Alpha bay, Silk Road, Hansa: They made the headlines of newspapers for weeks. They were underground markets offering several illicit goods and services and were shut down in 2013 and 2017. All were using Tor, currently the most used parallel Internet network, called Darknet.
DARKNET
Computers connected to the Internet use the Internet protocol suite (TCP/IP) protocol to connect to each other. Darknet are networks connecting computers through their own communication protocols built on top of TCP/IP (network overlaying).
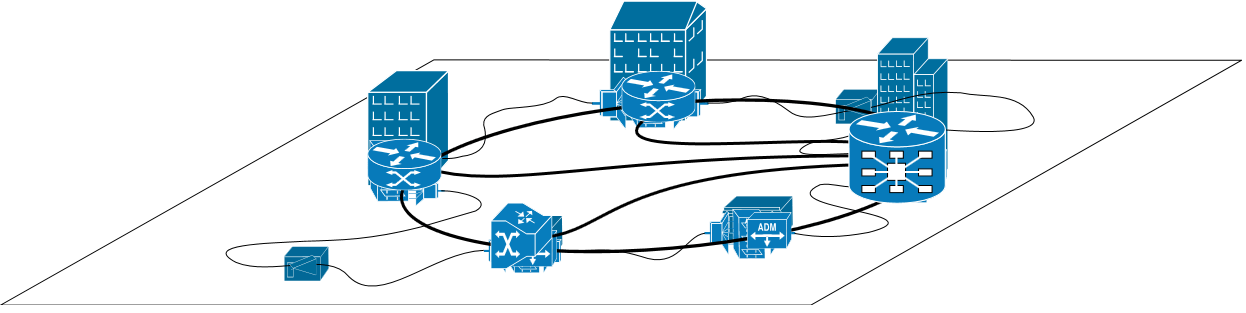
(Here, the bold cables represent the overlay and the smaller one, TCP/IP. We can see that the computers are not connected in the same way within the two networks.)
Since the computers part of a Darknet are interconnected using custom protocols, they usually provide more privacy than the Internet, often offer anonymous services like mail and Instant Messaging and data only accessible using the Darknet specific protocol.
Their ultimate goal is to provide complete anonymization between the data provider (like a webserver) and the client accessing such data (like a browser) using custom routing rules and specific encryption system.
USAGE
Darknets were originally designed to ensure safety of political dissidents and circumvent network censorship used by totalitarian regimes, but also as a reaction to mass surveillance performed by governmental organisations.
Although such networks are still heavily used for these purposes, criminals made their way into them, attracted by the anonymity they provide. Sharing of illegal contents and selling of illicit or illegal goods or services were greatly facilitated since they cannot be accessed without knowing the exact address and search engines are unable to see them (Deep Web).
Servers hosting or offering such illegal contents are hard to take down and the people running them even harder to arrest. For the record, Silk Road market owner were tracked down thanks to the use of honeypots and hacking by the Drug Enforcement Administration (DEA).
Several Darknets are currently operating, the best known being Freenet, I2P and Tor. The last one being the most popular (both for free speech and criminal activities), we will focus on it.
TOR
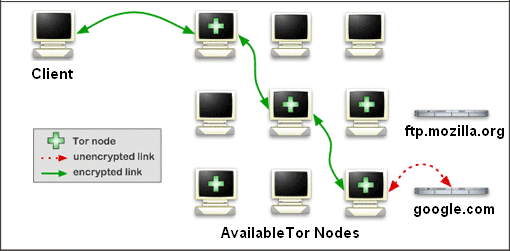
Tor is composed of multiples network relays that are able to connect to each other. When using the Tor network, traffic flow between these nodes are using a random path, being encrypted and decrypted on the fly, before reaching an “exit node” that will connect to the desired service, using standard connection.
Network administrators can configure the service they manage to be also directly accessible within the Tor network, removing the need to pass through an exit nodes, using a “.onion” address.
One such exemple is DuckDuckGo search engine which can be accessed using address https://duckduckgo.com or 3g2upl4pq6kufc4m.onion.
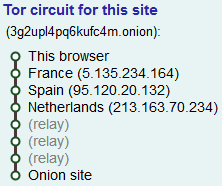
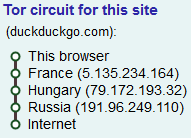
However, some are only reachable through a “.onion” address and have no standard counterpart, these are called “hidden services” and usually feature illegal contents, like underground markets.
DEEP WEB
The easiest way to connect to the Tor Network is to use the Tor Browser. Based on Mozilla Firefox, it automates the connection to the nodes and is already configured to handle “.onion” links.
To ensure maximum privacy and to prevent data leaks (like the real address IP of the user), JavaScript interpretation and WebSockets feature are disabled, which can alter some sites functionalities.
Even if numerous illicit markets were closed in 2017, it is still possible to find some easily. The goods the most proposed are drugs or medications that require prescriptions to obtain them (usually opiates), followed by credit card number and password lists, counterfeits and porn accounts.

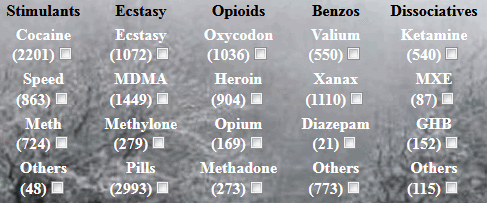
Some markets features more sensitive contents like child pornography videos, weapons and even hitman services but they are harder to find. The transaction between the seller and the buyer are anonymous and the payment is made available through the use of cryptocurrencies.
TECHNICAL RISKS
Even if Tor provides anonymity, some flaws may be exploited that may allow law enforcement agencies to localise the real location where the .onion link point to. When the server has been seized, it’s a piece of cake to reprogram it to serve code that may be used to get the real identity of the visitor. In most countries, buying illicit goods is punished by the law.
Attackers can also set exit nodes to gather email addresses and password used by Tor users when connecting to online accounts. Such attacks can easily be prevented using end-to-end encryption (HTTPS instead of HTTP).
More rarely, network traffic may be modified to include malware in downloaded software. However, this won’t work with signed executables.
CONCLUSION
Tor and Darknets in general are a really good thing to improve freedom of speech for oppressed or threatened people like political opponents or whistleblowers, even if they feature a darker side. When using Tor, never assume you are truly anonymous and that you are 100% safe from legal repercussions associated with your actions.