Analysis
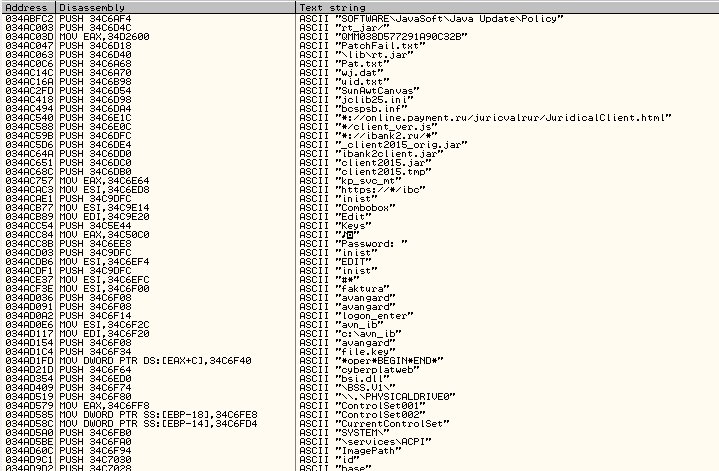
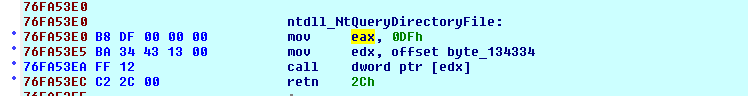
Carberp is a Zbot/Zeus clone that uses userland code injection to protect its files, and to steal banking information into your web browsers. To keep persistence, it has an executable file, hidden in the startup folder. Carberp hooks ntdll.dll into some processes, detouring API calls to its filter functions.
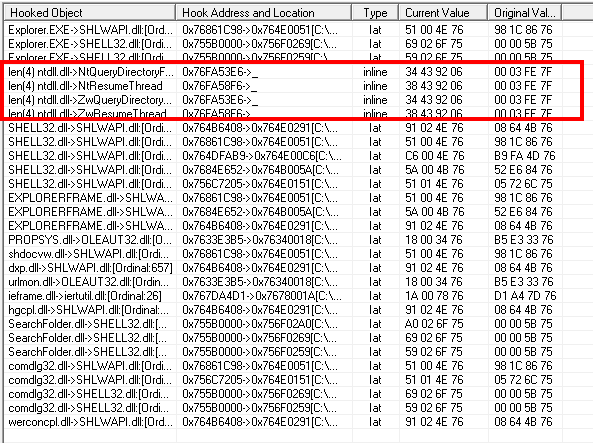
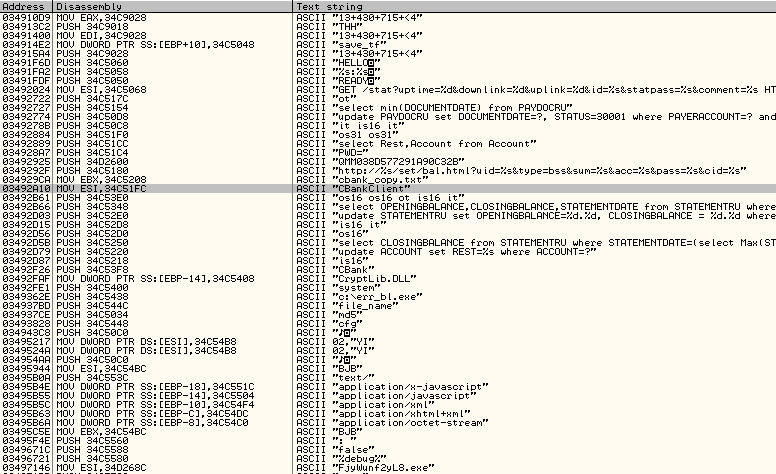
When we look at the text strings, we can find many information related to HTTP injection, and to bank websites.
Removal
Scan your computer with RogueKiller and remove registry keys and files. Please look at the demo video.
