How Internet Explorer BHO can turn into a Spy
What is a BHO? A BHO (for Browser Helper Object) is a module (often a DLL) that acts as a plugin for either explorer.exe or Internet Explorer. Most of the time (as its name suggests) it’s used to extend Web Browser features with some customization. If you’re familiar with Internet Explorer, you probably use some extensions, or toolbars. They are BHOs.
Like any web browser extension, a BHO runs in the context of the web browser, using provided APIs. Knowing that, it’s easy to understand that an extension can have access to pretty much everything you’re doing on the web, including passwords, bank information, credentials, and so on, no matter if encryption is used (SSL). And this is what I’ll try to demonstrate.
What is a BHO ?
To be able to start within the web browser, a Internet Explorer BHO needs to be registered first. This is usually done with the command regsvr32.exe myBHO.dll.
This will call the registration routine (that you have to code, see later), that will add a registry key to globally register the DLL in the system under a guid name:
(x86) HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Classes\CLSID\{guid}
(x64) HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{guid}
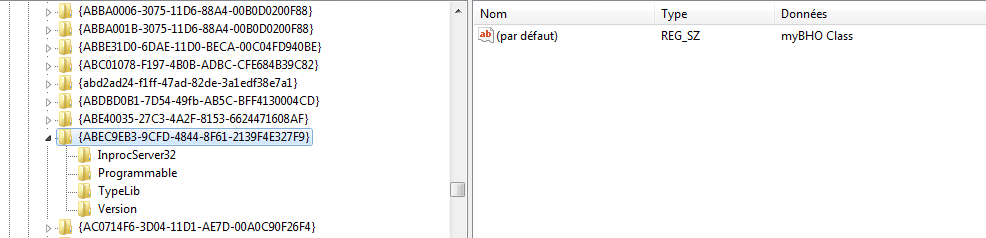
And the registry key that will add a new BHO using the defined guid above:
(x86) HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\explorer\Browser Helper Objects\{guid}
(x64) HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\explorer\Browser Helper Objects\{guid}
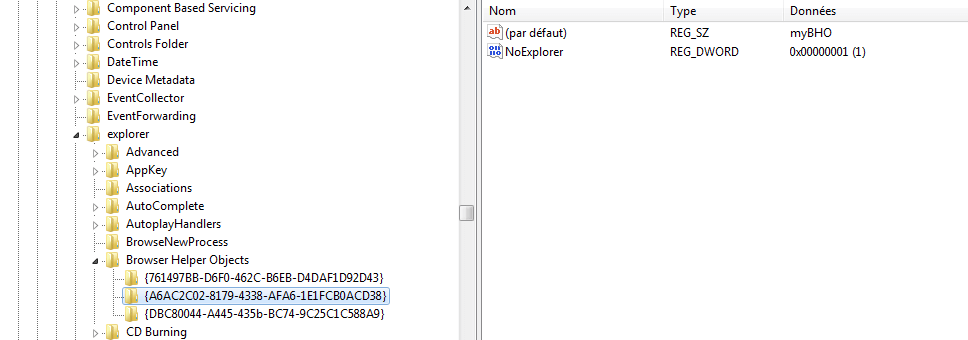
That registry key is responsible for loading the DLL into Internet Explorer.
To unregister a DLL, use regsvr32.exe /u myBHO.dll.
How to make a BHO ?
First, we need to learn how to code a BHO. Microsoft gives us a tutorial to get on rails, let’s follow it to create the project and have some working code. Once done, let’s customize it.
Our main goal is to intercept data from forms that are posted back to a web server. This includes login and passwords, even encrypted with SSL, and even visually obfuscated (with dots or stars).
We are using the BeforeNavigate2 event because it’s fired when clicking on a link, or submitting a form.
.h file
class ATL_NO_VTABLE CmyBHO :
public CComObjectRootEx,
public CComCoClass<cmybho, &clsid_mybho="">,
public IObjectWithSiteImpl,
public IDispatchImpl<imybho, &iid_imybho,="" &libid_bholib,="" *wmajor="*/" 1,="" *wminor="*/" 0="">,
public IDispEventImpl<1, CmyBHO, &DIID_DWebBrowserEvents2, &LIBID_SHDocVw, 1, 1>
{
...
public:
STDMETHOD(SetSite)(IUnknown *pUnkSite);
void STDMETHODCALLTYPE OnBeforeNavigate( IDispatch *pDisp, VARIANT *pvarURL, VARIANT* pFlags, VARIANT* pTargetFrameName, VARIANT* pPostData, VARIANT* pHeaders, VARIANT* pCancel );
...
};.cpp file
void STDMETHODCALLTYPE CmyBHO::OnBeforeNavigate( IDispatch *pDisp, VARIANT *pvarURL, VARIANT* pFlags, VARIANT* pTargetFrameName, VARIANT* pPostData, VARIANT* pHeaders, VARIANT* pCancel )
{
HRESULT hr = S_OK;
// Query for the IWebBrowser2 interface.
