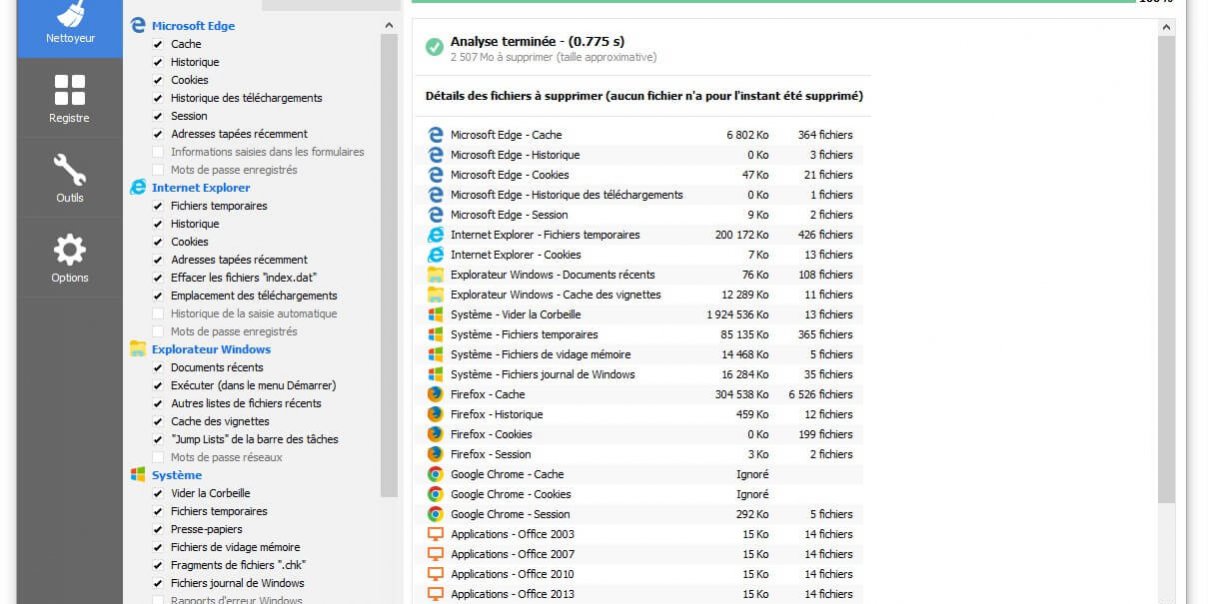
Version 5.33 of the popular machine cleaner CCleaner has been compromised to deliver the Floxif malware as injected DLL. Older and newer versions are not affected, and Avast (CCleaner owner) claims simply updating to 5.34 removes the malware.
Update: September, 21
Talos discovered that the supposedly sleeping or idle infection was actually just filtering for specific targets on C&C (command and control) server. After analysing the server code, they discovered interesting domains list of the possible targets, including Cisco, Samsung and other big corporations.
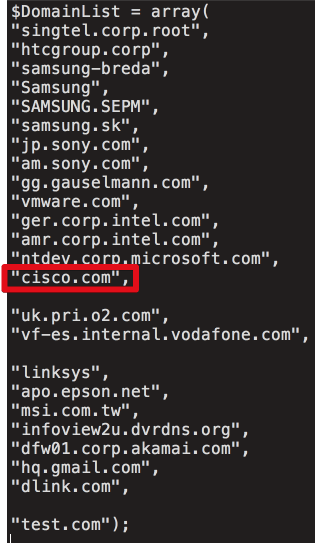
They also found that machines from these organizations (20 machines) got a second stage payload. As of now, we don’t know what this second stage infection is doing. Also, another registry key was found storing a malware (later executed by the infection):
HKLM\Software\Microsoft\Windows NT\CurrentVersion\WbemPerf\001 HKLM\Software\Microsoft\Windows NT\CurrentVersion\WbemPerf\002 HKLM\Software\Microsoft\Windows NT\CurrentVersion\WbemPerf\003 HKLM\Software\Microsoft\Windows NT\CurrentVersion\WbemPerf\004 HKLM\Software\Microsoft\Windows NT\CurrentVersion\WbemPerf\HBP
What happened?
Every big software company uses “continuous integration and deployment”, a methodology that allows easier, faster and safer software update (with testing). Usually, this requires a dedicated machine where the source code is compiled into the new binary/installer.
That machine is also responsible for signing the end package to make sure no altered version can be spread under the company’s name (see our blog post about code signing).
It is very possible (not confirmed) that this machine was compromised and that hackers gained access to it. They either altered the source code (unlikely) or added a patch routine (most likely) on the end binary, just before the digital signature processing.