Your reports should look like this (with your own language text) :
Removal
¤¤¤ Processus malicieux : 3 ¤¤¤
[SVCHOST] svchost.exe -- C:\Windows\System32\svchost.exe [-] -> TUÉ [TermProc]
[SVCHOST] svchost.exe -- C:\Windows\System32\svchost.exe [-] -> TUÉ [TermProc]
[SVCHOST] svchost.exe -- C:\Windows\System32\svchost.exe [-] -> TUÉ [TermProc]
¤¤¤ Entrees de registre : 2 ¤¤¤
[HJ DESK][PUM] HKLM\[...]\NewStartPanel : {59031a47-3f72-44a7-89c5-5595fe6b30ee} (1) -> REMPLACÉ (0)
[HJ DESK][PUM] HKLM\[...]\NewStartPanel : {20D04FE0-3AEA-1069-A2D8-08002B30309D} (1) -> REMPLACÉ (0)
¤¤¤ Tâches planifiées : 0 ¤¤¤
¤¤¤ Entrées Startup : 1 ¤¤¤
[FuckSirefef][Root.Zbot] FjyWunf2yL8.exe : C:\Users\FuckSirefef\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\FjyWunf2yL8.exe [-] -> SUPPRIMÉ AU REBOOT
¤¤¤ Navigateurs web : 0 ¤¤¤
¤¤¤ Fichiers / Dossiers particuliers: ¤¤¤
¤¤¤ Driver : [CHARGE] ¤¤¤
[Address] IAT @explorer.exe (GetUserNameExW) : Secur32.dll -> HOOKED (C:\Windows\system32\SSPICLI.DLL @ 0x74F929FC)
[Inline][Rootkit!] EAT @explorer.exe (NtQueryDirectoryFile) : ntdll.dll -> HOOKED (Unknown @ 0x06904E64)
[Inline][Rootkit!] EAT @explorer.exe (ZwQueryDirectoryFile) : ntdll.dll -> HOOKED (Unknown @ 0x06904E64)
[Inline] EAT @explorer.exe (?s_pClassInfo@CCRadioButton@DirectUI@@0PAUIClassInfo@2@A) : DUI70.dll -> HOOKED (Unknown @ 0x7BD1A399)
[Inline] EAT @explorer.exe (?s_pClassInfo@Macro@DirectUI@@0PAUIClassInfo@2@A) : DUI70.dll -> HOOKED (Unknown @ 0x6BD1A378)
[Inline][Rootkit!] EAT @firefox.exe (NtClose) : ntdll.dll -> HOOKED (Unknown @ 0x00103EE7)
[Inline][Rootkit!] EAT @firefox.exe (NtDeviceIoControlFile) : ntdll.dll -> HOOKED (Unknown @ 0x0010406D)
[Inline][Rootkit!] EAT @firefox.exe (NtQueryDirectoryFile) : ntdll.dll -> HOOKED (Unknown @ 0x00114E64)
[Inline][Rootkit!] EAT @firefox.exe (ZwClose) : ntdll.dll -> HOOKED (Unknown @ 0x00103EE7)
[Inline][Rootkit!] EAT @firefox.exe (ZwDeviceIoControlFile) : ntdll.dll -> HOOKED (Unknown @ 0x0010406D)
[Inline][Rootkit!] EAT @firefox.exe (ZwQueryDirectoryFile) : ntdll.dll -> HOOKED (Unknown @ 0x00114E64)
[Inline] EAT @firefox.exe (GetWindowInfo) : USER32.dll -> HOOKED (C:\Program Files\Mozilla Firefox\xul.dll @ 0x6801E25A)
[Inline] EAT @firefox.exe (_wpgmptr) : MSVCR100.dll -> HOOKED (Unknown @ 0x183B0670)
¤¤¤ Ruches Externes: ¤¤¤
¤¤¤ Infection : Root.Zbot ¤¤¤