CComQIPtr spTempWebBrowser = pDisp;
// Is this event associated with the top-level browser?
if (spTempWebBrowser && m_spWebBrowser && m_spWebBrowser.IsEqualObject(spTempWebBrowser))
{
VARIANT* post = pPostData->pvarVal;
if ( post && post->vt == (VT_ARRAY|VT_UI1) )
{
ULONG size = post->parray->rgsabound[0].cElements;
//Obtain safe pointer to the array
void * pArrayData;
SafeArrayAccessData( post->parray, &pArrayData );
//Copy the bitmap into our buffer
BYTE* buff = (BYTE*) malloc(size);
memcpy( buff, pArrayData, size );
//Unlock the variant data
SafeArrayUnaccessData( post->parray );
MessageBoxA( NULL, (char*)buff, "posted", MB_OK );
free( buff );
}
}
}The code is very basic. We only read pPostData value, and output its text in a MessageBox. Let’s take a look at the resuts.
BHO Analysis
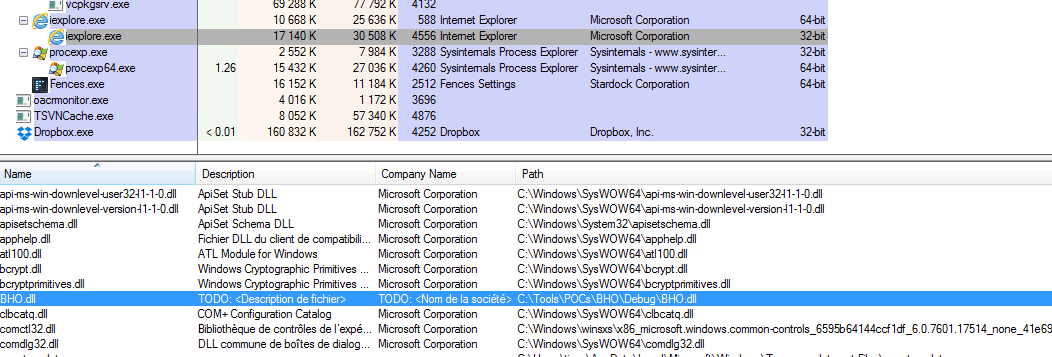
The DLL is indeed loaded in Internet Explorer:
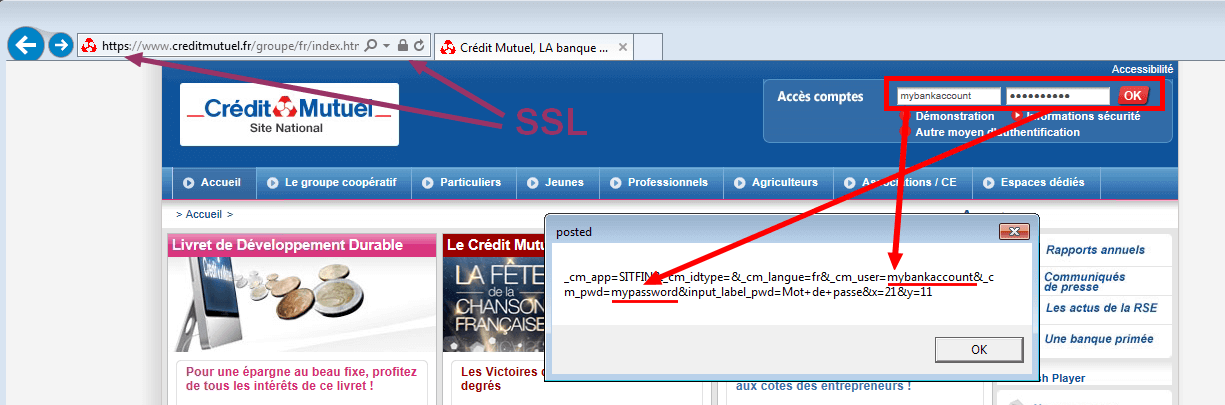
Credit Mutuel (French Bank), with SSL turned on:
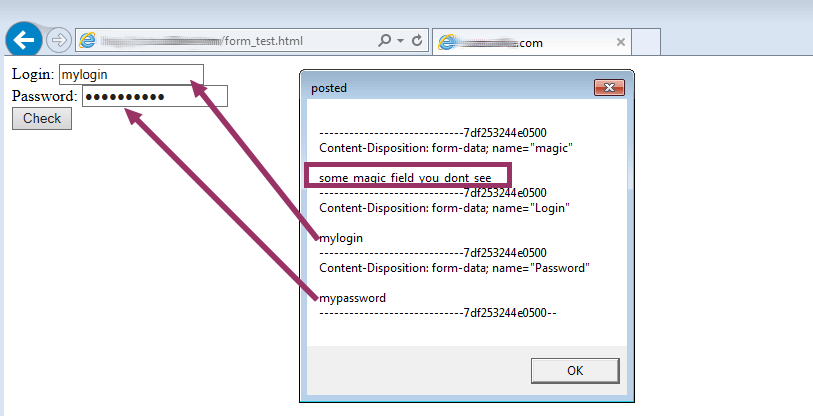