The patch
The official CCleaner binary was patched using the TLS callback method. That means the TLS callback is first called, before the actual binary entrypoint. That way, the malware is able to execute its own code before to launch the legitimate program.
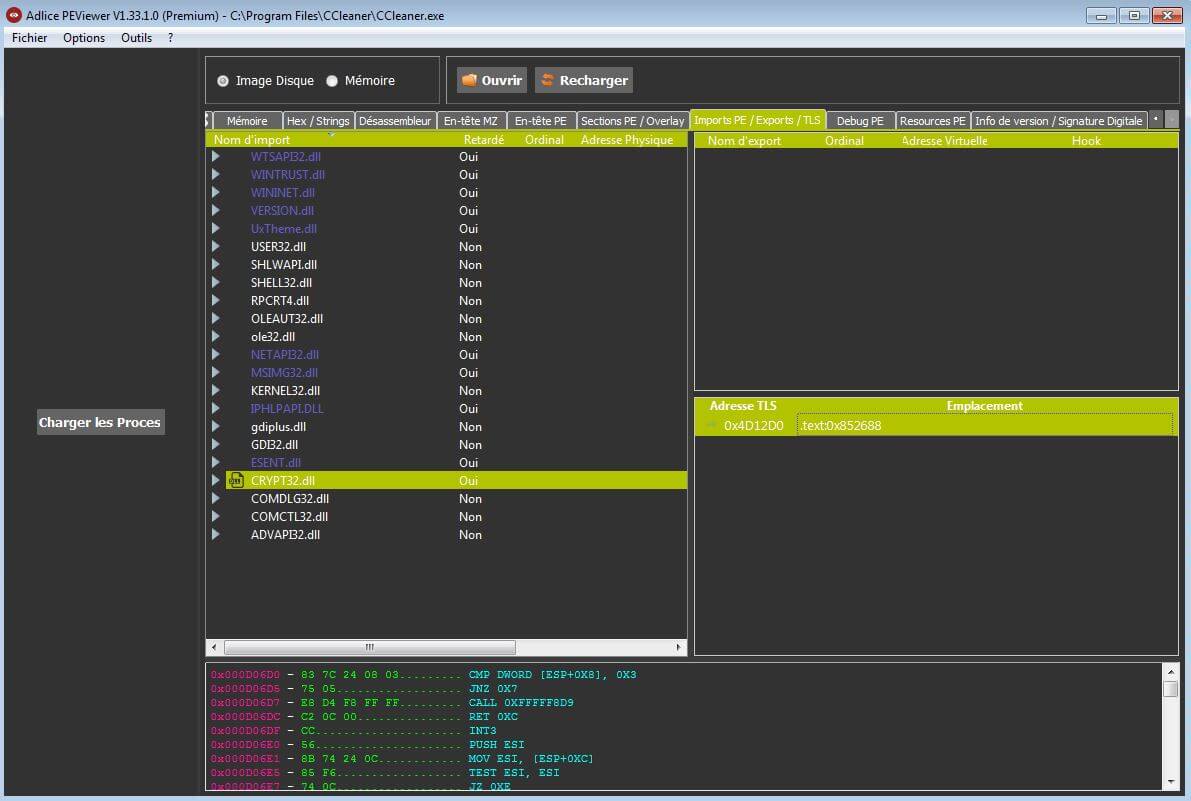
In this routine, the malware is executing what appears to be a PE loader, using Heap creation and execution. The payload is a DLL stored encrypted (XOR) without the PE header (to avoid AV detections), and once loaded it fires a new thread that will run the malware code.
