Analysis
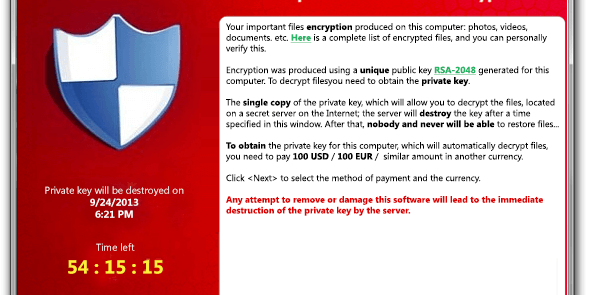
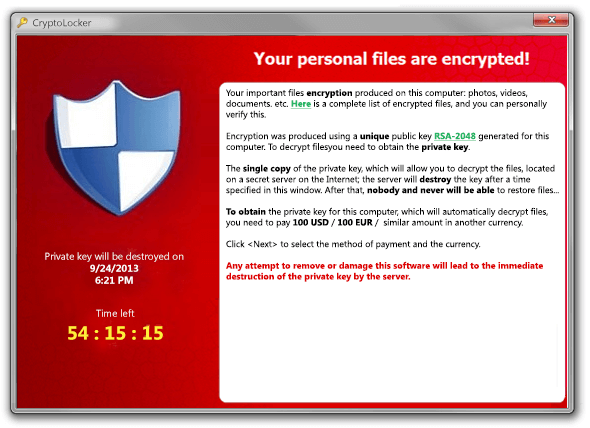
CryptoLocker is a ransomware that uses encryption to corrupt your documents, and asks for a payment to restore them back. It keeps persistence by having 2 processes re-spawning each other when killed, and by restoring the RUN/RUNONCE registry value. Those processes are responsible for crawling the hard drives (and USB drives as well) to search for new files to encrypt, and for displaying the ransom web pages that gather your payment informations (following capture).
With a simple analysis with DiffView, we can see that it stores the encrypted files list into a registry key.
We can also see the persistence RUN values, to be able to restart the infection at boot.
DiffView 1.1.0.0 (by Tigzy)
********************************
Run : 22/12/2013 12:09:48 [Normal Mode]
Machine : VMXP (1 CPUs) [tigzy : ADMIN]
OS: Microsoft Windows XP Professionnel Service Pack 3 (x86)
Diff Time: 1 mn(s)
~~ File Diff: ~~
ROOT --> C:\\Documents and Settings\tigzy
[NEW] C:\Documents and Settings\tigzy\Local Settings\Application Data\Knymfhjmpodrhjjx.exe
~~ Reg Diff: ~~
ROOT --> HKEY_CLASSES_ROOT
ROOT --> HKEY_CURRENT_USER
[KEY][MOD] HKEY_CURRENT_USER\Software
[KEY][MOD] HKEY_CURRENT_USER\Software\CryptoLocker_0388
[KEY][MOD] HKEY_CURRENT_USER\Software\CryptoLocker_0388\Files
[VAL][NEW] HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{75048700-EF1F-11D0-9888-006097DEACF9}\Count : HRZR_EHACNGU:P:\Qbphzragf naq Frggvatf\gvtml\Ohernh\EX_Dhnenagvar\Zcsdyitfmnkaaao.rkr (System.Byte[])
[VAL][NEW] HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run : CryptoLocker ("C:\Documents and Settings\tigzy\Local Settings\Application Data\Knymfhjmpodrhjjx.exe")
[VAL][NEW] HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunOnce : *CryptoLocker ("C:\Documents and Settings\tigzy\Local Settings\Application Data\Knymfhjmpodrhjjx.exe")
Finished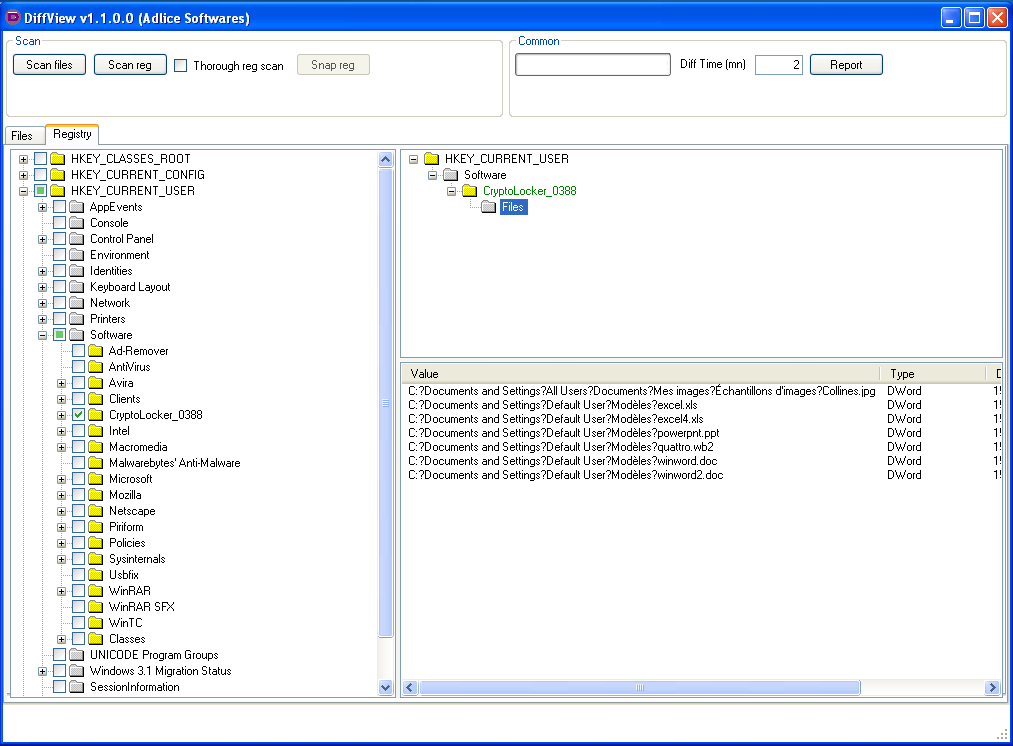
Removal
Simply scan your computer with RogueKiller and remove registry values. Please look at the demo video.
Unfortunately the files cannot be decrypted.
Your reports should look like this (with your own language text) :
¤¤¤ Processus malicieux : 2 ¤¤¤
[Rans.Crypto][BLACKLIST] Knymfhjmpodrhjjx.exe -- C:\Documents and Settings\tigzy\Local Settings\Application Data\Knymfhjmpodrhjjx.exe [-] -> TUÉ [Tree]
[Rans.Crypto][BLACKLIST] Knymfhjmpodrhjjx.exe -- C:\Documents and Settings\tigzy\Local Settings\Application Data\Knymfhjmpodrhjjx.exe [-] -> ERROR [183]
¤¤¤ Entrees de registre : 3 ¤¤¤
[RUN][Rans.Crypto] HKCU\[...]\Run : CryptoLocker ("C:\Documents and Settings\tigzy\Local Settings\Application Data\Knymfhjmpodrhjjx.exe") -> SUPPRIMÉ
[RUN][Rans.Crypto] HKCU\[...]\RunOnce : *CryptoLocker ("C:\Documents and Settings\tigzy\Local Settings\Application Data\Knymfhjmpodrhjjx.exe" [-]) -> SUPPRIMÉ