Founder and owner of Adlice Software, Tigzy started as lead developer on the popular Anti-malware called RogueKiller. Involved in all the Adlice projects as lead developer, Tigzy is also doing research and reverse engineering as well as writing blog posts.
Adware (ad-ware) are a quite recent thread, compared of the others. They begin to rise in popularity with the decline of the shareware license model. Instead of offering trial version of the software they developed, software writers began to include ads in their installers
Computer viruses were the first kind of malware that were developed. At the beginning, they were not malicious per se (the first computer virus “Creeper”, developed in 1970 only displayed a message), but soon after malicious ones begin to appear and counter-measures known as “anti-virus” software were developed.
With the development of broadband Internet connections, online/cloud-based services have become more and more numerous. Your data is not only located on your computer anymore but on a multitude of online servers. Not only you now should consider what could happen if your computer gets infected, but you must also consider what could happen if one of your online accounts gets compromised.
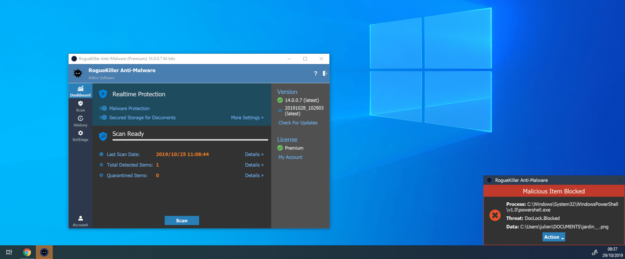
We are pleased to announce our flagship, RogueKiller Anti-malware, is finally available for version 14 BETA testing. Version 14 is a very big milestone for us because it introduces a major new feature that customers have been asking us for a long time: Real Time Protection. Let’s take a look. Real Time Protection RogueKiller 14…
We are proud to present you today a new software (or rather a new variant of an existing software) that was many times requested by our customers, UCheckCMD. Test it now !
We are proud to announce that our popular Anti-maware RogueKiller new version, that we’ve been working on hardly for the past year, has been released ! Test it now.
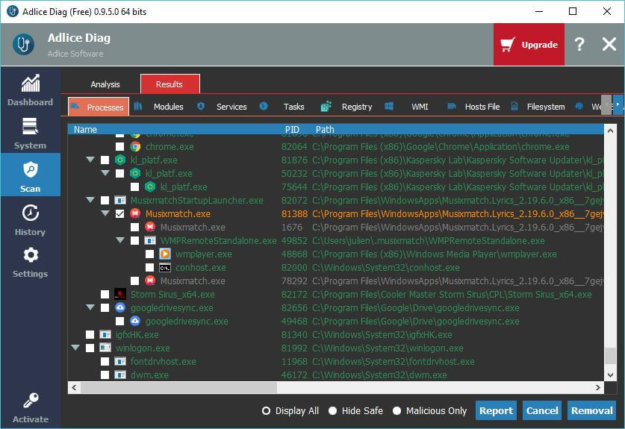
We are proud to announce that our new project, that we’ve been working on hardly for the past year, has been released ! It is called Adlice Diag, and it will be your favorite software when it comes to diagnose a machine’s health…
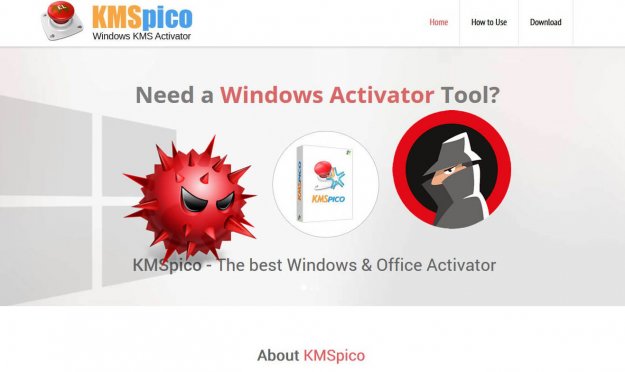
Infections related to the use of hacktools like Windows Loader or KMSPico are rising. Learn how malware authors use them to spread cryptominers, ransomwares and ultimately take control of your newly installed operating system.
Alpha bay, Silk Road, Hansa: They made the headlines of newspapers for weeks. They were underground markets offering several illicit goods and services and were shut down in 2013 and 2017. All were using Tor, currently the most used parallel Internet network, called Darknet. DARKNET Computers connected to the Internet use the Internet protocol suite…
A major increase in the number of malware featuring cryptominers has been observed. Discover the way malware writers make money with them.