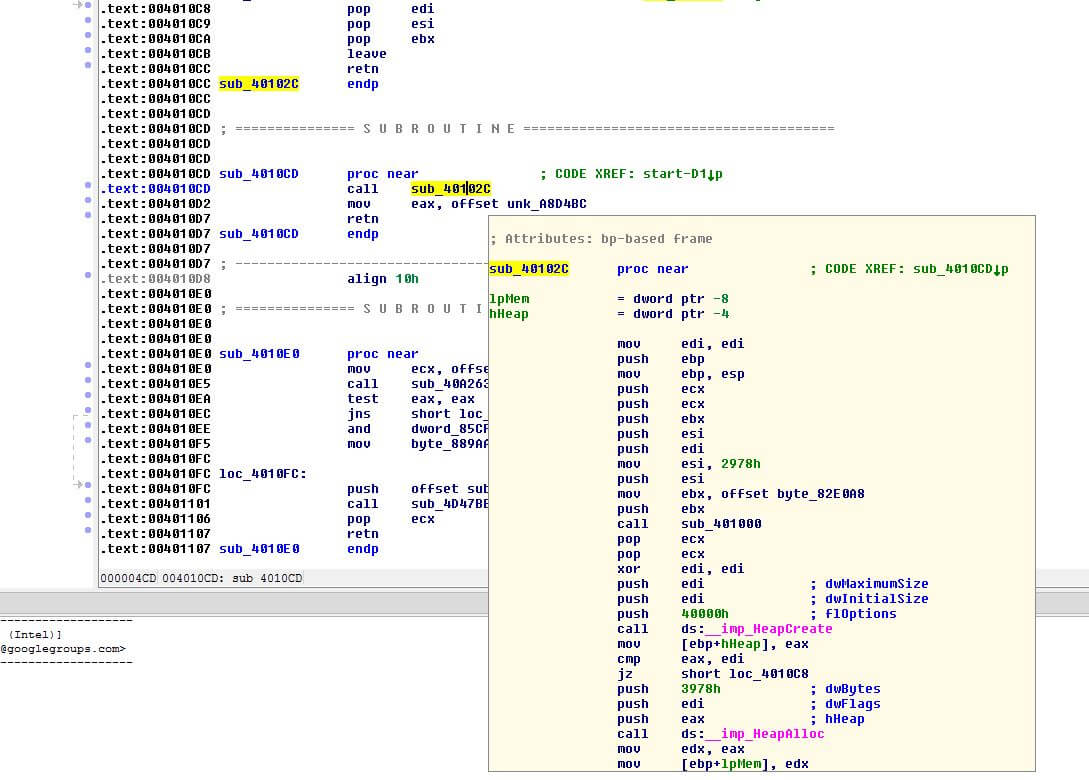
The malware code appears to be using extensively the following registry key to store data:
HKLM\SOFTWARE\Piriform\Agomo
Also, for now, the malware doesn’t seem to be very aggressive and only logs inoffensive data from the machine (machine name, IP address, etc…). But this may change very quickly if the malware owner decides to send different orders from the command and control (C&C) server. It could ask to deliver a Ransomware for example.
Update: The C&C server has been takedown and DGA domains taken, so in theory the malware cannot do anything now.
Removal
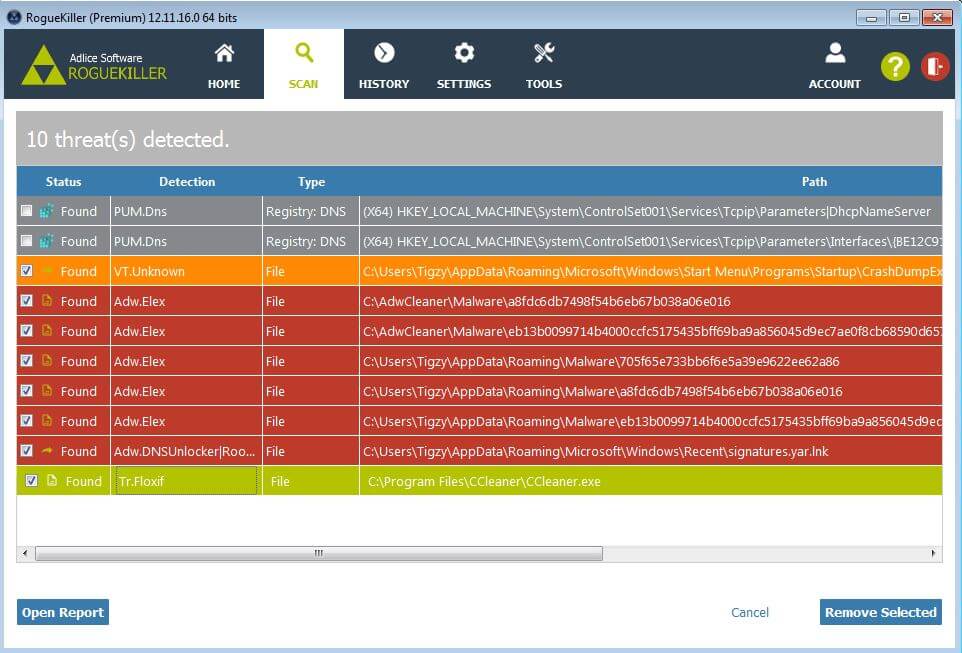
Avast claims updating CCleaner to version 5.34 addresses the issue and removes the malware. However, RogueKiller (version 12.11.16 and above) finds the infected CCleaner binaries, as well as the registry keys used by the malware and remove them.
Links
– http://blog.talosintelligence.com/2017/09/avast-distributes-malware.html
– http://blog.talosintelligence.com/2017/09/ccleaner-c2-concern.html
– https://www.piriform.com/news/blog/2017/9/18/security-notification-for-ccleaner-v5336162-and-ccleaner-cloud-v1073191-for-32-bit-windows-users
– https://www.bleepingcomputer.com/news/security/ccleaner-compromised-to-distribute-malware-for-almost-a-month/