Introduction
As we saw in Part I, discovery and exploitation of new vulnerabilities are critical to the effectiveness of Exploit kits. In fact, Exploit kits that does not renew its exploits database will not be effective anymore and then will lose popularity and customers.
For various reasons, many people are researching vulnerabilities in programs and ways to exploit them. These include fame, ethics, and of course finance. In this part we will see exploits monetizing, or how the operators make money.
Exploits Monetizing: Legal considerations
It is important to note that searching for vulnerabilities in a program and publishing exploits for them is anything illegal (unless stated otherwise in the software license agreement. The determining factor is the use that is made of the vulnerability exploitation.
Many companies now offer Bug Bounty programs. These programs define a specific report framework and rewards (money, swag, recognition of skills, etc.) offered to security researchers.
For these companies, the advantage of such programs is twofold. This allows them to encourage researchers to report vulnerabilities found via the Bug Bounty program rather than making them public or selling them to other organizations but to realize vulnerability tests cheaply.
Exploits Monetizing: Legal Market
Some companies specialize in buying and selling exploits, often offering much higher purchase prices than those of Bug Bounty programs.
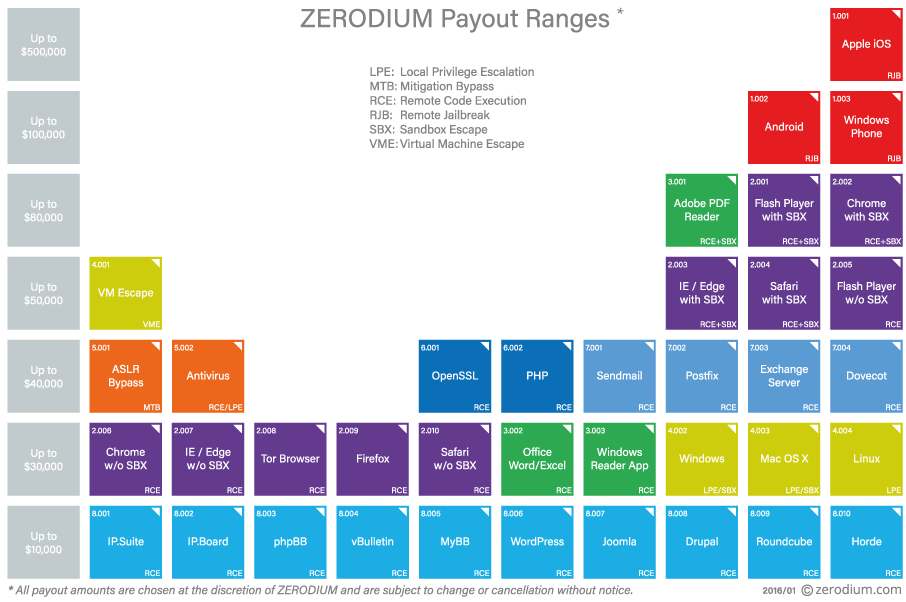
These include the service “Absolute Zero-Day” operated by Kevin Mitnick, which links exploits developers and potential buyers. The service only considers exploits with a CVSS score of a minimum value of 8 and on popular software (see Part I).
Dealers must be qualified to access the service. For this, high registration fees must be paid by sellers and buyers. For the latter, further investigations are carried out. According to Mitnick, a single exploit is sold at the minimum price of $100,000 USD, and their clients include governments and major corporations.
Unlike the “Absolute Zero-Day” service, exploits developers do not need to be qualified. Regarding their customers, ZERODIUM only accepts major companies in the fields of Defence, Finance, Technology, and government agencies.
Black Market
As we have seen above, it is very difficult or impossible to buy exploits from these companies. Therefore alternative exchange places emerged.
Most of the time, these places are private or semi-private forum where it is possible for anyone, for a fee, to buy 0-day exploits but also Exploit Kit, hacking tools, etc.
An example is the private forum Darklife. To access it, it’s necessary to be invited or to pay $100 USD. Once connected and checked, it is possible to access the different sections of the forum:
Another example on the forum exploit.in, where user BuggyCorp offers 0-day exploit (privileges escalation) working on all versions of Windows for $90,000 USD.
A video showing the effectiveness of the exploit despite the presence of the EMET tool (see Part I) is also included.
Transaction exemple
We will study here a transaction between the Russian hacker Vitaliy Toropov and company Hacking Team, which specializes in selling software for spying and surveillance.
On October 13 2013, Vitaliy Toropov initiates contact with the company and offers to sell them six exploits for Windows, Java, Flash Player and Safari, for a price of $30.000 to $45.000 USD per exploit.
Hi, is your company interested in buying zero-day vulnerabilities with RCE exploits for the latest versions of Flash Player, Silverlight, Java, Safari?
All exploits allow to embed and remote execute custom payloads and demonstrate modern techniques for bypassing ASLR and DEP-like protections on Windows, OS X, and iOS without using of unreliable ROP and heap sprays.
The company is only interested in the exploit for Flash Player. On 25 October, an agreement is made between Toropov and Hacking Team, whose clauses are:
- The price is set at $45,000 USD for a non-exclusive sale and includes a discount on future exploits
- Sources of the exploit are shared, and three days of testing are planned
- Payment will be made in three parts : $20,000, $15,000 and $10,000 USD
- Payment can be interrupted if the vulnerability is patched by the software vendor
- Hacking Team is committed to not report the vulnerability to the software vendor
On October 29, Hacking Team testes the exploit and on October 30, Toropov receives the first part of the payment. It is latter specified that the discount will be of $5,000 USD for the second deal and $10,000 USD for the third one.
In total, Hacking Team bought for a minimum known amount of $84,000 USD exploits to Vitaliy Toropov.
Conclusion
It is perfectly legal to search for vulnerabilities and exploits for them. Software vendors have realized this and developed Bug Bounty programs. However, these programs cannot compete in financial terms with companies and specialized platforms in the resale of exploits. It is therefore unlikely to see them disappear in a short or medium timespan.
As we have seen with the transaction between Vitaliy Toropov and Hacking Team company, acquiring an exploit is made under strict conditions (customer commitment, exploit test, guarantee measures, etc.) even on the parallel market, ensuring both the interests of the developer and the client.
It is thus possible to consider that some companies don’t hesitate to carry out such transactions, to more or less laudable reasons.