Introduction
This article is segmented into three parts in order to present in detail the various aspects of exploits and exploit kits.
- The first one will present the exploits definition and explanation of these terms, how they are used and the methods which could be used against them : Part I – Exploits, Exploit kits and Protection
- The second one will focus on the marketplace where they are bought/sold, sometimes legally, sometimes not : Part II – A Marketing Approach
- The third one will explore in details the inner working of exploits, exploits kits and anti-exploit : Part III – A Technical Approach
Exploits Definition
An exploit is a code section used to exploit software vulnerability in order to gain increased privileges (code execution, getting information, etc.) on the computer running said software. This brings us to the definition of a software vulnerability: it’s a design error made by the developer that could be exploited. Concrete examples of vulnerabilities will be presented in Part III.
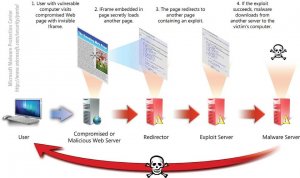
An exploit kit is a software usually running on top of a Web server and containing different exploits. Its goal is to list exploitable software installed on the computer communicating with it and to deliver the appropriate exploit in order to infect the remote computer (drive-by download).
Usually, operating an exploit kit doesn’t require any exploitation knowledge making it very easy to use.
Criticality level of vulnerabilities
All software vulnerabilities don’t pose the same threat. Indeed, to be exploited some require special conditions and others only give limited access to the remote system. That is why an organization, the MITRE, handles referencing.
Once a vulnerability is discovered and made public, the exploits definition is added to the Common Vulnerabilities and Exposures (CVE) dictionary as a CVE identifier. The assessment of the criticality of vulnerabilities is governed by the Common Vulnerability Scoring System (CVSS).
This assessment consists of three measures called metrics and consisting of various risk factors. The higher the risk factor, the greater will be the metric value, with 10 being the maximum value. Unreferenced vulnerabilities and vulnerabilities for which there is no patch available are called by the name « 0-day ». However, this doesn’t affect their CVSS score.
Popularity level of vulnerabilities
Software with the most vulnerabilities are not necessarily the most exploited. Indeed, several factors must be taken into account:
- CVSS score
- Software popularity
- « 0-day » or not
CVSS score: As we have seen in the above paragraph, the higher the CVSS score of a vulnerability, the higher its exploitation is easy. We can therefore deduce that vulnerabilities with a high CVSS score are more likely to be exploited than them with a lower score.
Software popularity: The purpose of exploit kits is to infect as many machines as possible. So, the most exploited vulnerabilities are cross-platform products or the Windows operating system and its applications (almost 90% of non-mobile connected devices).
« 0-day » or not: A « 0-day » vulnerability might be exploitable for months or even years. The development of an exploit is particularly profitable (see Part II).
Demonstration:
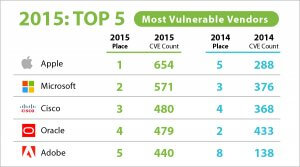
In 2015, the MITRE referenced 654 vulnerabilities for Mac OS operating system and Apple software. Microsoft ranks second with 571 vulnerabilities.
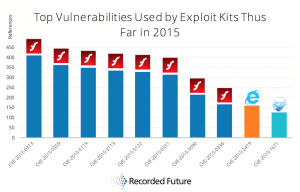
Yet, if we compare these figures with those of the top exploited vulnerabilities used by exploit kits, we realize that the first eight places are occupied by Adobe Flash Player, which occupies the 5th place in the most vulnerable vendors ranking.
If we analyse the case of the CVE-2015-0313 vulnerability, the most exploited, we realize that its CVSS score is 10, that it’s cross-platform (Windows, MacOS, and Linux) and is « 0-day ».
Passives protections
Many exploits still used today target vulnerabilities for which patches are available. So, it’s highly advised to keep software installed up-to-date (for example by using UCheck), especially high risk software ones such as:
- Operating systems
- Web browsers and the installed plugins (Flash Player, SilverLight, Java, etc.)
- PDF readers
This will of course not be effective against « 0-day » exploits.
Another approach is to consider the browser as the entry point for exploits and to use a Sandbox. In this context, even if an exploit is executed and malware installed on the host system, it will be, for the most part, easy to remove. However, this protection does not prevent user data theft.
It is also possible to filter the requests between the browser and the remote server and allow only legitimate traffic. Software like NoScript or uMatrix made this possible.
Although highly effective, the main disadvantage of this approach is a strong user investment.
Active protections
Software specifically designed to protect against « 0-day » exploits were developed, named « anti-exploits. These include Enhanced Mitigation Experience Toolkit (EMET) or Malwarebytes Anti-Exploit (MBAE).
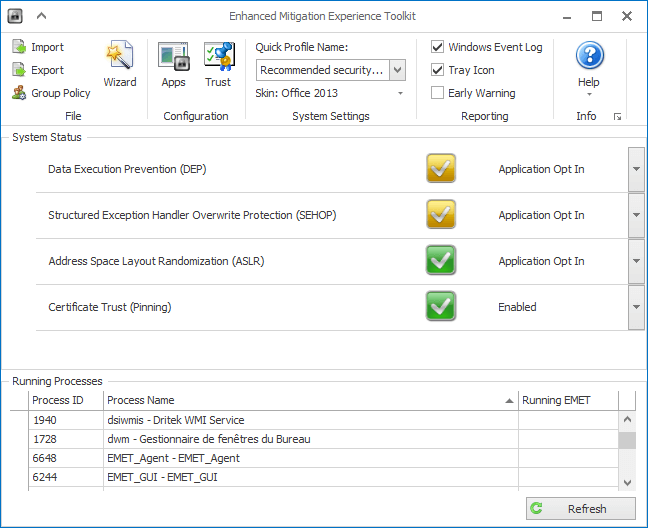
Most of the methods used by exploits (see Part III) are known and these software can detect them and make them ineffective. However, these tools are not infallible and malware constantly adapt to circumvent them.
Conclusion
After talking about exploits definition, we’ve seen that exploit kits played a major role in the spread of malware since they allow the attacker to silently install them without any user interaction. The products for which the most vulnerabilities have been discovered are not necessarily less safe and the most exploited. There are no fool proof solutions to protect oneself against this kind of threat. Also, it is advisable to combine passive and active protections, to minimize the potential attack surface.