Some custom form in HTML, containing a hidden “magic field”:
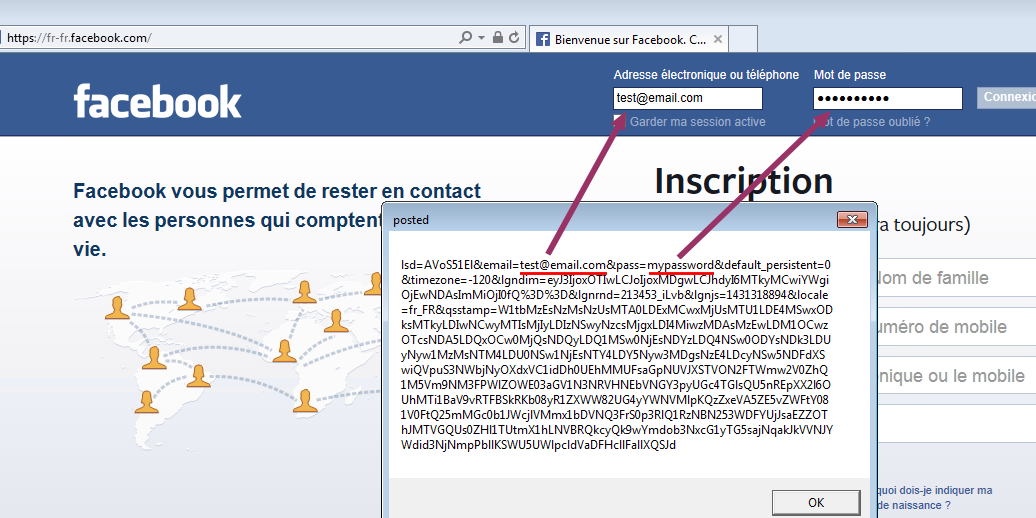
Facebook:
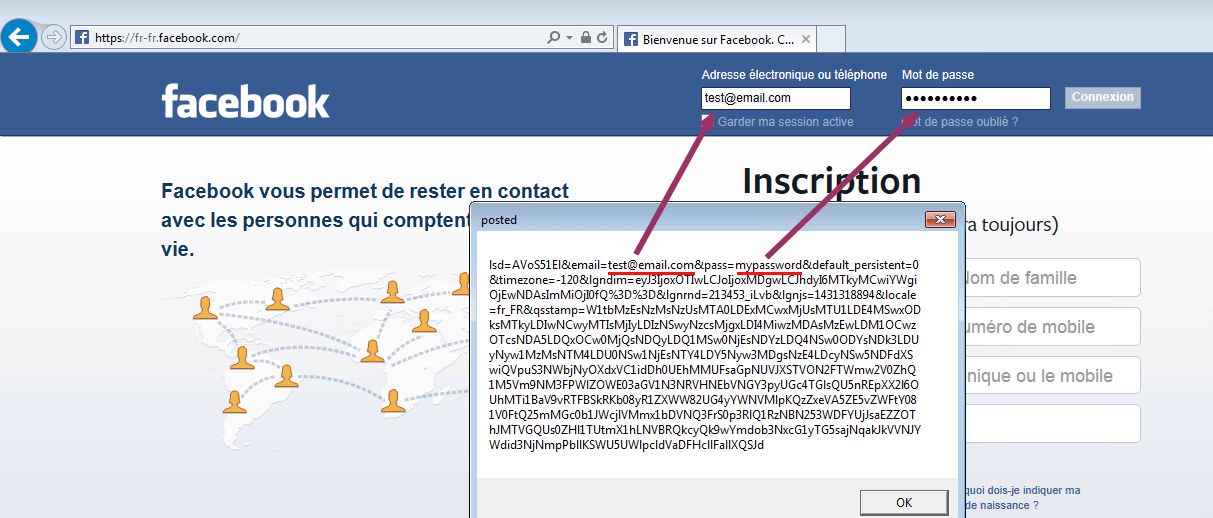
Conclusion
I’ve tried a few secure login pages, from some banks, and social networks. I found only one that was able to bypass this: Paypal, because they probably use a ajax login (?). Anyway it didn’t hit the BeforeNavigate2 routine. For the others, even with SSL turned on, we are able to see the clear text that is posted back to the web server.
All of this was to demonstrate that any random web browser extension can access your personal data, and very classified credentials. So please, pay attention to what you install (in general) but especially in your web browser. And don’t think you’re safe because you’re seeing the “encryption symbol”. Malicious extensions have been found to be redirecting users, stealing credentials, modifying web pages on-the-fly to request credentials (HTML injection), opening ads, … There’s no limit.
Don’t feel safe, you’re not.