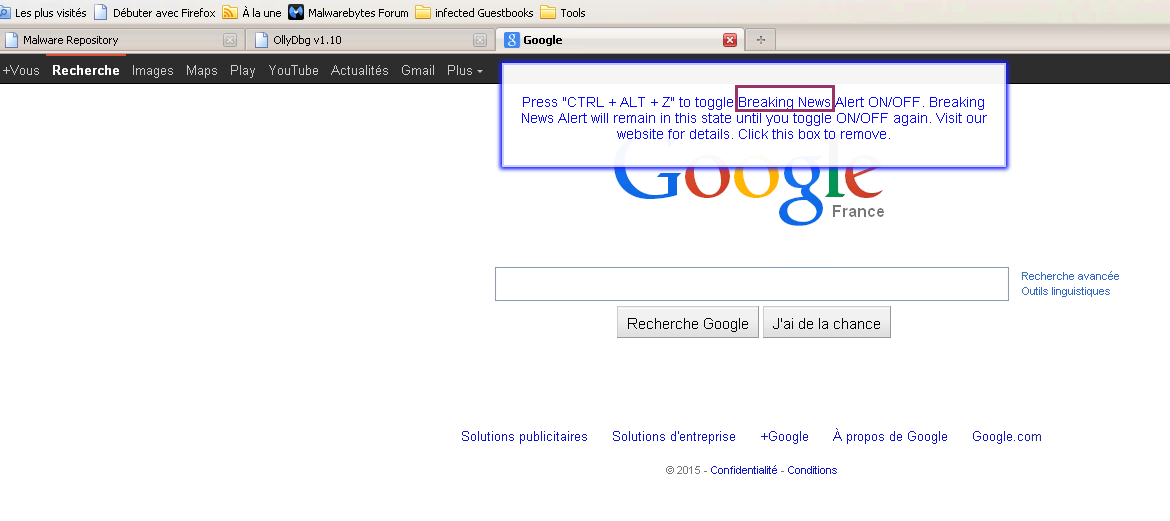
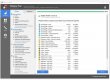
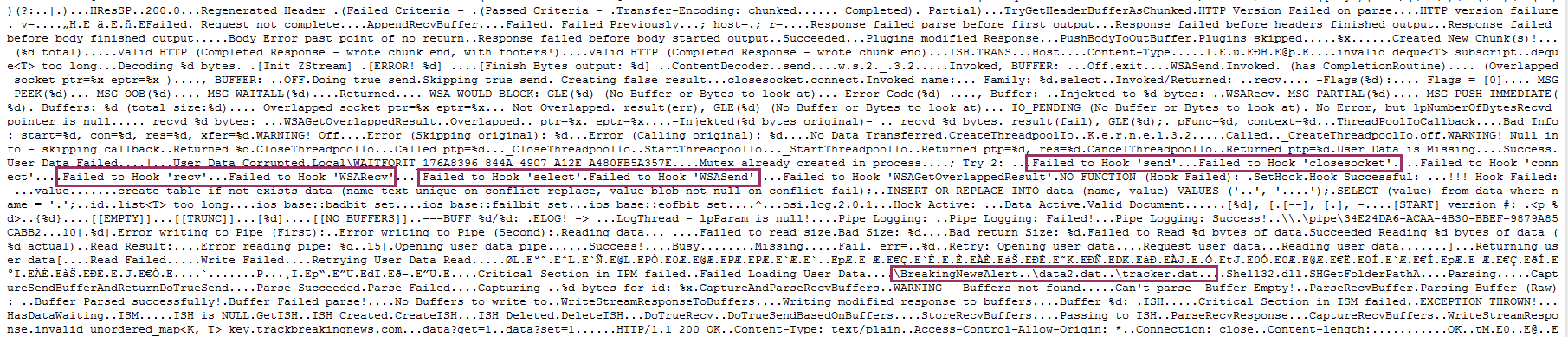
By running RogueKiller, we can see hooks appearing in Firefox (just as a reminder, hooks are code modifications made by a program to filter a function, or an API), on WSARcv API.
This API is called when we receive data from a socket (internet connexion). We can safely assume that whatever program is hooking that API will filter the internet flow.

Also, RogueKiller shows that the hook ends in an unknown module (or shellcode?).
With a debugger attached to Firefox process, we can indeed see the hook in the assembly code.
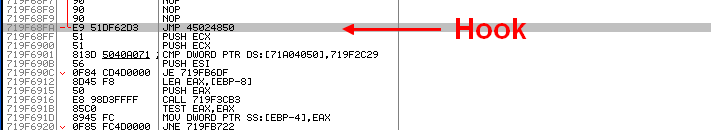
By looking at the sections map, we see that address (0x45024850) is located in a dynamically created section. If we look sections above and below, we can see a PE header, and according to section permissions we can conclude it’s a DLL that has been loaded in a stealth way and hidden in the process. That technique is used by many malware to inject code.
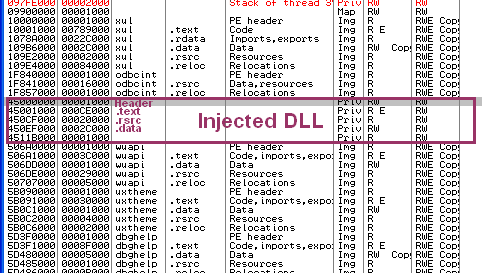
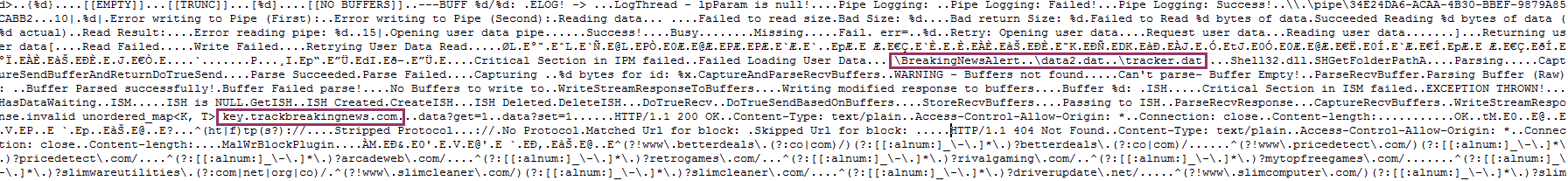
I decided to dump all these sections to look into them for interesting strings. And indeed, we retrieve some interesting things related to BreakingNews PUP.
We see strings related to hooking, BreakingNewsAlert, and tracker data. We also found the main website to trackbreakingnews.com as an evidence.

Conclusion
During our test, we were unable to find any persistence item, nor uninstall key, for BreakingNews PUP.
The fact of hiding code that way in the browser, splice-hooking sensitive APIs (instead of just using Firefox API), and not registering any extension nor uninstall entry is intentional. They just want to be sure their application remains as long as possible on user PC, by hardening the detection and removal process.
Should we call that PUP still? They have clearly crossed the red line.